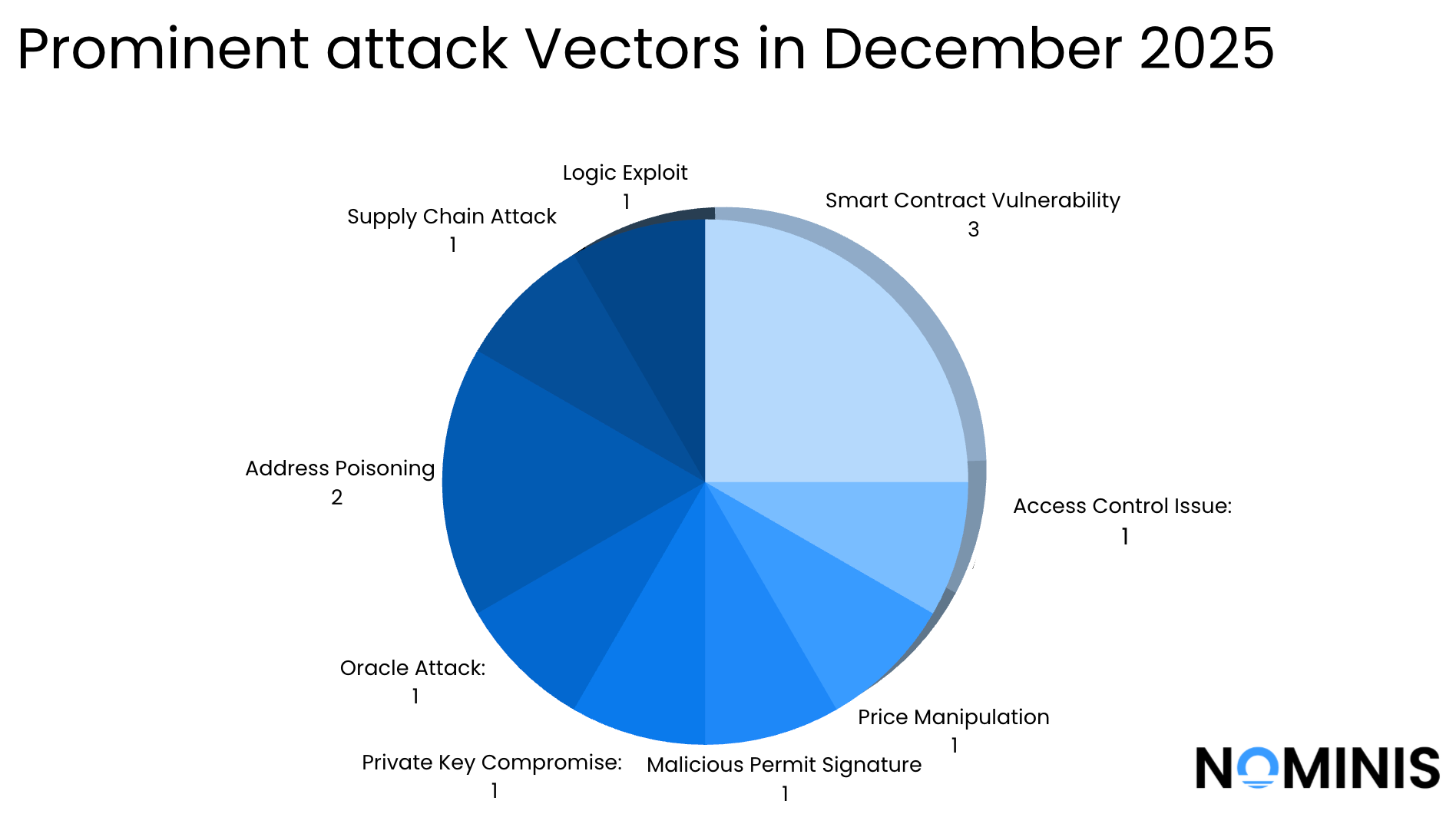
December 2025 closed the year with one of the most damaging and instructive months for crypto security, fraud, and illicit finance. Across a broad spectrum of incidents, ranging from smart contract exploits and oracle manipulation to private key compromise and supply-chain attacks, attackers extracted over $99 million in confirmed losses during the month.
