Executive Summary
The 2025 crypto ecosystem revealed an intensifying convergence of sophisticated cyberattacks, terror financing networks, hostile state operations, and jurisdictional exploitation at unprecedented scale. Through continuous monitoring, granular on-chain analysis, open-source intelligence (OSINT), social media intelligence (SOCMINT), and deep/dark web research, NOMINIS has systematically mapped how hostile and illicit actors operate across digital asset infrastructure, revealing strategic, adaptive, and highly organized financial networks that deliberately exploit structural gaps in global compliance and enforcement frameworks.
This report presents NOMINIS' comprehensive findings from 2025, demonstrating not only how bad actors operated throughout the year, but how critical vulnerabilities in exchange architecture, regulatory fragmentation, and compliance assumptions enabled their success. Our investigations span multiple threat vectors: from record-breaking exchange compromises and North Korean state-backed cyber-financing operations, to terror-linked fundraising campaigns disguised as humanitarian aid, IRGC sanctions evasion through Western-registered exchanges, and the billion-dollar criminal marketplace infrastructure of Huione Guarantee. Each case study underscores a central conclusion: cryptocurrency has transitioned from an experimental tool for illicit finance into an embedded, operationally critical component of hostile state funding, terrorist operations, and transnational organized crime.
NOMINIS Key Findings of 2025
High-Impact Attacks Dominate Total Losses
While over 150 incidents were recorded in 2025, financial severity was driven by a small number of catastrophic breaches. The $1.46 billion Bybit attack in February alone accounted for the majority of annual losses, attributed to North Korea's Lazarus Group. On-chain exploits, primarily smart contract vulnerabilities and protocol logic flaws, were the most frequent attack vector, but off-chain attacks involving private key compromise, phishing, and insider access consistently resulted in the largest per-incident losses. This imbalance demonstrates that preventing even a handful of extreme failures would have fundamentally altered the year's financial outcome.
Jurisdictional Arbitrage as a Strategic Operating Model
Terrorist organizations and hostile states increasingly exploit jurisdictions perceived as "low-risk", politically stable, economically developed countries with regulated financial systems, to move funds with reduced scrutiny. NOMINIS analysis of random 24-hours transaction windows revealed that approximately 94% of terror-linked transactions flowed through exchanges in low-risk or Grey List jurisdictions, including China, the UAE and Canada. This distribution exposes a fundamental weakness: compliance frameworks calibrated to jurisdictional safety rather than adversarial behavior create exploitable blind spots. The gap between compliance infrastructure and law enforcement capacity has become a strategic vulnerability.
State and Terror Networks Leverage Crypto as a Survival Mechanism
Hamas, Hezbollah, the IRGC, and North Korean state actors systematically used cryptocurrency to bypass sanctions, aggregate funds, and sustain operational resilience. NOMINIS documented over $635 million processed through Hamas-linked Gaza OTC infrastructure, persistent IRGC oil-revenue laundering via USDT, and North Korea's tactical evolution from large-scale exchange breaches to relationship-driven social engineering attacks against DeFi founders and high-net-worth individuals. Cross-regional collaboration, including cryptocurrency flows linking Hezbollah financial networks to Latin American drug cartels, illustrates how terrorist financing and transnational organized crime now operate as integrated, globalised systems, with crypto serving as the connective tissue.
Exchange Vulnerabilities are Structural, Not Incidental
NOMINIS' investigations into instant exchanges, nested exchange architectures, and offshore/no-KYC platforms revealed that transaction speed, custodial opacity, and jurisdictional arbitrage are deliberately weaponized by threat actors. Instant swaps enable post-exploit funds to move faster than detection systems can respond. Nested exchanges allow proxy services to aggregate high-risk activity under compliant façades. Offshore platforms provide anonymity at scale through weak KYC, opaque ownership structures, and regulatory fragmentation. The Binance lawsuit analysis revealed that approximately 30% of funds across just nine highlighted wallets originated from terror-linked sources, demonstrating how structural design choices can create permissive environments for sustained illicit activity.
Education, Intelligence, and Proactive Detection are Non-Negotiable
Technology alone cannot counter adaptive adversaries. NOMINIS' approach integrates continuous transaction monitoring (KYT), behavioral analytics, wallet clustering, geolocation intelligence, and multi-source OSINT/SOCMINT into a unified detection framework. Through partnerships with ACAMS and direct collaboration with law enforcement, we translate intelligence into operational vigilance, empowering exchanges, VASPs, compliance teams, and regulators to identify high-risk activity before exploitation occurs. Our Terror Financing Database, built in collaboration with law enforcement and now encompassing thousands of verified wallets, exemplifies how intelligence sharing and proactive flagging can disrupt illicit networks in real time.
Report Structure
This report is organised into thematic sections, each providing both investigative depth and actionable intelligence:
1. Crypto Hacks of 2025
A comprehensive breakdown of over 150 recorded incidents, including month-by-month loss analysis, attack vector distribution (smart contracts, access control, private key compromise), blockchain and asset targeting trends, mixer usage patterns, and attribution insights. This section establishes the financial and operational landscape that defined the year.
2. Prevention of Hostile State and Terror Financing
- The Gap Between Compliance and Law Enforcement
An examination of how terrorist organizations and hostile states exploit low-risk jurisdictions, with detailed case studies on Australia's exposure to terror-linked fundraising and crypto infrastructure misuse. Includes empirical analysis demonstrating that 94% of terror transactions targeted low- or monitored-risk exchanges, revealing systematic exploitation of perceived safety.
- Spotlight on the Middle East
In-depth investigations into Hamas' use of Buy Cash, Binance, and humanitarian-themed fundraising; analysis of the Binance lawsuit and $383 million in terror-exposed wallet flows; the Hezbollah-Cartel crypto pipeline linking Middle Eastern militants to Latin American drug cartels; and IRGC sanctions evasion via oil-revenue laundering and London-based exchanges (Zedcex, Zedxion). This section provides the most comprehensive public documentation of Middle Eastern terror financing via cryptocurrency to date.
- Spotlight on North Korea
Documentation of North Korea's tactical evolution from large-scale exchange breaches (Bybit, $1.4 billion) to targeted, relationship-driven social engineering attacks on DeFi founders and high-net-worth individuals. Analysis of infiltration efforts into Western crypto entities via falsified developer credentials, malware deployment, and insider access. Demonstrates how cryptocurrency has become a state survival mechanism funding nuclear programs and regime operations.
- Spotlight on Russia
Examination of Russia's reliance on cryptocurrency as a sanctions workaround, including the use of MIR Pay as a crypto on-ramp and the Aeza Group bulletproof hosting investigation. Highlights how Russia's embedded darknet ecosystem enables sustained sanctions evasion through OTC brokers, ransomware infrastructure, and alternative payment rails.
- Geolocation Intelligence and Jurisdictional Masking
Analysis revealing how Iranian and other high-risk users appear as U.S. or German traders via VPN/proxy networks, undermining IP-based compliance controls. Demonstrates the necessity of multi-layered location intelligence combining behavioral analytics, wallet clustering, and network telemetry.
3. Exchange Infrastructure Analysis
Systematic evaluation of instant exchanges (transaction speed as a laundering vector), nested exchanges (compliance infrastructure repurposed as a proxy layer), and offshore/no-KYC platforms (jurisdictional arbitrage at scale). Includes licensing, custodial architecture, and withdrawal limit assessments across 18+ platforms, revealing structural enablers of illicit finance.
4. OSINT-Driven Insights
Case studies including blockchain intelligence applied to U.S. synagogue bomb threats demanding Bitcoin payments, and the uncovering of connected crypto game fraud (Epic Ballad Ponzi scheme and Legend of Constellations rug pull). Demonstrates the breadth of NOMINIS' investigative methodology across financial crime, fraud, and real-world threat analysis.
5. SOCMINT-Driven Insights
Detailed investigation into Huione Guarantee and Huione Group, revealing a tens-of-billions-of-dollars criminal marketplace ecosystem operating via Telegram, facilitating pig butchering scams, romance fraud, phishing infrastructure, and USDT-based settlement. Documents the subsequent Telegram takedown, license revocations, and merchant migration to successor platforms.
6. Dark Web Intelligence
Analysis of cryptocurrency usage across dark web ecosystems, revealing that Bitcoin (64%) and Tron remain dominant, while Monero adoption grows. Drug trafficking represents 36% of activity, followed by stolen credit cards (14%), weapons (13%), and hacking services (12%). Includes findings on human organ trafficking and CSAM, underscoring the most severe misuse cases.
7. 2025 Developments of the NOMINIS Platform
Overview of AsKYT (AI-driven Bitcoin analytics), CryptoSanctions.net (comprehensive sanctions resource), case management tools, Risk Radar visualization, and Shadow Intelligence (off-chain context integration). Outlines upcoming forensic suite expansion for law enforcement and private investigators in 2026.
This report equips industry stakeholders, exchanges, VASPs, banks, regulators, law enforcement, and compliance professionals, with a comprehensive, evidence-based understanding of how bad actors operated in 2025 and the structural vulnerabilities they exploited. It demonstrates that jurisdictional trust, transaction speed, and custodial opacity have become weapons in the hands of adversaries, and that static compliance frameworks calibrated to geography rather than behavior will continue to fail.
