Introduction
This report reviews the most significant crypto security incidents observed in January 2026, examining where losses occurred, who was targeted, and how attackers gained access. It covers a range of events, from smart contract exploits and cross-chain failures to phishing, social engineering, and private key compromise, highlighting both technical and human-driven attack vectors.
Beyond documenting individual incidents, the report analyses broader patterns across the month, including the types of entities most frequently targeted, the attack methods responsible for the largest losses, and how stolen funds were moved once access was obtained. Together, these findings provide a snapshot of the evolving risk landscape, showing how attackers are increasingly shifting focus away from code-level vulnerabilities toward exploiting authorisation, trust, and operational access within the crypto ecosystem.
TL;DR : NOMINIS January 2026 Key Findings
- ~$385M lost across major crypto incidents in January 2026
- One private-user attack ($282M) accounted for nearly 75% of total losses
- Private individuals were the most frequently targeted, primarily via phishing and social engineering
- Phishing, malicious signatures, and approval abuse caused more damage than smart contract exploits
- Smart contract vulnerabilities were common but less financially severe, typically resulting in mid seven-figure losses
- Privileged access failures (developer keys, treasury wallets) remain a high-impact risk
- Cold storage and hardware wallets did not prevent loss when authorisation was compromised
- The dominant trend: authorisation abuse has become the primary attack surface in crypto
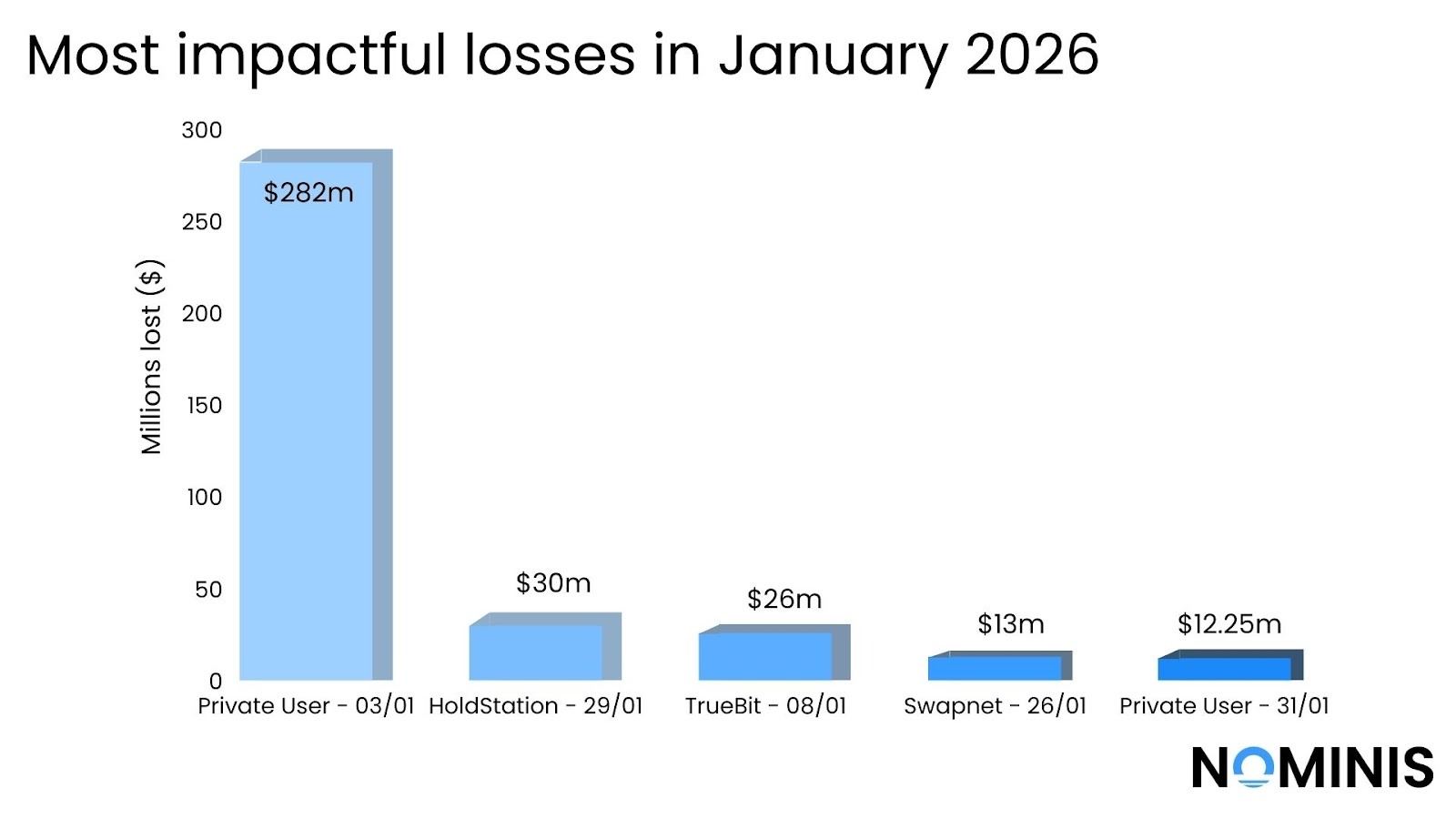
Major Crypto Attacks in January 2026
Private User - 03/01/2026
Type: Phishing Attack
At the beginning of the month, a private user suffered a significant loss when they signed a malicious permit signature, granting a third party authorization to transfer their $aEthLBTC from their wallet without requiring an on-chain approval transaction. This permit, once signed, allowed the attacker to later execute token transfers directly from the victim’s wallet, resulting in the theft of over a million dollars. No protocol vulnerability was exploited; the transfer was executed using a valid authorization provided by the user.
Impact: $1,080,000
TMX - 06/01/2026
Type: Smart Contract Exploit
Several days later, a contract associated with the exchange TMX on Arbitrum was exploited, resulting in almost one and a half million worth of assets being drained by an attacker.
The loss included tokens such as USDT, wrapped SOL, and WETH. The attacker leveraged a vulnerability in the exchange’s contract logic to execute unauthorized transfers, effectively bypassing intended safety checks and allowing systematic removal of funds from TMX’s liquidity.