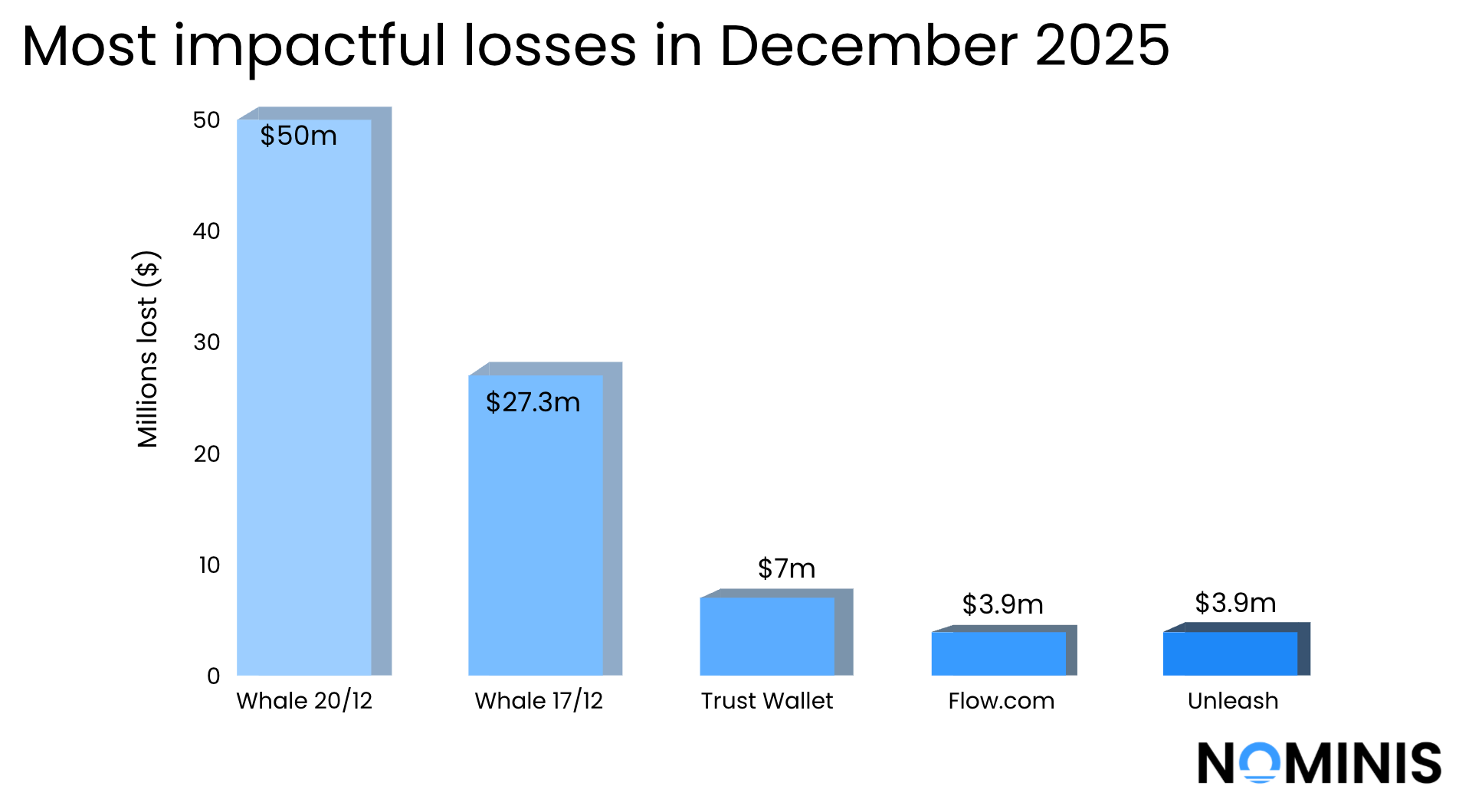
Most notably, December saw one of the largest address poisoning scams ever detected, in which a single user lost approximately $50 million in USDT after falling victim to a transaction-history contamination attack. This incident alone accounted for roughly half of the month’s total losses and marked a turning point in the scale and sophistication of user-targeted scams.