NOMINIS' contributions extend beyond documentation. Through early-warning intelligence, continuous monitoring, wallet clustering at scale (over 1 billion wallets), terror financing database construction, and education partnerships, we have provided the industry with tools, insights, and operational frameworks to detect, disrupt, and prevent the misuse of digital assets before harm occurs.
The challenges outlined in this report will persist into 2026 and beyond. However, by combining advanced analytics, intelligence-driven transaction monitoring, cross-jurisdictional enforcement, and a commitment to education and transparency, the crypto ecosystem can evolve to meet these threats with resilience, accountability, and precision.
Crypto Hacks of 2025
This section of the NOMINIS monthly report accumulates findings derived from NOMINIS’ ongoing monthly monitoring and analysis of publicly reported crypto hacks, exploits and thefts throughout 2025.
The findings presented in this report are based on continuous data collection conducted as part of NOMINIS’ monthly threat intelligence and incident reporting. Each recorded event was aggregated from publicly disclosed incidents, on-chain analysis, investigative reporting, and open-source intelligence. Monthly datasets were consolidated to identify broader trends, recurring attack patterns, and structural risks across blockchains, entities, and attack vectors. While the data reflects confirmed and attributed incidents at the time of reporting, figures may evolve as investigations progress and additional laundering activity is identified.
The 2025 calendar year stands as one of the most instructive periods in crypto security history. While the total number of incidents did not increase dramatically compared to prior years, the financial severity of successful attacks escalated sharply, driven by a small number of high-impact compromises. More than 150 recorded incidents resulted in multi-billion-dollar cumulative losses, exposing systemic weaknesses across smart contracts, operational security, access control, and key management.
The data shows that attackers ceased relying on opportunistic experimentation. Instead, they execute selective, intelligence-driven attacks against liquidity-dense environments, privileged infrastructure, and poorly segmented operational controls.
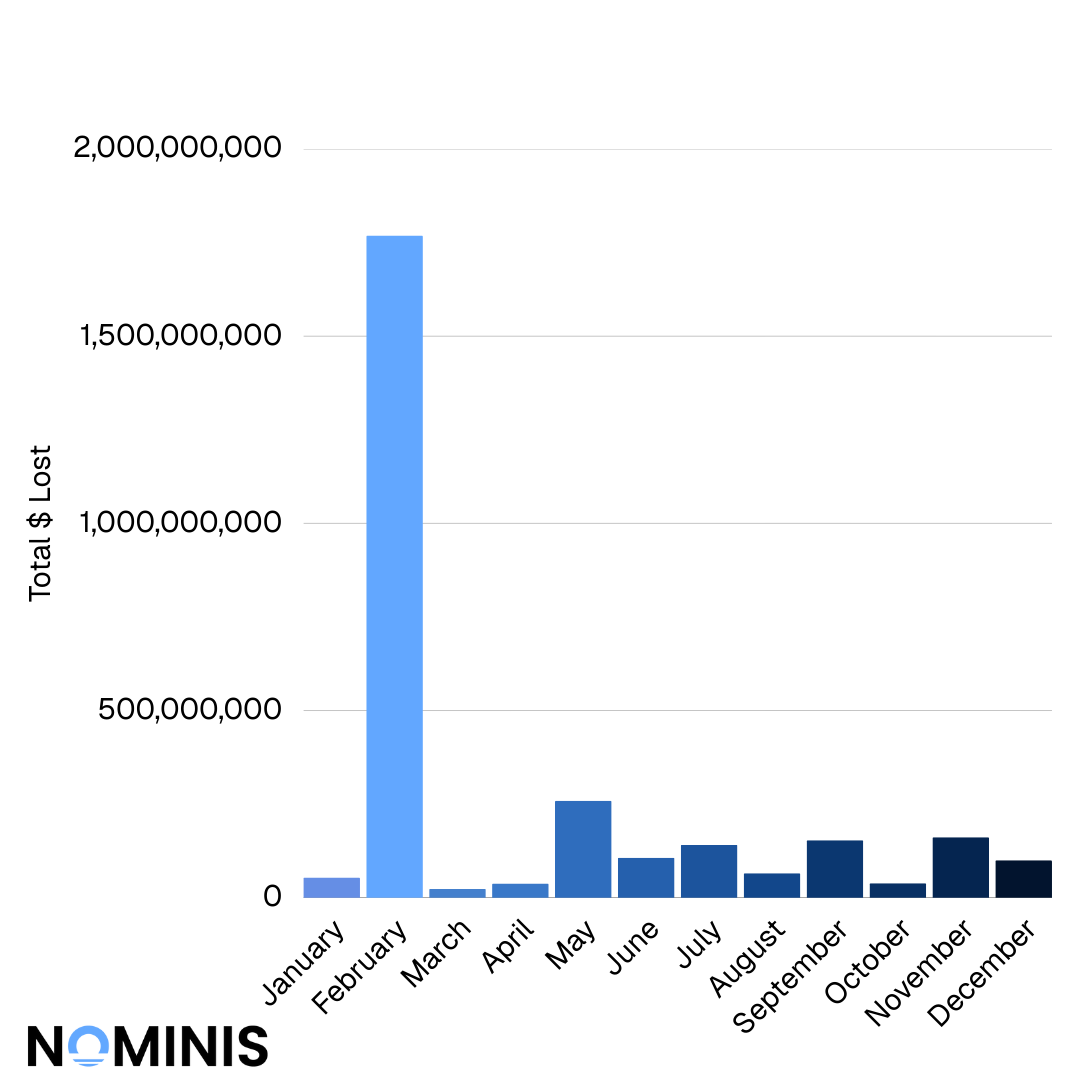
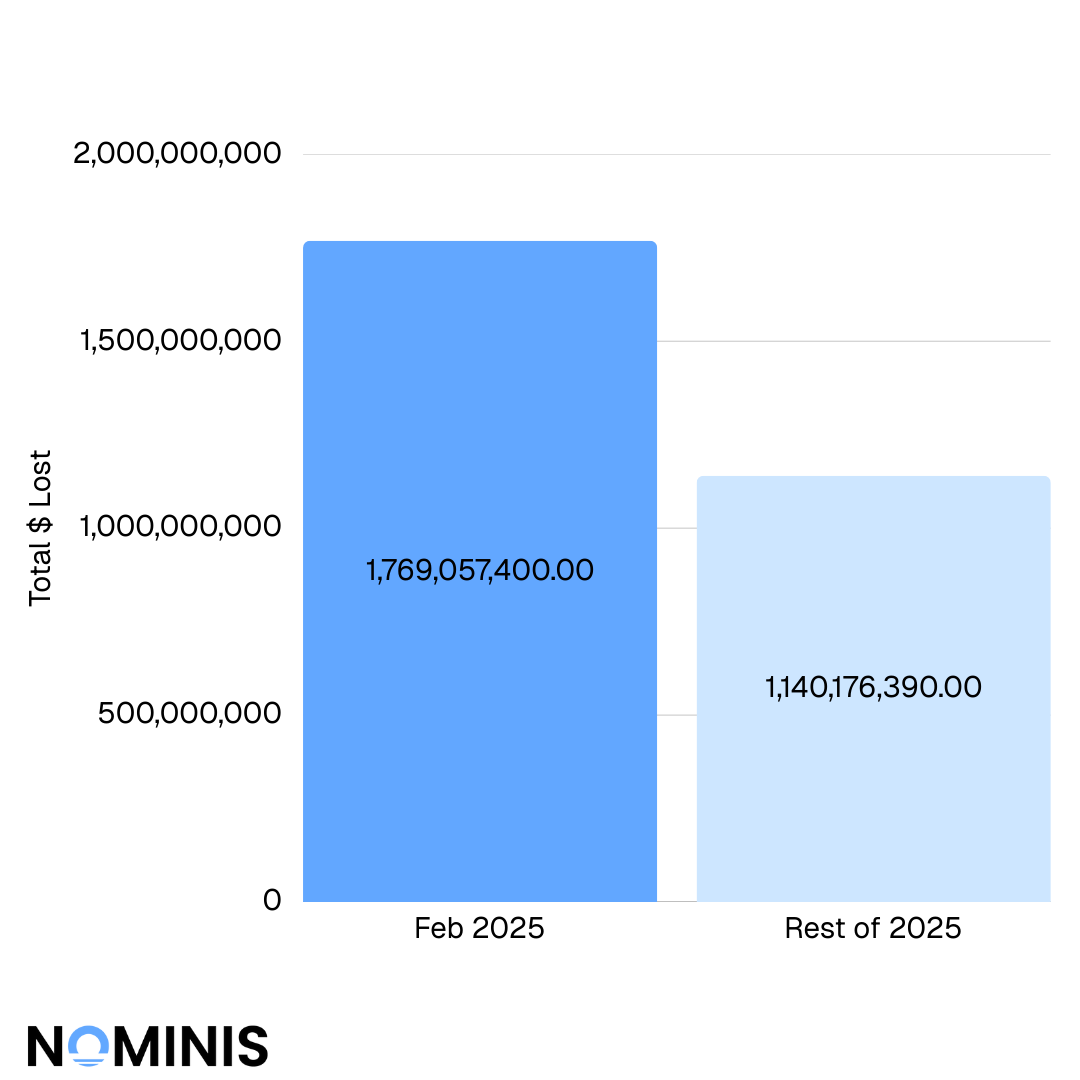
February 2025 alone recorded approximately $1.77 billion in crypto losses, exceeding the combined losses of all other months.