Impact: $1,400,000
Private User - 06/01/2026
Type: Phishing Attack
On the same day, a different wallet owner fell for a similar phishing attack as seen at the beginning of the month. A victim lost just shy of $300,000 in $aEthLBTC when they mistakenly signed off permission for a third party to move funds from their wallet. In each case, the stolen funds were sent to different wallets, however the attackers appeared to use the same technique. In this case, the victim lost significantly less than the first victim.
Impact: $229,951.00
TrueBit - 08/01/2026
Type: Smart Contract Exploitation
A couple of days later, the Truebit protocol on Ethereum was exploited for an estimated over $25 million when an attacker abused a flaw in its TRU minting smart contract.
Due to a mathematical vulnerability in the pricing logic, a function that should calculate how much ETH was needed to mint TRU tokens instead returned nearly zero in certain conditions, allowing the attacker to mint large quantities of TRU at almost no cost and then sell or burn those tokens to extract ETH from the protocol’s reserves. The attacker repeated this mint-and-sell cycle, draining about 8,535 ETH before moving the funds.
Impact: $26,600,000
Private User - 10/01/2026
Type: Social Engineering Attack
Days later, the month’s largest attack took place, when a user suffered a loss of over $250 million due to a hardware wallet social engineering attack. The attacker stole LTC and BTC, converted the stolen funds to privacy coin Monero via multiple instant exchanges, which ultimately caused the Monero price to sharply spike.
Impact: $282 million
Synap Logic - 19/01/2026
Type: Smart Contract Vulnerability
Later in the month, DeFi protocol Synap Logic experienced an exploit after a flaw in the smart contract was manipulated. The swapExactTokensForETHSupportingFeeOnTransferTOkens() function lacked proper parameter checks, which allowed attackers to abuse the contract’s logic and extract excess native tokens while also receiving newly minted SYP tokens. This vulnerability enabled unauthorized withdrawals of approximately $186,000 in losses.
Impact: $186,000
Private User - 20/01/2026
Type: Phishing Attack
A day later, a wallet owner suffered a hack when the victim signed multiple phishing signatures, giving the attacker the authority to move funds. Examples of these signatures may be through a malicious dApp, or spoofed interface, that prompts a user ‘sign to continue’, ‘verify ownership’ or ‘confirm access’ while in reality authorizing token approvals or direct transfer permissions. The attacker was able to drain millions of dollars worth of SLVon and XAUt from the wallet.