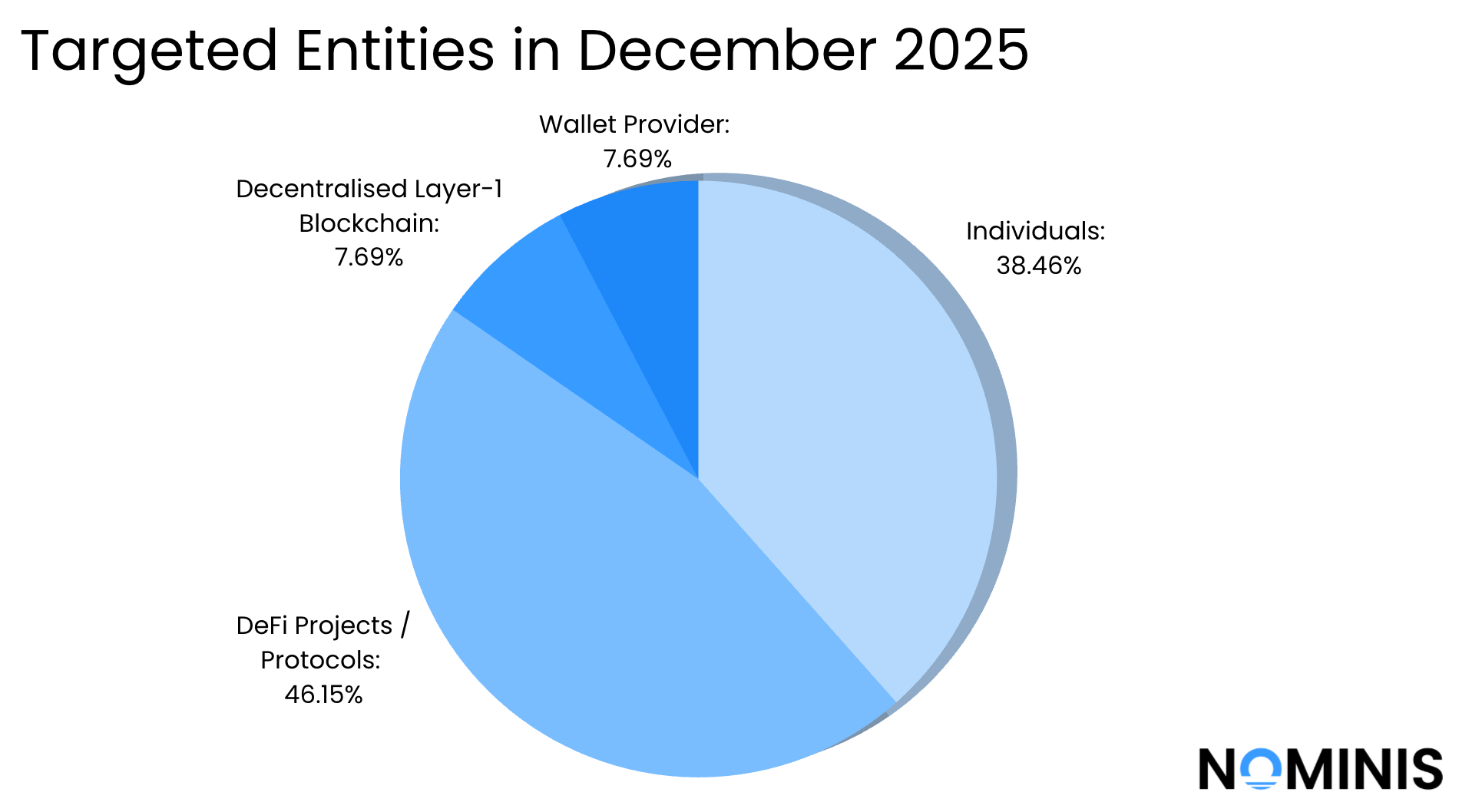
Beyond this landmark case, December also featured major protocol-level exploits, including attacks against Aevo, USPD, Rari Capital, Trust Wallet, and Flow, alongside a growing number of high-value private wallet compromises. Together, these events underscore a critical reality: while smart contract risk remains significant, human-layer exploitation, wallet hygiene failures, and infrastructure weaknesses are increasingly driving the largest financial losses in crypto.
Major Crypto Attacks in December 2025
Private Goldfinch User - 02/12/2025
Type: Smart Contract Exploit
Early in the month, a user of the Ethereum-based DeFi lending protocol Goldfinch Finance, known as deltatiger.eth, suffered losses after an attacker exploited a vulnerability in the smart contract. The flaw resided in the contracts collectInterestRepayment() function, which allowed USDC to be transferred from any wallet that had previously granted approval, enabling the attacker to manipulate the contract’s share price by depositing a small amount of USDC and repeatedly withdrawing funds. After the exploit, the attacker converted some of the stolen funds in to ETH and deposited about 118 ETH into Tornado Cash, in an attempt to obscure the trail of funds.