This is due to the record-breaking Bybit attack, in which the Dubai-based exchange lost $1.46 billion, now attributed to North Korean based Lazarus Group. The incident took place on 21st February 2025, during a transfer of funds from a cold to warm wallet, when attackers gained control and transferred 401,000 ETH to unknown addresses.
A month-by-month breakdown of 2025 losses can reveal that 2025 as a year was defined by concentration, rather than cyclical patterns.
January began with $54.2 million in recorded losses, setting an already elevated baseline. February then experienced an unprecedented surge to approximately $1.77 billion, representing the single most destructive month of the year and accounting for a substantial share of total annual losses.
Following this peak, March dropped sharply to $23.4 million and April recorded $37.6 million, suggesting a temporary contraction in attack severity rather than frequency. However, May saw losses rebound to $258.7 million, reaffirming that February was not a behavioral anomaly but an extreme scaling event.
June and July remained elevated, with losses of $106.8 million and $140.9 million respectively. Even during August, traditionally viewed as a quieter period, losses reached $65.1 million. September once again crossed the $150 million threshold, followed by a relatively lower October at $38.8 million. November recorded $161.2 million, and December closed the year with nearly $99.8 million in losses.
Most attacks in 2025 were small to mid-sized, but total losses were driven by a limited number of extreme events.
When incidents are grouped by loss size, a heavy-tailed distribution emerges. The majority of recorded hacks resulted in losses under $10 million. However, a small cluster of incidents exceeding $100 million accounted for a disproportionate share of total losses.
This imbalance suggests that preventing even a handful of catastrophic failures would have dramatically altered the year’s financial outcome.
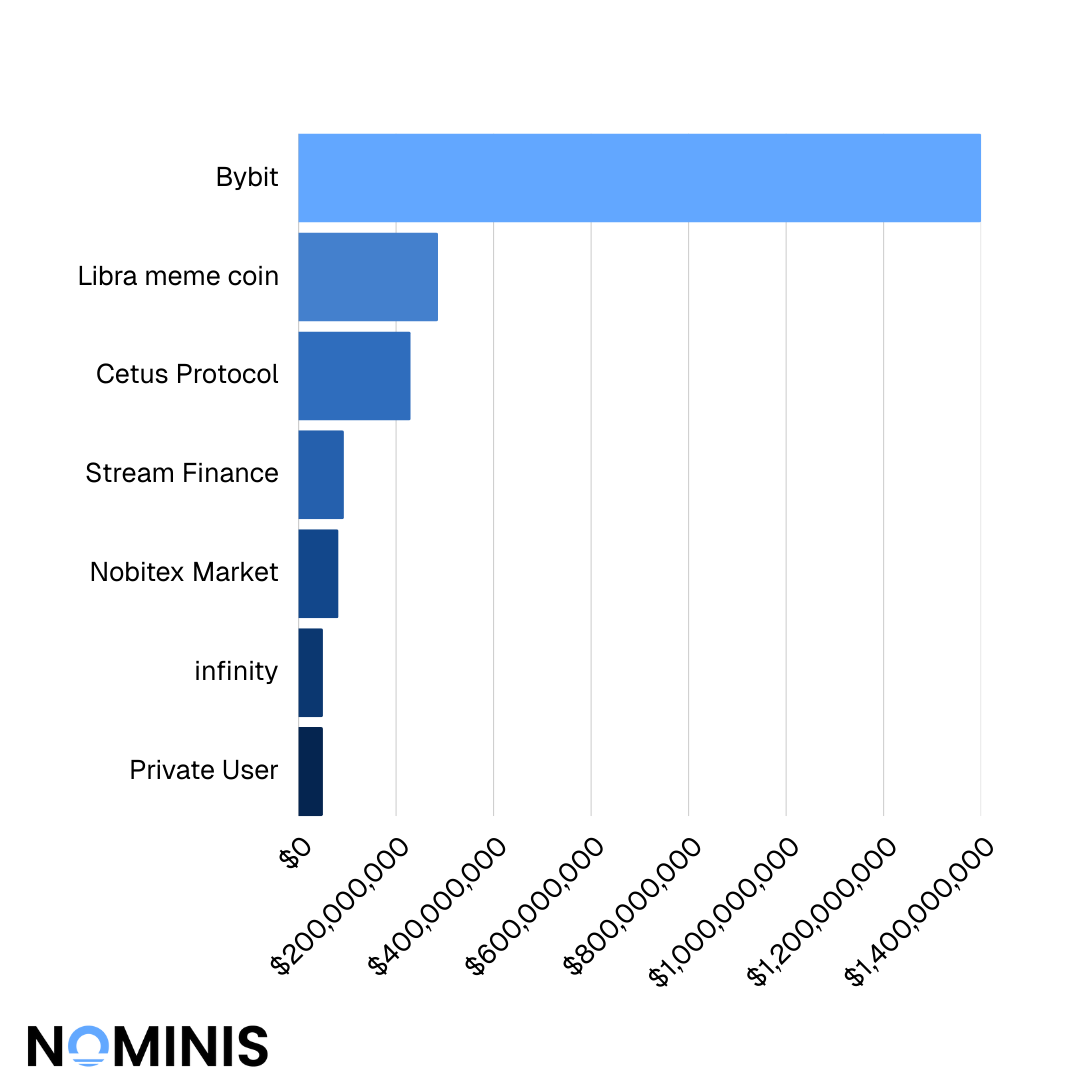
On-chain attacks were significantly more frequent in 2025, while off-chain attacks caused greater financial damage per incident.
A clear divergence emerges when separating attacks by execution layer.
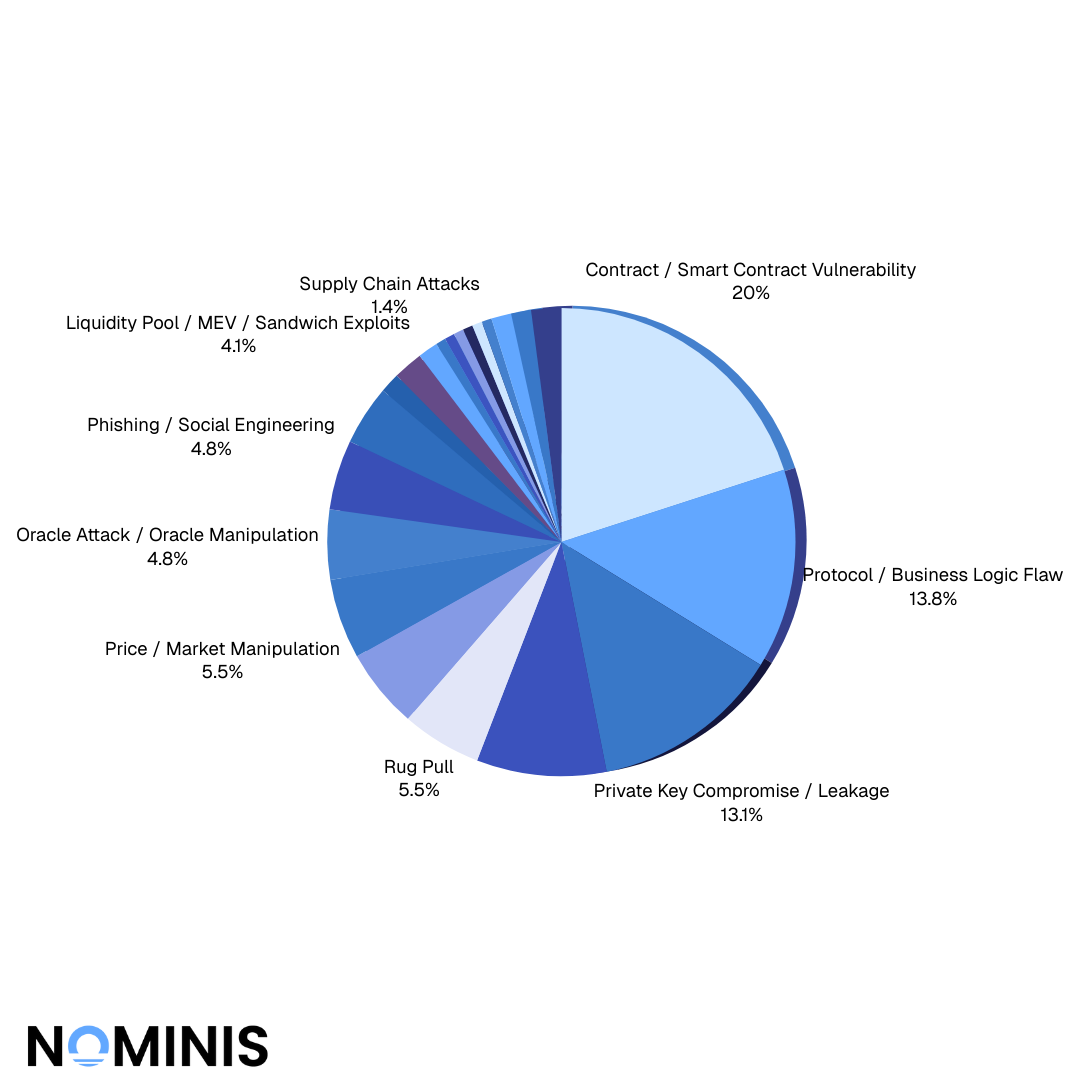
On-chain exploits accounted for the majority of recorded incidents throughout the year. These included smart contract vulnerabilities, protocol logic flaws, business logic errors, and access control failures. The relative ease of testing contracts, combined with composability across DeFi systems, made on-chain targets consistently attractive.