Impact: $3,020,000
MakinaFi - 20/01/2026
Type: Logic Flaw
On the same day, MakinaFi, a DeFi protocol, experienced an ethereum-based exploit after an attacker manipulated how LP token value is asserted. The root cause was that DUSDUSDC.getSharePrice() relied on the pool’s spot price, rather than a time weighted manipulation resistant price. By temporarily skewing the pool price, the attacker artificially inflated the perceived value of the LP position and then exploited this distortion to execute a profitable arbitrage, extracting USDC from the protocol.
Impact: $4,100,000
SagaEVM - 21/01/2026
Type: Smart Contract Vulnerability
Saga, a Layer-1 blockchain protocol, suspended SagaEVM when it suffered a cross-chain bridge logic failure. The attacker abused how bridged assets and messages were validated on SagaEVM. By manipulating the bridge and associated contracts, the attacker was able to illegitimately mint or withdraw bridged assets and move them onto Ethereum, draining assets and causing Saga’s stablecoin to depeg.
Impact: $7 million
Aperture Finance - 26/01/2026
Type: Contract Vulnerability
Aperture Finance, a DeFi liquidity management protocol, suffered an exploit when attackers abused a flaw in its closed-source smart contracts that allowed arbitrary external calls due to insufficient input validation. By leveraging this weakness, the attacker misused existing token approvals to trigger unauthorised transferFrom() operations, draining assets from the protocol across multiple chains, including Ethereum, Arbitrum, Base, and BNB Chain.
Impact: $3,670,000
Swapnet - 26/01/2026
Type: Smart Contract Vulnerability
Similarly to Aperture Finance, Swapnet suffered a smart contract exploit on the same day, caused by an arbitrary call vulnerability in its closed-source code that lacked proper input validation and safeguards. This flaw allowed an attacker to craft malicious calls that bypassed intended logic, enabling unauthorized use of existing token approvals to execute transferFrom() operations and drain assets from the protocol across multiple chains much like above.
Impact: $13 million
holdstationW - 29/01/2026
Type: Private Key Compromise
Holdstation, a DeFi platform, suffered a smart contract vulnerability via a private key compromise, when a core developer’s device was compromised through a malicious coding/ browser IDE extension that had been widely downloaded. This compromise exposed an admin private key, allowing the attacker to impersonate a legitimate administrator rather than exploit any flaw in the smart contracts themselves.
Using this access, the attacker deployed a malicious contract and executed an unauthorized upgrade of the Vault Proxy for Holdstation’s Perp DEX, first on World Chain and then on BNB Chain, altering the vault logic to enable fund extraction. Approximately 22 ETH (~$66,000) was successfully drained on World Chain, while around $126,000 on BNB Chain remains in the vault and is subject to whitehat negotiation.
Impact: $100,000
Step Finance - 30/01/2026
Type: (Suspected) Private Key Compromise
Step Finance, a solana-based DeFi analytics platform suffered a major security breach towards the end of January, when attackers compromised several of its treasury and fee wallets, enabling them to un-stake and transfer approximately 261,854 SOL (around $27–$30 million) to unknown addresses in a short time window. On-chain activity suggests the attacker had direct wallet permissions rather than exploiting a smart contract bug, and while user funds were reportedly unaffected, the incident triggered a sharp crash in the project’s native STEP token and renewed concerns about treasury security in the Solana DeFi ecosystem, with investigations and forensic analysis still underway.
Impact: $30 million
Private User- 31/01/2026
Type: Contaminated transfer history
On the last day of the month, a private user lost 4,556 ETH after falling for a transaction history poisoning scam. The attackers exploited the wallet transfer history, first sending a small ‘dust’ transaction from an address looking deliberately similar to the legitimate one. This make the fake address appear in the victim’s transaction history, who then copied the fake address believing it was the correct one, given it was in the history, and unknowingly sent funds to the attacker who controlled the lookalike address.