Impact: $330,000
USPD.io - 05/12/2025
Type: Access Control Issue
Several days later, USPD, an Ethereum-based USD-pegged stablecoin system that issues the USPD token, suffered a critical exploit. An attacker leveraged a sophisticated proxy-based attack known as CPIMP (Clandestine Proxy In the Middle of Proxy) to gain access of the system, mint approximately 98 million USPD tokens and, and steal around 232 stETH from protocol liquidity. According to USPD, the exploit did not stem from a flaw in the audited smart contract logic but from a deployment-time compromise on September 16, when the attacker front-ran the proxy initialisation via Multicall3 transaction and silently seized admin privileges. By installing a shadow implementation that forwarded calls to the legitimate, audited code while manipulating event payloads and storage slots, the attacker evaded detection by verification tools and block explorers for months before upgrading the proxy and executing the drain. UPSD urged users to revoke approvals immediately, warned against purchasing USPD, and stated that it is coordinated with law enforcement exchanges, and whitehat security groups to contain the incident.
Impact: $1,000,000.00
Aevo fka Ribbon Finance - 13/12/2025
Type: Smart Contract Vulnerability
In mid December, Aevo, formerly Ribbon Finance, suffered a sizable exploit of its legacy smart contracts after a recent oracle update introduced vulnerabilities in access control and decimal precision. The update changed price feeds to support 18-decimal assets while older assets still used 8 decimals, creating a mismatch. A flaw in the proxy-based oracle stack deployed a malicious contract to create options with artificially low strike prices across mismatched decimal assets. By exploiting the decimal inconsistency and weak access control, the attacker minted large numbers of options and drained funds from the protocol’s vaults.
Impact: $2,700,000.00
Private User - 13/12/2025
Type: Suspected Access Issue
On the same day, a private wallet owner on the BNB Chain appeared to have suffered a targeted attack, where the entire contents of the wallet was emptied. The stolen funds were allegedly swapped on the Ethereum network. According to a post on X, the attacker withdrew 300 ETH from Tornado Cash before the hack took place.
Impact: $700,000
YearnFinanceV1 - 16/12/2025
Type: Price Manipulation
Several days later, Yield Finance, a decentralised protocol suffered an exploit resulting in a loss. The exploiter appeared to swap the stolen funds for 103 ETH. This follows an additional hack Yearn suffered at the end of last month, when an attacker targeted the legacy ‘yETH’ pool; in last month’s case, the attacker exploited a flaw in the contact logic to mint fake tokens, stealing $9 million, with Yearn recovering $2.4 million.
Impact: $300,000.00
Private User - 16/12/2025
Type: Access Control Issue
The same day, an individual lost over half a million dollars after signing a malicious permit signature. It is believed that the victim experienced a phishing attack, leading them to sign to signature.
Impact: $563,590.00
Whale - 17/12/2025
Type: Private Key Compromise
The following day, a crypto Whale’s Gnosis Safe multisig wallet suffered a significant drain. The wallet had been configured as a 1 of 1 multisig meaning a single key controlled the funds, which allowed the attacker to take full control. About 4,100 ETH of the stolen assets were laundered through Tornado Cash in 100 ETH increments. The attacker still controls the wallet, which maintains an active leveraged long position on Aave collateralized with approximately $25 million in ETH, posing a potential risk of further losses market condition shift.
Impact: $27,300,000.00
RariCapital - 18/12/2025
Type: Smart Contract Vulnerability
RariCapital, who allegedly ceased operations following sizable hacks in 2021 and 2022, appears to have experienced a hack. Investigators identified a series of on-chain transactions where the attacker repeatedly interacted with the Rari Capital Protocol to execute multiple borrowing operations, without posting any collateral. A preliminary investigation determined the exploit was enabled by the hijacking of a vulnerable implementation contract, which the attacker controlled at the time of execution, allowing them to bypass normal protocol safeguards. The attacker was able to extract profit via the unauthorized control.