Off-chain attacks, including private key compromise, phishing, credential theft, and insider access, occurred far less frequently. However, these incidents produced larger median and maximum losses, often enabling attackers to bypass on-chain safeguards entirely.
In 2025, frequency favored on-chain exploits, while financial devastation favored off-chain compromise.
This distinction reinforces a critical insight: security maturity on-chain has advanced faster than operational security off-chain.
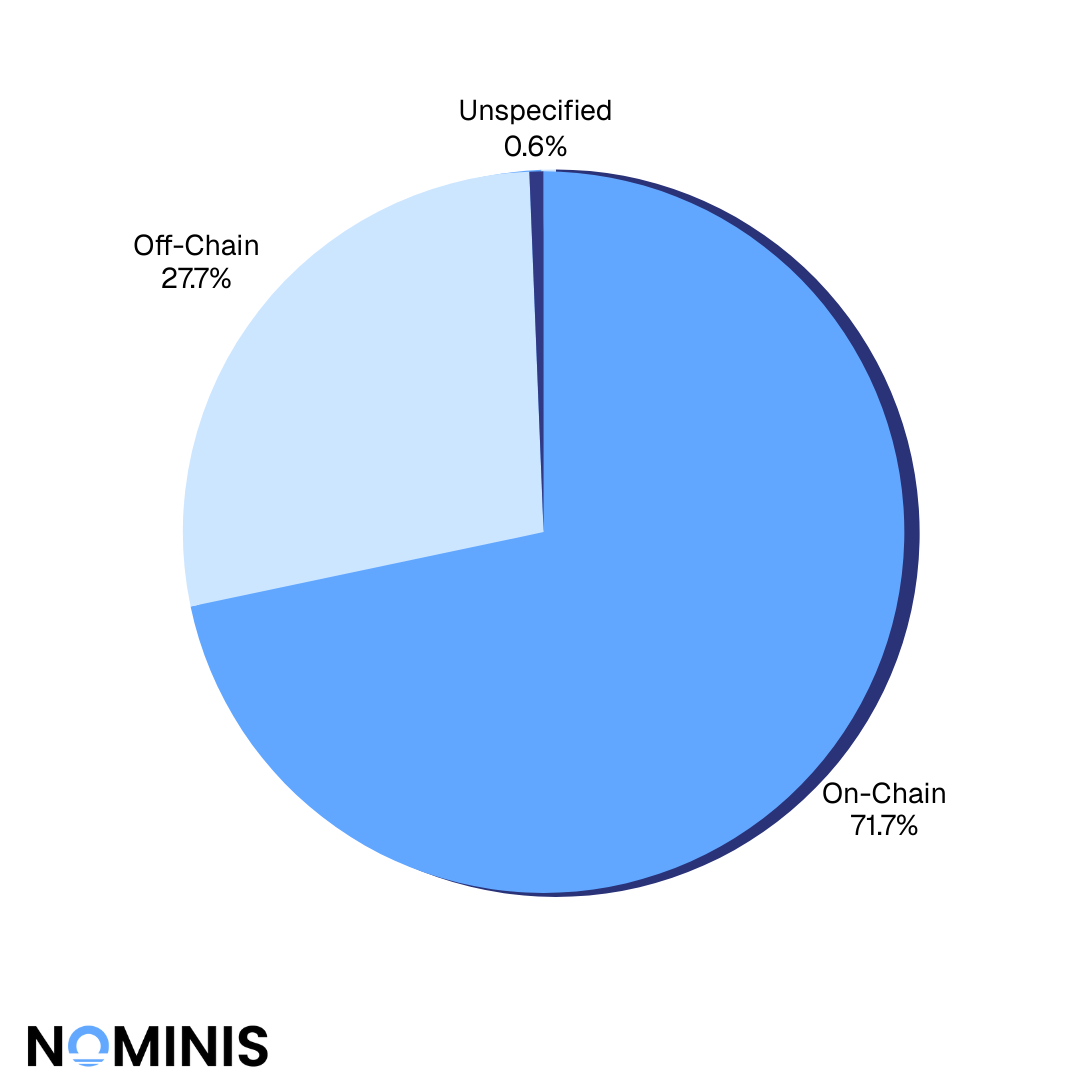
Smart Contract vulnerabilities were the most common attack vector of 2025.
Followed by protocol logic flaws and business logic errors. These incidents often stemmed from unsafe assumptions, improper validation, flawed upgrade paths, or incomplete permissioning models.
Access control failures and private key compromises occurred less often but were consistently associated with the largest losses. In many cases, a single compromised administrative key enabled attackers to mint tokens, drain treasuries, or disable security mechanisms.
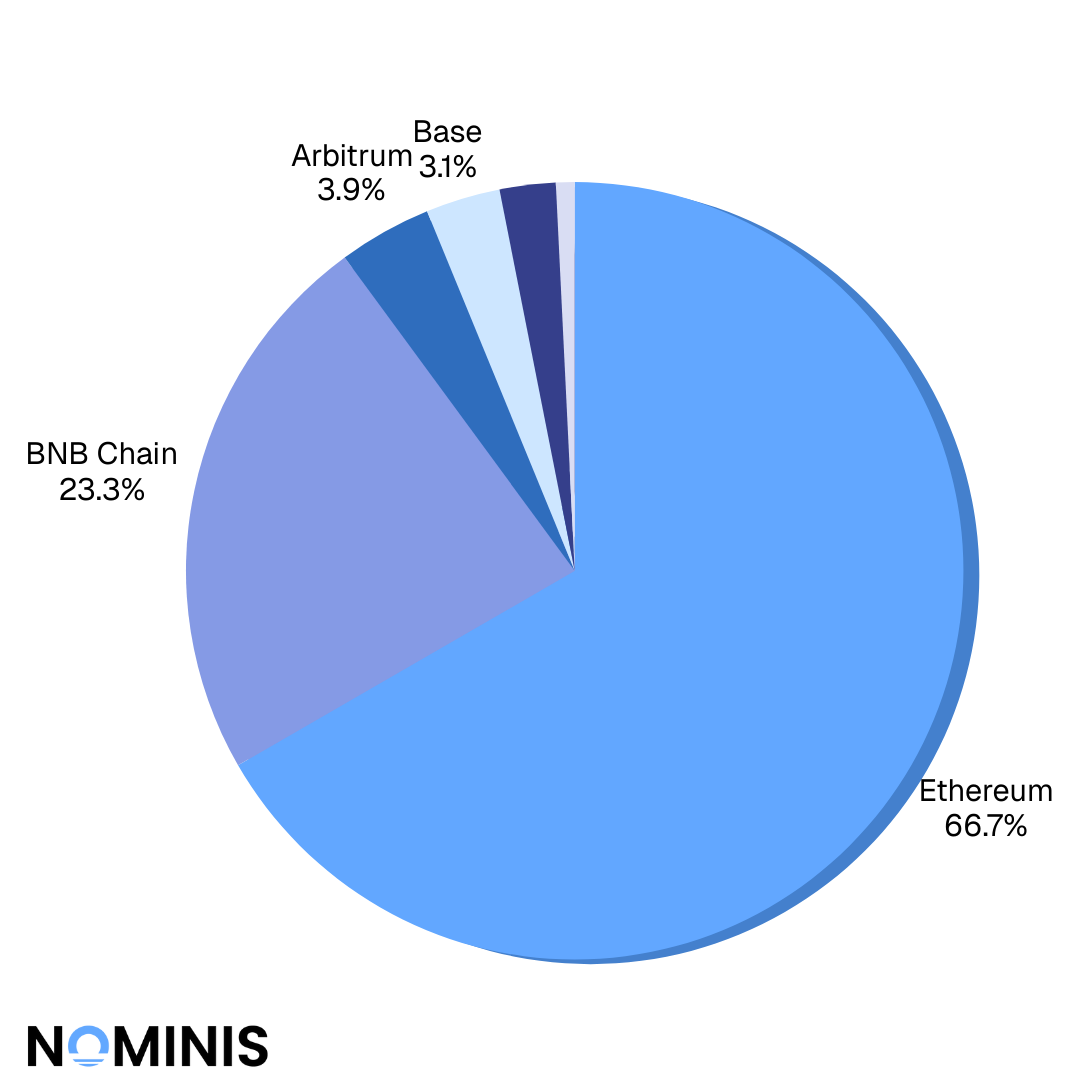
Ethereum was the most targeted blockchain in 2025, reflecting its dominance as the primary liquidity and execution layer.