Impact: $12,250,000
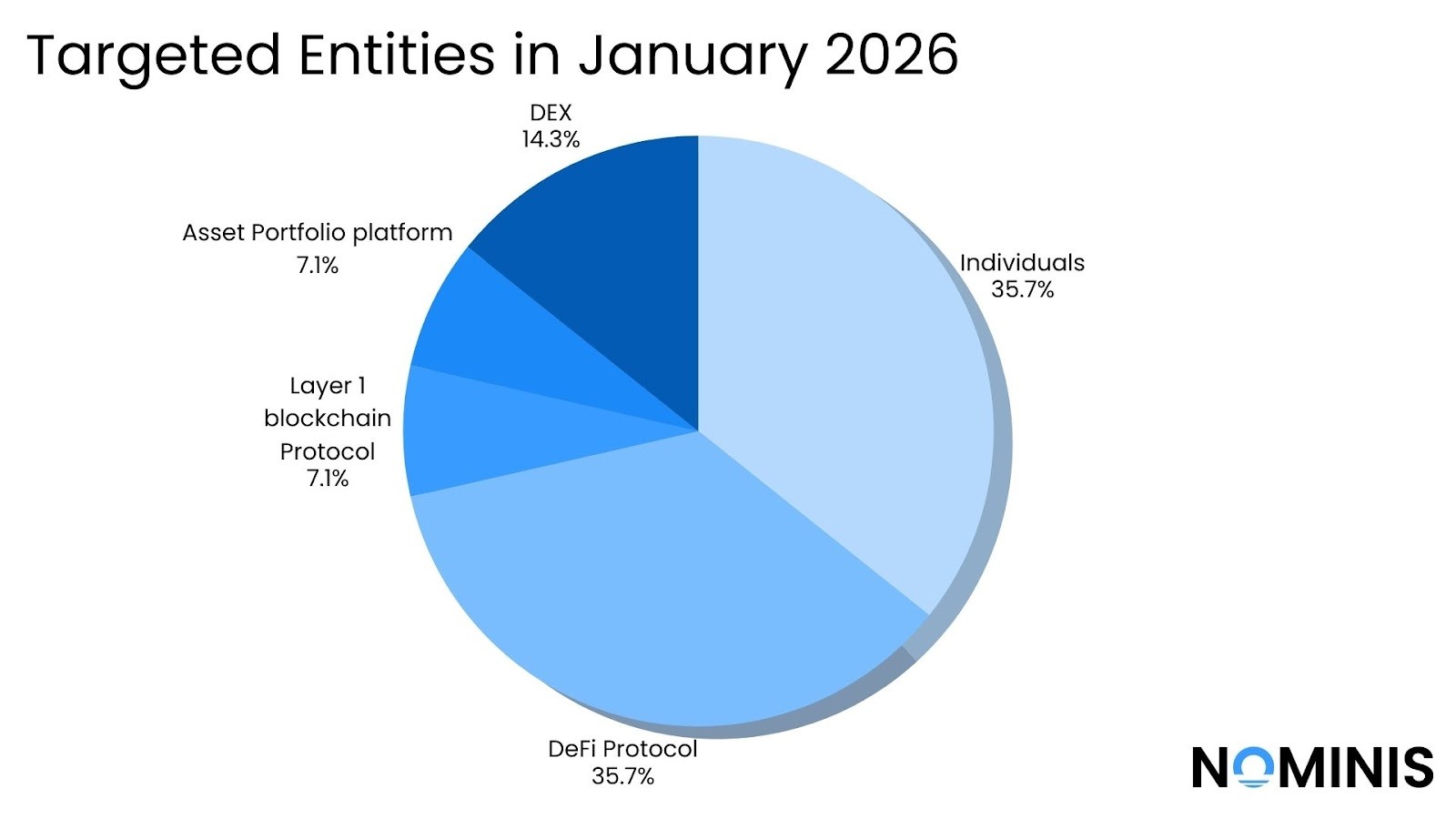
Significant events in January 2026
January 2026 was a sharp reminder that crypto risk isn’t just about smart contracts, it’s just as often about people. As discussed above, early in the month, a single whale lost $282 million in Bitcoin and Litecoin after being socially engineered into compromising a hardware wallet. Despite using cold storage, the victim was tricked into signing malicious actions, allowing the attacker to drain funds and rapidly launder them through cross-chain swaps and privacy infrastructure.
This month also saw strong concerns from security firm SlowMist , who warned of a new MetaMask phishing campaign masquerading as a fake “2FA upgrade.” The scam relied on cloned interfaces and urgent messaging to extract seed phrases, highlighting how wallet-targeted social engineering continues to evolve as attackers adapt to more security-aware users.