Impact: $2,000,000.00
Private User - 20/12/2025
Type: Address Poisoning
In mid December, a private user experienced a large-scale address poisoning scam resulting in the theft of approximately $50 million in USDT, after they mistakenly sent funds to a scammer-controlled address that closely resembled a legitimate destination. The victim first withdrew about $50 million in USDT from Binance and sent a small test transfer of $50 USDT to verify the recipient address. Shortly after, a scammer poisoned the transaction history by sending a similar looking address to the victim, and just over 12 minutes later, the victim accidentally transferred the full $50 million to ETH, with most of the proceeds ultimately deposited into Tornado Cash, marking the incident as one of the largest address poisoning scams ever detected.
Impact: $50,000,000
Private User - 22/12/2025
Type: Address Poisoning
Just two days later, another user fell victim to an address poisoning scam, after copying a wallet address from their transaction history that had been contaminated by a scammer. The attacker sent a small transaction from an address designed to closely resemble a legitimate one of the victims had previously interacted with, causing it to appear in the wallet’s recent transfers.
When the victim later copied the address from their history to make a new transfer, they unknowingly sent the funds to the scammer-controlled address instead of the intended recipient. As with larger address poisoning cases, the loss occurred due to human error rather than a protocol vulnerability, highlighting how deceptive address look-alikes can lead to significant financial losses.
Impact: $81,000.00
Trust Wallet - 25/12/2025
Type: Compromised Supply Chain attack
On Christmas Day, Trust Wallet suffered a supply-chain security incident affecting its official Chrome browser extension. It appears that attackers obtained a leaked API key used in the extension’s build or update pipeline. A compromised update (version 2.68) was distributed through the legitimate Chrome Web Store. The malicious code embedded in this update enabled attackers to exfiltrate users’ recovery phrases, allowing full wallet takeovers rather than isolated transaction fraud. As a result, attackers were able to rapidly drain affected wallets and move the stolen funds across chains, often through instant swap services and exchanges, consistent with common post-theft laundering patterns.
Impact: $7,000,000
Flow.com - 27/12/2025
Type: Logic Exploit
Towards the end of December, the Flow Foundation experienced a protocol-level execution logic exploit in which an attacker abused a vulnerability in the execution layer to move approximately $3.9 million in assets off-network before validators coordinated a full network halt. The incident did not compromise user balances or deposits, as the flaw did not involve application smart contracts or custody logic. The stolen funds were primarily bridged out via cross-chain services such as Celer, Debridge, Relay and Stargate, and then routed into liquidity and swap protocols as part of active laundering attempts.
Impact: $3.9 million
Unleash Protocol - 30/12/2025
Type: Oracle Attack
On the second to last day of 2025, Unleash Protocol experienced an oracle driven economic exploit in which an attacker abused collateral price distortions to extract value from the protocol. During a short time window, the prices of certain collateral assets collapsed by more than 80%, triggering forced liquidations and enabling the attacker to profit from artificially under-collateralised positions. The incident did not stem from a smart contract code vulnerability, but instead, the protocol’s pricing and risk assumptions were exploited under low-liquidity conditions.
Impact: $3.9 million
Significant events in December 2025:
Crypto Scams, Fraud and User Exploitation
In late 2025, anti-scam analytics firm Scam Sniffer warned that phishing and crypto fraud activity has surged, with attackers increasingly leveraging Telegram and malware-based techniques to deceive users and steal assets .According to data shared, traditional phishing scams remain widespread but are now being overshadowed by sophisticated malware campaigns that infiltrate crypto communities by posing as verification bots and spoofed services, resulting in dramatic increase in successful theft attempts.
Another high-profile incident in this category involved a compromised communication channel tied to an employee in Binance, where the attacker used the individual’s WeChat account to orchestrate a pump-and-dump market manipulation scheme, reportedly netting around $55,000. This breach illustrates just how threat actors are not targeting not just end users but also employee credentials at major crypto platforms, to execute fraud and market abuse.
Justice, Accountability and Law Enforcement Actions
Pleasantly, Law Enforcement and Investigation pressure has increased against crypto-related criminal activity in December 2025. In a major enforcement action, a 23-year old Brooklyn resident, ROnalf Spektor, was arrested and charged with orchestrating a long-running phishing and social-engineering scam that defrauded approximately 100 cryptocurrency investors out of nearly $16 million. Prosecutors allege that Spektor impersonated a Coinbase representative to convince victims to transfer funds to wallets he controlled, subsequently laundering stolen assets through exchanges and gambling platforms.