Ethereum accounted for the highest number of recorded incidents by a wide margin. This dominance aligns with its role as the backbone of decentralized finance and asset settlement.
BNB Chain ranked second, with a high concentration of token-level and access control exploits. Notably, its share of incidents appeared disproportionate to its total value locked, suggesting structural weaknesses in token governance and deployment practices.
Layer-2 networks such as Arbitrum and Base featured repeatedly, confirming that attackers actively follow liquidity as it migrates across ecosystems. Other chains, including Solana, Avalanche, and Tron, appeared less frequently but often played roles in laundering or cross-chain movement.
The most valuable targets were not individual tokens, but consolidated treasuries and infrastructure-level access points.
Native chain tokens and project-issued assets dominated stolen value. Stablecoins appeared primarily in large-scale off-chain incidents and bridge compromises, where custodial or treasury access enabled direct extraction.
Multi-asset thefts were a defining feature of infrastructure and bridge attacks, underscoring the systemic risk posed by centralized control points within decentralized ecosystems.
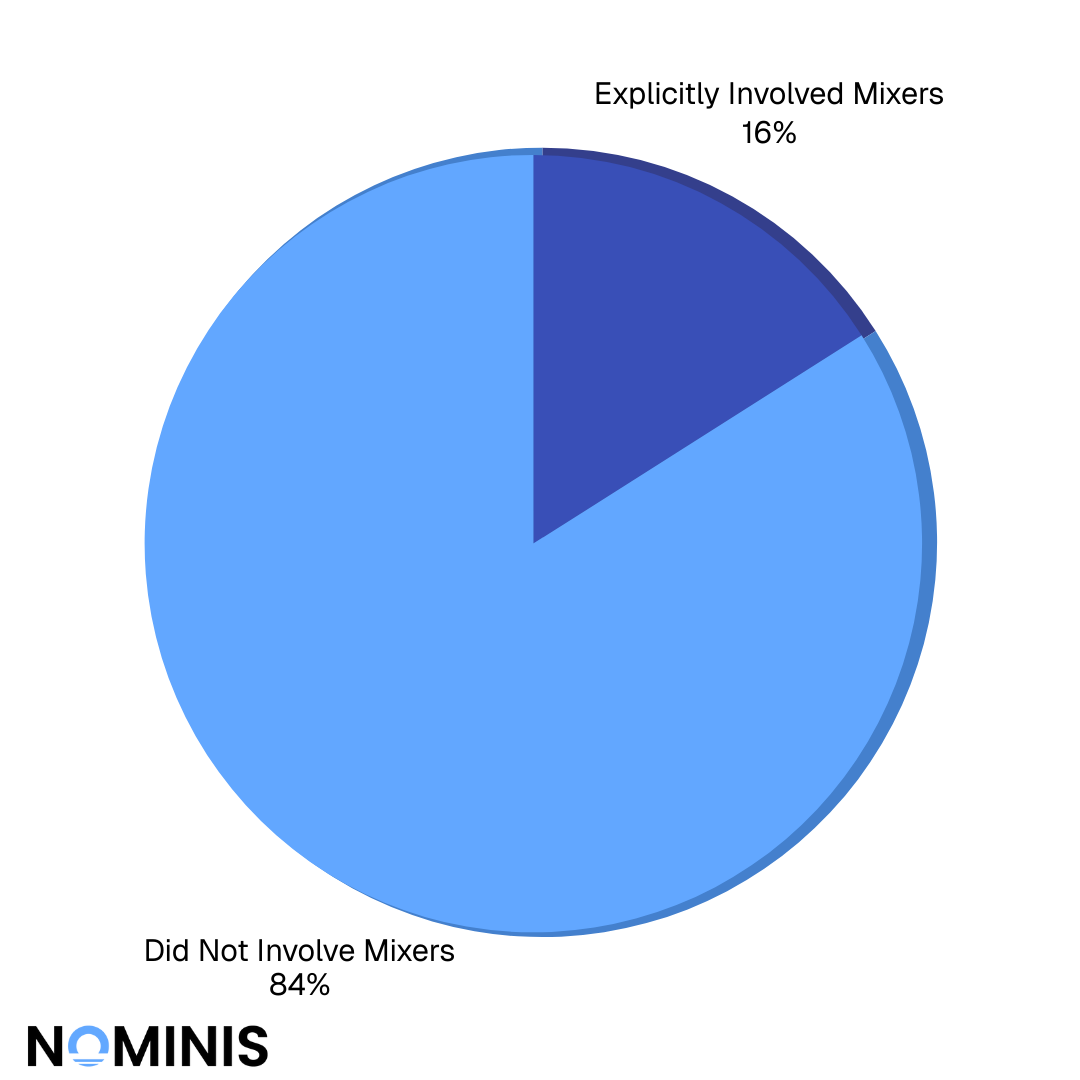
~16% of recorded hacks explicitly involved mixers, although delayed laundering likely increases the true figure.
Mixer usage was observed in roughly one-sixth of incidents, with Tornado Cash remaining the dominant service. Importantly, mixers were disproportionately associated with high-value thefts.
The low percentage does not necessarily mean mixers were not used. Attackers may move to use mixers later in their laundering process, or the use of a mixer may not be validated until much later after the attack took place.
North Korea-linked actors accounted for a small share of incidents, but some of the most sophisticated and strategically executed attacks.
Explicit attribution to North Korean entities appeared in approximately 4-5% of recorded cases. These incidents consistently displayed advanced operational security, structured laundering paths, and extended timelines. It is difficult to ascertain exactly how many hacks or scams North Korean hacking entities are responsible for, given it is not always possible to verify their responsibility; this can take a significant amount of time.
Readers can skip to Spotlight on North Korea in this report for more coverage of North Korea’s role in crypto crime in 2025.
Of all targeted entities, DeFi protocols were attacked most frequently, while centralized platforms suffered the highest per-incident losses
DeFi protocols dominated incident counts due to their composability, rapid deployment cycles, and public attack surface. Token projects were also heavily targeted, particularly through compromised admin keys and flawed minting logic.
Centralized exchanges and custodians appeared less often, but when compromised, losses were significantly larger, reflecting their concentration of user funds and systemic importance.
NOMINIS contributions to prevention of Hostile State Financing and Terror Financing
In 2025, the financial networks of hostile states and terrorist actors became increasingly sophisticated, exploiting gaps between compliance frameworks and law enforcement oversight. High jurisdiction countries such as Russia and Iran, alongside terror-linked actors, continue to move funds through jurisdictions widely perceived as low risk, politically stable, economically developed countries with regulated financial systems, including Australia. Licensed exchanges operating with legacy tools are often taken advantage of, highlighting the critical importance of Know Your Transaction (KYT) systems. Without dynamic, intelligence-driven monitoring, these actors can circumvent detection, using detection avoidance methods to operate under the radar.
This report demonstrates how NOMINIS addresses these challenges through a comprehensive approach that spans multiple regions, sectors, and operational methodologies. Our investigations explore terror-linked fundraising and cryptocurrency flows in the Middle East, exposing how Hamas and affiliated networks use exchanges and over-the-counter brokers to solicit, convert, and move funds. In North Korea, we examine the evolution of state-backed cyber-financing, from large-scale exchange breaches to targeted, relationship-driven intrusions against high-value individuals and DeFi projects, including efforts to infiltrate crypto entities for malware deployment and intelligence gathering. Russia’s reliance on cryptocurrency and alternative payment infrastructure, alongside a deeply embedded darknet ecosystem, illustrates the growing sophistication of state-aligned and criminal networks exploiting financial opacity.
The report also assesses the involvement of major global exchanges, including the Binance lawsuit, highlighting structural and legal gaps that may allow terror-linked funds to flow through otherwise legitimate platforms. Across all regions, our work shows how hostile actors adapt to sanctions, leverage behavioral obfuscation, operate across multiple jurisdictions and blockchains, and exploit systemic trust in low-risk environments.
Finally, we underscore that prevention is not solely a matter of technology or regulation. Education and capacity building are central to our strategy, translating intelligence into operational vigilance for compliance teams through targeted guidance and training. Complementing this is our GeoIntelligence platform, which combines behavioral analytics, wallet clustering, geolocation, and network-based risk scoring to proactively identify high-risk activity before it can be exploited.
Taken together, these investigations demonstrate a recurring pattern: terrorist and hostile state actors deliberately exploit the friction between compliance and enforcement, using low-risk jurisdictions and licensed infrastructure to advance their objectives. Our findings reinforce the necessity of dynamic, intelligence-driven transaction monitoring, combined with education and actionable insights, to prevent the misuse of the global financial system for terror financing.