On the investigative side, on-chain researchers exposed activity linked to a figure known as “Lick,” associated with tens of millions of dollars in suspicious crypto flows. The case reignited debate around insider risk, custody controls, and the limits of on-chain transparency when privileged access is involved.
Beyond crime and scams, geopolitics also surfaced on-chain. In a notable move, Iran’s largest crypto exchange staked $10 million in Ethereum, signalling how sanctioned or high-risk jurisdictions are increasingly embedding themselves deeper into core blockchain infrastructure as global financial pressure intensifies.
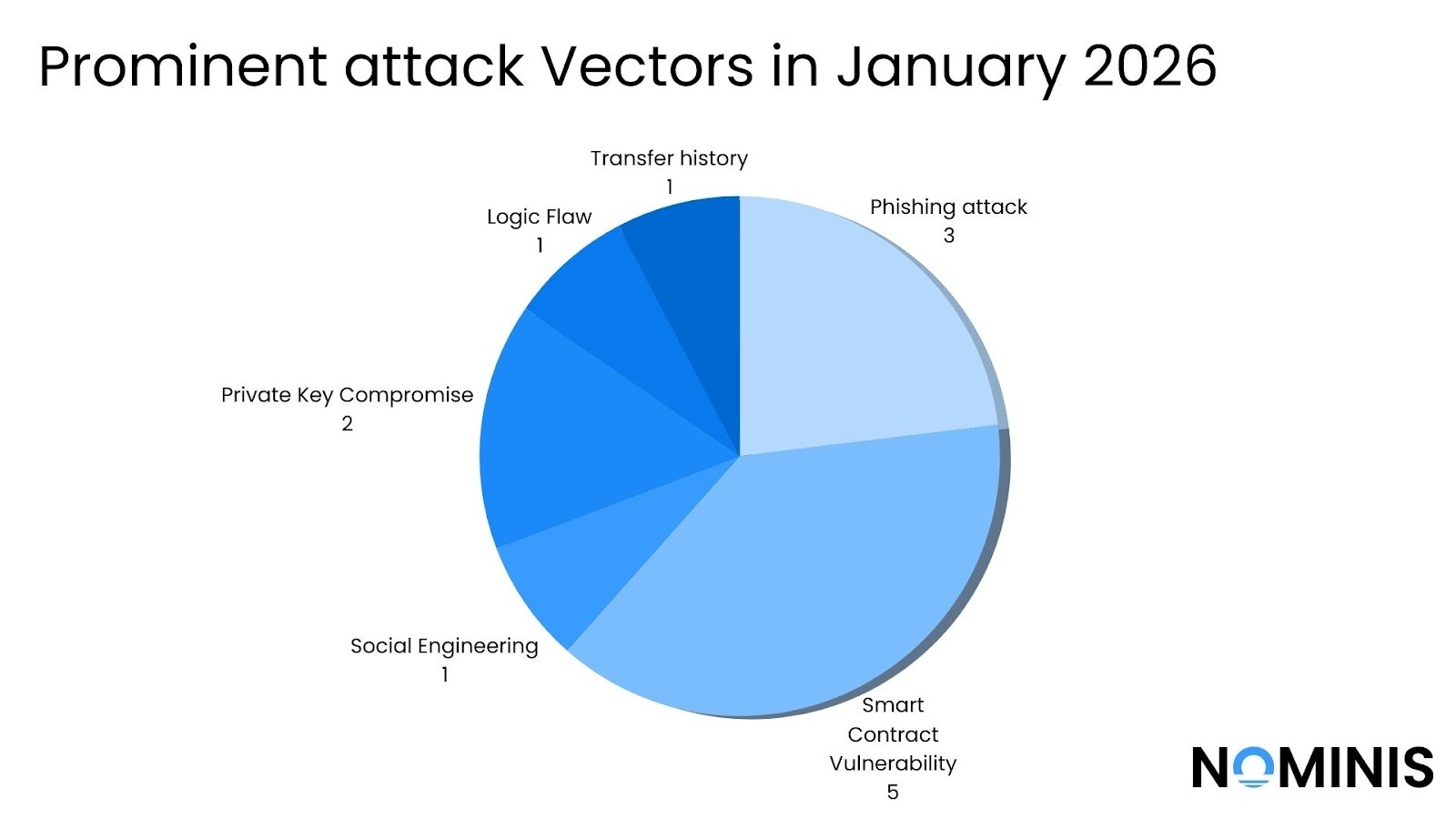
NOMINIS Unique Findings:
NOMINIS began 2026 sharing significant investigative findings that span both illicit finance and emerging compliance challenges in the crypto ecosystem.