Independent blockchain investigator ZackXBT also revealed the identity of an alleged Canadian threat actor who is accused of social engineering scams that stole over $2 million by impersonating Coinbase support services. Through detailed on-chain analysis and screenshots shared on X, ZachXBT traced multiple thefts and exposed the individual’s public online behaviour and patterns of misuse.
Illicit Finance, Terror and Hostile State Financing
In a further continuation of investigative work linking crypto flows to geopolitical conflict, this month saw the release of our detailed report, analysing on-chain evidence that highlights alleged connections between major terrorist organisations, including Hamas and Hezbollah, and the Iranian Islamic Revolutionary Guard Corps (IRGC) through cryptocurrency transactions. This analysis adds to broader concerns about how state and non-state actors may leverage digital assets to circumvent sanctions and finance hostile operations.
Regulatory and Policy Developments
Regulatory landscapes around cryptocurrency continue to evolve globally, with several jurisdictions taking notable steps in December 2025. In the United States, the Federal Reserve announced it would ease certain banking restrictions related to crypto activities, rolling back earlier rules that required banks to obtain special approvals for custody, tokenisation and stablecoin operations. The change aims to give banks more flexibility in offering digital-asset services under standard supervisory oversight, though regulators emphasise that risk management requirements remain in place.
In Ghana, the national parliament passed the Virtual Asset Service Providers Bill 2025, formally legalising cryptocurrency trading and providing a regulatory framework for licensed exchanges and service providers. Under the new law, crypto asset activities are no longer in a legal grey area and will be subject to supervision by the Bank of Ghana, a move intended to protect consumers while supporting technological
NOMINIS Unique Findings:
Throughout December, NOMINIS’ research and investigative capabilities were recognised by leading international media, underscoring our role at the forefront of crypto threat intelligence. We were featured in the Financial Times in the context of the Binance lawsuit, where NOMINIS was cited for our subject matter expertise. We shared our evidence suggesting that crypto is used by internationally designated terrorist entities to move money across borders discreetly.
Our insights also reached a broader public audience, through i24 news, where NOMINIS CEO Snir Levi broke down how Iran leverages crypto to fund terror activity, translating complex on-chain intelligence into geopolitical analysis.
In parallel, following the Bondi Beach Massacre during the Jewish festival of Hannukah, targeting those who celebrate, NOMINIS released original findings exposing how Australian-based actors have sent crypto to terrorist organisations, either knowingly, or unknowingly, via ‘humanitarian charity’ fund collection, and how terrorists have interacted with Australian crypto exchanges and banking rails. Together, these moments reflect NOMINIS unique position at the intersection of on-chain investigation, geopolitical risk, and public accountability, bringing evidence-based clarity to how crypto is embedded in modern terror financing and hostile state activity.
Concluding Insights:
When viewed in the context of the full year, December 2025 highlights a clear shift in the composition of crypto losses rather than their absolute scale. While December recorded approximately $99.8 million in confirmed thefts, this figure sits well below the year’s most extreme outlier, February’s $1.77 billion, and below several other high-loss months such as May ($258.7 million), September ($153.6 million), November ($161.2 million), and July ($140.9 million). Even so, December’s losses exceeded those seen in January ($54.2 million), March ($23.4 million), April ($37.6 million), August ($65.1 million), and October ($38.8 million), placing it firmly in the mid-to-upper range of monthly impact for 2025.
What makes December distinct is not where it ranks numerically, but how those losses occurred. Earlier high-loss months were dominated by protocol-level failures, economic design flaws, and large-scale DeFi exploits that affected platforms and liquidity pools. In contrast, December’s nearly $100 million in losses were heavily concentrated in user-targeted and operational attacks, with a single $50 million address poisoning scam accounting for roughly half of the month’s total losses.
This concentration underscores a critical evolution in attacker behaviour. December demonstrates that adversaries no longer need complex, high-risk exploits to generate outsized returns. Instead, manipulation of transaction histories, compromised update pipelines, malicious signatures, and weak access controls proved sufficient to rival the financial impact of traditional smart contract exploits seen earlier in the year.
In effect, December acts as a warning signal for 2026. While total monthly losses may fluctuate, the risk surface is widening, shifting away from isolated code vulnerabilities toward the everyday tools, interfaces, and workflows that users and institutions rely on. Without widespread adoption of real-time transaction intelligence, address-level risk detection, and stronger operational safeguards, the industry is likely to see December’s pattern repeated, not as an anomaly, but as a baseline.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.