The Gap between Compliance and Law Enforcement
VASPs in ‘safe countries’ are being exploited by high jurisdiction countries and Terror groups to move funds
Over the course of the past year, NOMINIS investigations repeatedly identified a structural weakness that transcends geography, ideology and organisational structure. Terrorist organisations and Hostile State aligned networks are increasingly shifting critical components of their financial activity away from designated high risk jurisdictions and into environments widely perceived as low risk. These jurisdictions are typically politically stable, economically developed and equipped with formal anti money laundering and counter terror financing frameworks. Precisely because of these characteristics, they are assumed to pose a lower exposure to hostile state financing and terrorist misuse.
This assumption has become a strategic vulnerability. In practice, the designation of a jurisdiction as low risk often results in reduced investigative urgency, lower alert sensitivity and less aggressive transaction level scrutiny. While compliance frameworks may be technically robust, enforcement activity is frequently reactive rather than proactive, and intelligence integration remains limited. Terror linked financial activity that would be immediately escalated in sanctioned or conflict affected regions can therefore operate within low risk environments for extended periods without disruption.
This phenomenon reflects a widening gap between compliance and law enforcement. Compliance systems are often designed to satisfy regulatory requirements rather than to detect adaptive, adversarial behaviour. Law enforcement, meanwhile, must prioritise resources toward jurisdictions already labelled as high risk. The result is an exploitable space where hostile actors can operate inside trusted financial ecosystems, leveraging the credibility of those systems as a form of operational camouflage.
Australia: a Politically-Stable State Experiencing Terror Misuse
Terror Financing under the guise of Humanitarian Fundraising.
Australia represents a particularly illustrative example of this dynamic. As a stable Western democracy with a strong regulatory reputation, Australia is widely regarded as a low risk jurisdiction for terror financing. Its financial institutions operate under established AML and CTF obligations, and its digital asset ecosystem is increasingly regulated. However, NOMINIS investigations demonstrated that this perception of low risk was actively exploited by terrorist actors seeking both to raise funds and to access cryptocurrency liquidity with minimal friction.
Following the Bondi Beach massacre, NOMINIS conducted an in depth investigation into terror financing activity intersecting Australian banks, cryptocurrency service providers and domestic fundraising efforts. The investigation revealed how terrorist linked actors were able to solicit funds from within Australian society under the guise of humanitarian and charitable causes, such as the ‘humanitarian flotilla’ missions, while simultaneously utilising Australian-based financial and crypto infrastructure to receive, convert and move those funds onward.
On the fundraising side, terrorist aligned networks relied heavily on narrative legitimacy. Campaigns were framed around humanitarian emergencies, civilian suffering and aid delivery in overseas conflict zones. These appeals circulated through social media platforms, encrypted messaging applications and community networks, targeting donors who believed they were contributing to lawful and compassionate causes. The success of these efforts did not depend on anonymity or coercion, but on trust, emotional resonance and the absence of effective oversight mechanisms capable of distinguishing legitimate charity from abuse. OSINT intelligence exclusive to NOMINIS demonstrated verified terrorists playing organisational roles in running the social media platforms and raising money for ‘humanitarian campaigns’.

Saif Abukeshek, a confirmed Hamas operative, is the administrator of the Global Movement to Gaza Australia Telegram group and reportedly the owner of the group. Under the guise of humanitarian efforts to sail to Gaza to ‘break the siege’, confirmed Hamas operatives were accepting Crypto donations and funneling them into terror-financing channels.

On-chain analysis conducted by NOMINIS demonstrated that funds raised through these campaigns were routed into wallet clusters exhibiting clear exposure to designated terrorist organisations and known facilitators. Transaction patterns included rapid aggregation of small donations, brief holding periods and onward transfers to regional intermediaries and OTC brokers. These behavioural characteristics align with established terror financing typologies, yet were able to persist due to the fragmented nature of oversight across fundraising platforms, banks and crypto services.
Terror Financing continued via Australian Exchanges and crypto Infrastructure, remaining unchecked.
Parallel to this fundraising activity, NOMINIS identified the use of Australian cryptocurrency brokers and service providers as transit and conversion points for high risk funds. These entities were not clandestine operations or offshore shell exchanges. They were legally registered businesses operating openly within a low risk jurisdiction, servicing retail users and OTC clients. However, their KYT capabilities were limited, heavily reliant on static sanctions screening and insufficiently integrated with behavioural and network based analysis.
As a result, wallets with clear transactional proximity to terrorist organisations were able to interact with Australian crypto services without meaningful interruption. Funds were converted between assets, consolidated and routed onward to international destinations using high liquidity instruments such as stablecoins. In several cases, these flows continued over extended periods, indicating that compliance controls failed to identify either the cumulative risk or the network context of the activity.

The Australian case is not an anomaly. It reflects a broader global trend in which terrorist organisations and hostile state actors deliberately distribute financial activity across jurisdictions perceived as stable, reputable and low risk. Rather than concentrating exposure in sanctioned environments where scrutiny is intense, these actors fragment their operations, using low risk jurisdictions as liquidity hubs, conversion points and temporary storage environments within a wider financial architecture.
This strategy allows hostile actors to benefit from the credibility of trusted financial systems. Transactions processed through institutions in low risk jurisdictions carry an implicit assumption of legitimacy, reducing downstream scrutiny when funds move onward to other platforms or regions. In effect, the reputational strength of these jurisdictions becomes a shield that masks the origin and intent of illicit activity.
This dynamic exposes a fundamental limitation of jurisdiction based risk models. Traditional risk frameworks assume that terror financing risk correlates primarily with geography. However, when adversaries intentionally operate within low risk environments, geographic assumptions become unreliable indicators of actual exposure. Compliance that is calibrated to perceived jurisdictional safety rather than to adversarial behaviour creates blind spots that can be systematically exploited.
Beyond individual case studies, NOMINIS observed broader indicators suggesting that terror linked funds are routinely directed into exchanges and service providers operating in low risk jurisdictions. These environments offer deep liquidity, access to global markets and reduced expectation of hostile state activity. For terrorist organisations facing increasing pressure in high risk regions, they function as essential pressure release valves within a resilient, distributed financial system.
Beyond Australia:
To examine this phenomenon empirically, NOMINIS conducted a focused analysis of terror-linked transaction flows over a defined twenty-four-hour period, tracing the movement of funds from wallets associated with designated terrorist organisations into exchange infrastructure across multiple jurisdictional risk tiers. Jurisdictional risk was assessed using FATF classifications, with low-risk jurisdictions defined as countries not appearing on the FATF Black or Grey Lists, increased-risk jurisdictions defined as Grey List countries, and high-risk jurisdictions encompassing FATF Black List countries as well as Cambodia and Russia.
This analysis, presented in the following section, provides a time-bounded snapshot of transaction velocity, destination concentration, and behavioural consistency, illustrating how rapidly terror-linked value can enter trusted or semi-trusted financial environments.
This observation does not represent an isolated spike or anomaly. Rather, it should be understood as a cross-section of a persistent operational pattern. By examining transaction behaviour within a short, controlled timeframe, structural characteristics become visible that are often obscured within long-term aggregates. The findings therefore provide quantitative context to the qualitative investigations outlined earlier in this report.
The analysis revealed that of a total of 19,860 transactions sent by illicit and terror-linked actors to identifiable exchanges, the majority were directed toward exchanges operating outside of traditionally “high-risk” jurisdictions. Specifically, 16,674 transactions were routed to exchanges based in low-risk jurisdictions, including the UAE, Singapore, Lithuania, Estonia, Canada, Thailand, Nigeria, Australia, the United Kingdom, Cyprus, France, South Africa, the United States, Costa Rica, and St. Vincent and the Grenadines.