Early in the year, NOMINIS uncovered a wave of copycat bomb threat emails targeting U.S. synagogues that demanded Bitcoin payments, revealing how threat actors are leveraging cryptocurrency extortion at scale and exploiting community institutions.
In a major counter-terror finance development, NOMINIS exposed extensive crypto laundering operations by Iran’s Islamic Revolutionary Guard Corps (IRGC) through London-based exchanges Zedcex and Zedxion, tracing millions in illicit flows and highlighting gaps in exchange controls. This research contributed to the U.S. Department of the Treasury’s designation of both Zedcex and Zedxion as Specially Designated Global Terrorist (SDGT) entities, a landmark enforcement action in the blockchain era.
NOMINIS also reported that Iran’s largest exchange staked $10 million in Ethereum, a strategic move reflecting how state-linked actors continue deep participation in major blockchain networks amid escalating geopolitical tensions with the United States.
From a broader analytical perspective, NOMINIS found that illicit actors are 12× more likely to use crypto exchanges located in low-risk jurisdictions, as defined by the FATF, compared to high-risk counterparts. This insight highlights how illicit actors exploit perceived regulatory blind spots, emphasizing the need for consistent risk-based compliance worldwide.
Beyond investigative research, NOMINIS hosted a webinar this month, with CryptoSwift on the importance of intelligence-driven compliance. CEO Snir Levi discussed the critical role of accurate attribution when performing Travel Rule compliance. The session brought together practitioners and regulators to discuss real-world challenges and the role of on-chain analytics in meeting both regulatory expectations and operational needs.
Concluding Insights:
January 2026 was a stark reminder that crypto risk is no longer dominated by broken code alone. While smart contract exploits continued to surface throughout the month, the most damaging losses did not come from technical failures, but instead, users and actors with privileged access being tricked, compromised, or misled.
In total, January’s major incidents resulted in approximately $385 million in losses. What stands out immediately is how unevenly that damage was distributed. A single event, the $282 million loss suffered by a private user, accounted for nearly three quarters of all losses recorded during the month. No protocol failure, bridge exploit, or smart contract vulnerability exploit came close in scale.
Private individuals were also the most frequently targeted group, appearing in almost half of the major incidents. These attacks largely relied on phishing, malicious signatures, and social engineering rather than technical vulnerabilities. In several cases, victims unknowingly signed permits or approvals that granted attackers legitimate authority to move funds. We may see more representation of losses of individual wallets, due to the increasingly normalisation to publicly report such looses. Previously private wallets may have experienced losses, but did not report the incident or amount lost.
Despite using a hardware wallet and cold storage, the most serious victim was socially engineered into signing malicious actions, enabling the attacker to drain BTC and LTC and rapidly launder the funds through instant exchanges and privacy infrastructure.
Smart contract vulnerabilities remained a persistent background threat, particularly across DeFi protocols. Logic flaws, pricing calculation errors, unchecked parameters, and arbitrary call vulnerabilities accounted for multiple seven-figure losses. While these incidents were more frequent, their aggregate impact was significantly smaller than losses caused by user-targeted attacks.
Privileged access abuse also emerged as a recurring concern. Incidents involving compromised developer environments and treasury wallets showed how a single exposed private key can override every other security control. In these cases, attackers did not exploit the protocol’s logic. They operated it with legitimate permissions until funds were gone.
Taken together, January’s events highlight a clear shift in where the greatest damage occurs. The industry has made meaningful progress hardening smart contracts, but attackers are increasingly bypassing code altogether. They are targeting trust, routine user behavior, and operational access, areas that are harder to audit and easier to exploit.
January 2026 did not introduce new attack categories. What it did expose is the true concentration of risk. When nearly $385 million can be lost in a single month, and most of it from one compromised user, the conclusion that can be drawn is clear; in today’s crypto ecosystem, authorisation is the primary attack surface, and human error remains the most expensive vulnerability of all.