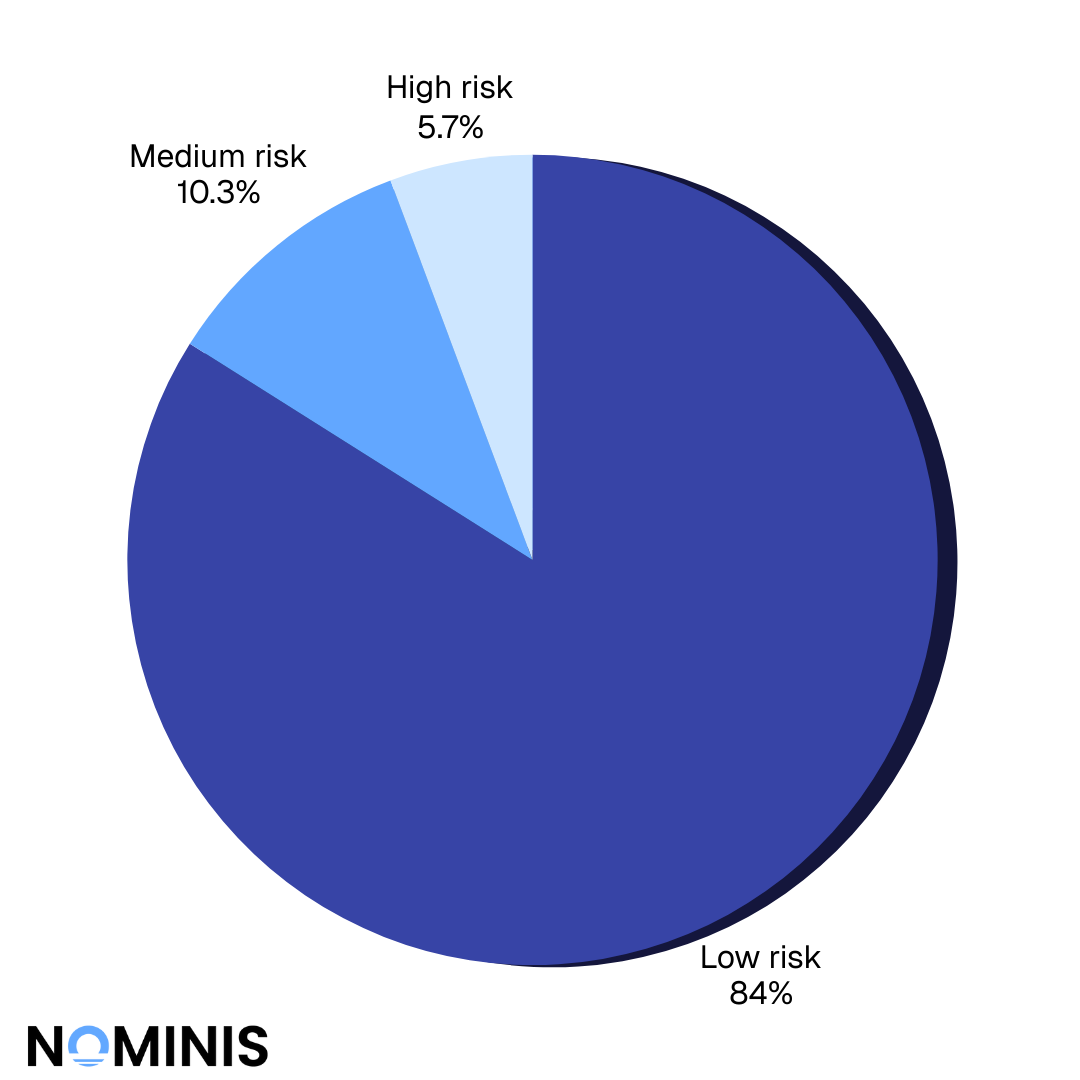
A further 2,054 transactions were sent to exchanges located in increased-risk jurisdictions appearing on the FATF Grey List, with notable concentrations in Seychelles, Curaçao, Panama, Indonesia, Turkey, the Cayman Islands, the Philippines, Brazil, Georgia, Belize, Argentina, Taiwan, Hong Kong, and El Salvador.
By contrast, only 1,132 transactions were directed toward exchanges operating in high-risk jurisdictions, defined as FATF Black List countries alongside Cambodia and Russia. This comparatively small volume underscores a deliberate avoidance of jurisdictions subject to the most stringent international scrutiny.
Overall, approximately 94% of all identified terror- and illicit-linked transactions were sent to exchanges operating in either low-risk or increased-risk jurisdictions. This distribution reinforces a critical insight: enforcement intensity and regulatory scrutiny, rather than formal jurisdictional risk labels alone, play a decisive role in shaping illicit routing behaviour. Where AML and KYT controls are inconsistently applied or unevenly enforced, those gaps are systematically exploited.
These findings reveal a clear operational preference. Terror-linked actors overwhelmingly favour jurisdictions that are perceived as accessible, reputable, or operationally permissive, while largely avoiding environments subject to explicit sanctions or comprehensive isolation. This pattern highlights both the strategic selection of exchange destinations by hostile actors and the critical importance of monitoring Grey List jurisdictions, where regulatory frameworks may exist but enforcement gaps remain exploitable.
The results further demonstrate the velocity and scale with which terror-linked value can permeate the broader crypto financial ecosystem, even within a tightly constrained twenty-four-hour observation window. By quantifying transaction flows across jurisdictional risk categories, NOMINIS provides actionable intelligence for compliance teams and financial intelligence units tasked with detecting and disrupting terrorist financing activity across both low- and increased-risk environments.
From a strategic perspective, the implications are significant. Some of the most consequential terror financing risks now emerge not from sanctioned or high-risk jurisdictions alone, but from the interaction between hostile actors and financial ecosystems that are broadly perceived as compliant or trustworthy. Where compliance frameworks rely on static jurisdiction-based risk assumptions, and enforcement prioritisation is guided more by geography than behaviour, illicit actors are able to operate in plain sight.
NOMINIS’ findings reinforce the necessity of moving beyond static risk classifications toward continuous, transaction-driven intelligence. Preventing terrorist financing in low- and Grey List jurisdictions requires persistent visibility into behavioural patterns, transactional velocity, network proximity, and evolving typologies. As terrorist organisations continue to adapt under sanctions pressure and regulatory scrutiny, the exploitation of low-risk and increased-risk jurisdictions will remain a central, and escalating, challenge within the global counter-terror financing landscape.
Spotlight on the Middle East
Hamas are utilising Buy Cash, Binance and ‘Humanitarian Aid’ to fund terror activity
Following the October 7th attack by Hamas, US and international authorities significantly expanded sanctions and designations targeting cryptocurrency wallets and service providers linked to terrorist organisations. Among the most widely publicised actions was the designation of Buy Cash, and individuals associated with its operations. This designation promoted extensive public discussion within the blockchain analytics community regarding the role of cryptocurrency in terror financing.
Leading analytics firms published analyses arguing that the overall scale of terrorist financing via digital assets was relatively limited compared to traditional channels, emphasizing that terrorist organizations primarily rely on conventional banking systems, informal cash networks, and hawala-based mechanisms. A recurring critique in this discourse focused on methodological weaknesses, particularly the tendency to attribute the full transaction volume of a service provider to a single sanctioned wallet, despite the pooled nature of exchange infrastructure and the presence of legitimate users.
While these critiques correctly identify risks of overestimation when relying solely on gross transaction volumes, subsequent enforcement actions, sanctions designations, forfeiture filings, and on-chain analysis over the past two years have revealed a more complex and evolving reality. Cumulatively, publicly documented cases now indicate that terror-linked cryptocurrency activity has exceeded one billion dollars, reflecting not isolated misuse but sustained, operational reliance on digital assets by certain actors.
Over this period, OFAC and the NBCTF have designated a broad network of entities and wallets linked to Hamas, Hezbollah, the Houthis and Iran’s IRGC, exposing interconnected financial infrastructures operating across Gaza, Lebanon, Yemen, Iran and affiliated regions. These designations have demonstrated that cryptocurrency has become an embedded component within broader terror financing architectures, rather than a marginal or experimental tool.
In Gaza, Hamas’ use of cryptocurrency appears driven primarily by necessity. Extensive sanctions, banking restrictions and international scrutiny have sharply limited access to formal financial systems, incentivising the adoption of digital assets as a means of maintaining inbound and outbound financial flows. Cryptocurrency enables rapid transfers, reduced reliance on regulated intermediaries, and continuity of operations when bank accounts are frozen, making it a structural element of Hamas’ financial resilience.
Blockchain analysis has also documented the use of humanitarian-themed fundraising campaigns to solicit crypto donations, often framed as emergency aid initiatives. While represented publicly as charitable efforts, on-chain tracing shows that funds collected through these campaigns were routed into wallets linked to Hamas financial operations, indicating dual-use or covert fundraising structures rather than purely humanitarian activity.
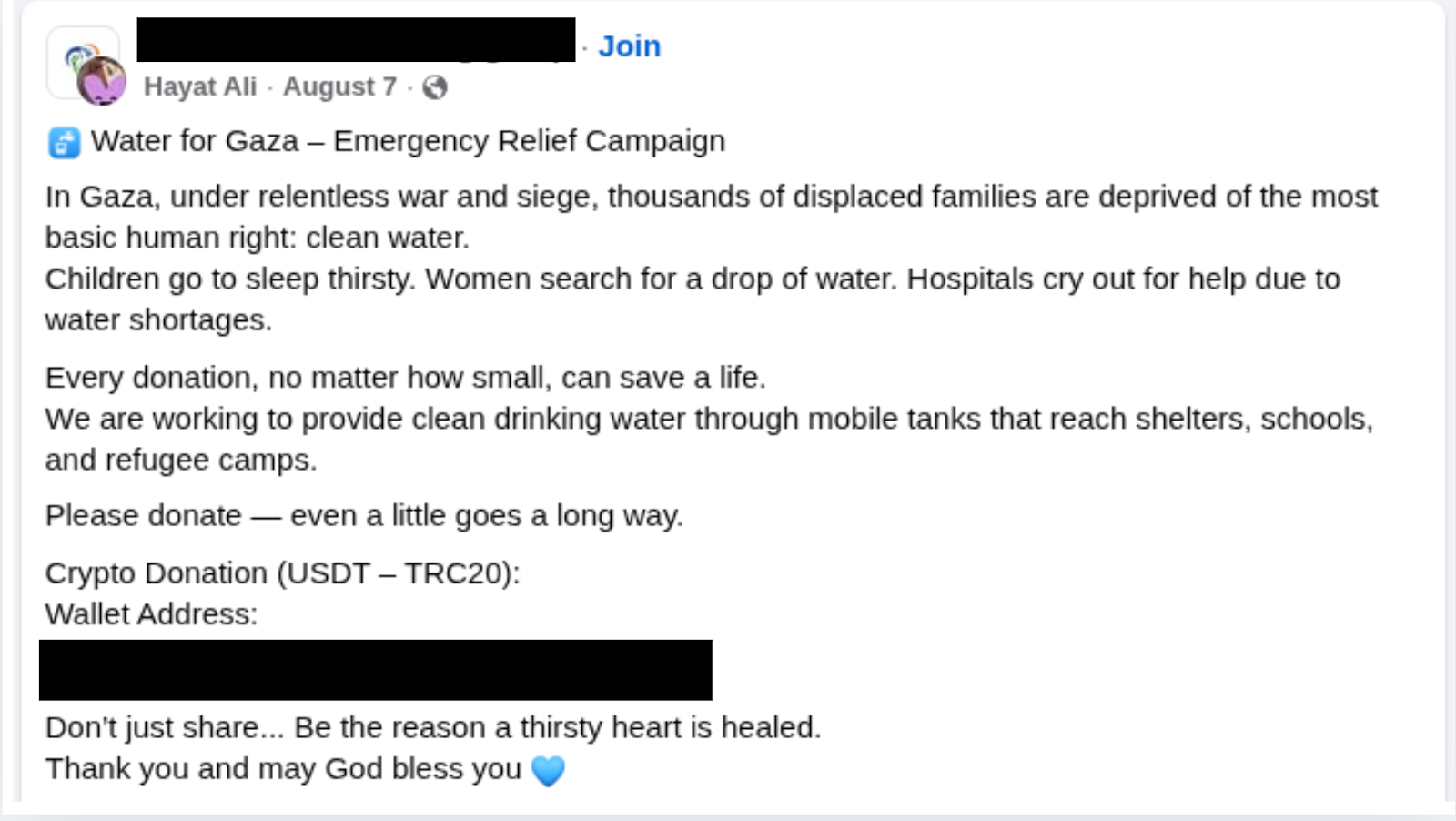
Alongside donation-based fundraising, Hamas has relied on institutional intermediaries, most notably Buy Cash, a Gaza-based money exchange and crypto conversion service. Buy Cash plays a central role in facilitating cryptocurrency flows into and out of Gaza and is examined in detail due to its repeated appearance in sanctions actions, forfeiture filings, and on-chain transaction trails.
Buy Cash presents itself as a cash-for-crypto service, but enforcement actions and transaction analysis indicate that it functions as a financial conduit closely integrated with Hamas’ funding mechanisms. Israeli authorities seized Buy Cash-linked wallets in 2021 in connection with Hamas fundraising, including wallets associated with the group’s military wing. Additional historical activity links Buy Cash infrastructure to transactions involving affiliates of al-Qa’ida and ISIS, reinforcing its repeated intersection with designated terrorist organizations.
Operationally, Buy Cash functions through a network of representatives controlling wallet clusters, conversion points, and customer channels. Its activity relies heavily on Telegram coordination, short-lived wallets, and repeated issuance of new addresses following sanctions actions. Multiple recurring email identities tied to Buy Cash operations appear across wallet registrations, Binance-linked accounts, and high-volume USDT flows, collectively moving tens of millions of dollars.
Named individuals associated with Buy Cash have been linked to ownership, operational control, and direct facilitation of high-risk crypto flows. On-chain evidence shows that Buy Cash-linked wallets exhibit transaction patterns consistent with known terror financing typologies, including rapid layering, mirrored inflows and outflows, and repeated interactions with Hamas, Palestinian Islamic Jihad, Iranian exchanges used for sanctions evasion, and IRGC-linked services. These names include Ahmed M. M. Alaqad, a central figure behind Buy Cash’s organisational and technical backbone, who appears to oversee the movement of funds from fundraising networks to Hamas’ military wing. Also included is Ahmed Y. A. Abughali, who appears to be the most active Buy Cash representative and executor behind Buy Cash high risk transactions. This individual in particular made efforts to evade enforcement after sanctions by creating a new working USDT address, address WGy.
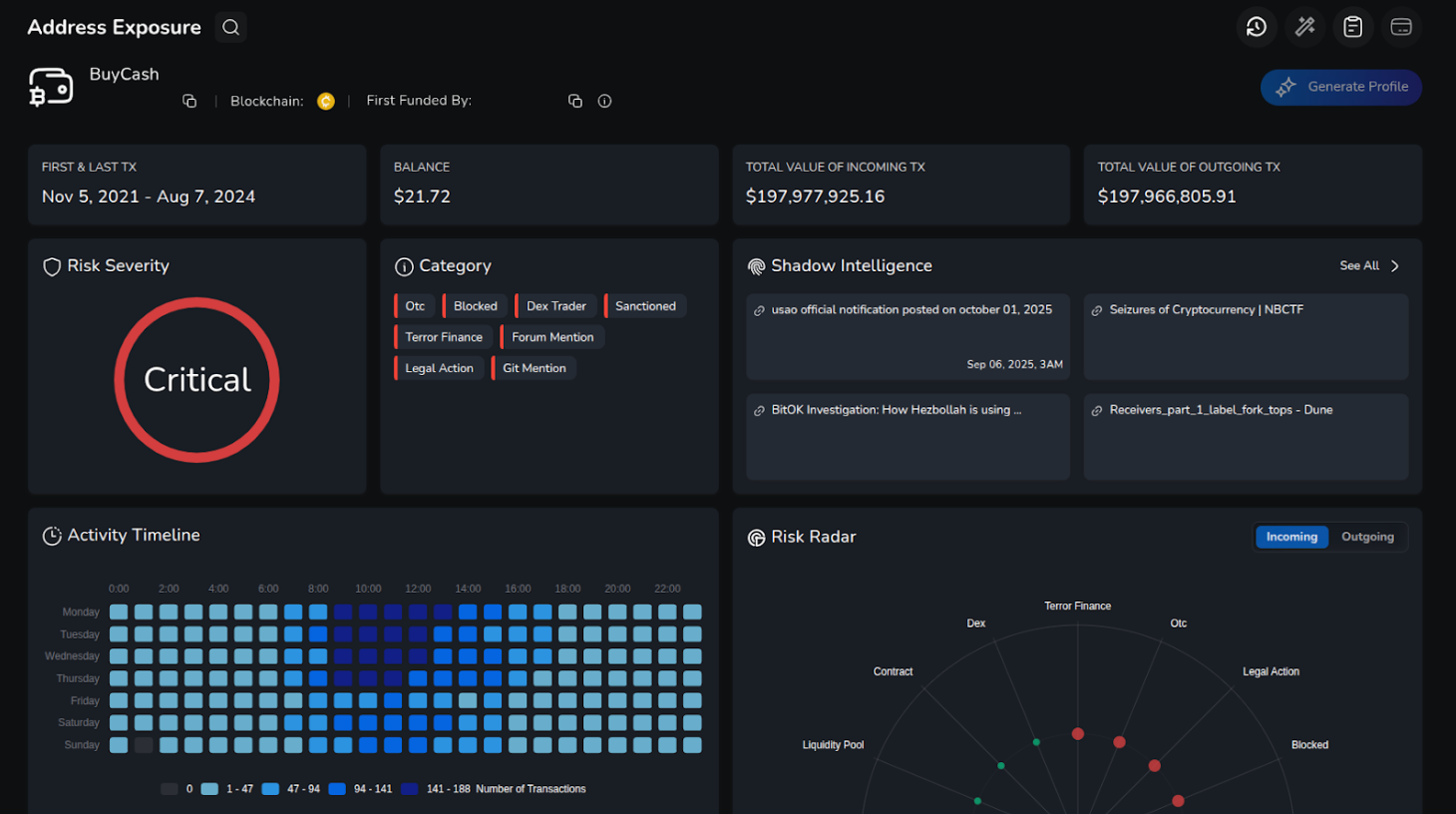
Despite sanctions, Buy Cash representatives continued issuing new wallet addresses and maintaining uninterrupted operations, indicating sustained access to crypto conversion services and deliberate adaptation to enforcement measures.
Buy Cash-linked wallets processed over $635 million on the TRON network, with the top ten wallets receiving approximately $230 million. From a broader economic perspective, Gaza’s financial environment is characterized by widespread poverty, extreme unemployment, and heavy dependence on humanitarian aid. Large-scale liquid wealth among civilians is statistically rare, and significant financial activity cannot occur independently of Hamas’ regulatory and administrative control.
Open-source sanctions data, forfeiture records, and blockchain analysis consistently identify Hamas and its affiliated facilitators as the only non-state actors in Gaza operating cryptocurrency and informal payment channels at multi-million-dollar scale. While it is not possible to categorically exclude isolated neutral actors, there are no documented cases of Gaza-based crypto operators handling comparable volumes outside of Hamas-aligned structures.
Over the past year, NOMINIS has worked with investigators and law enforcement agencies to map Gaza’s over-the-counter crypto infrastructure. This effort identified approximately 400 OTC-linked wallets that collectively processed hundreds of millions of dollars over time. The majority of these brokers demonstrated transactional exposure to Hamas-linked wallets, reinforcing the conclusion that large-scale crypto activity in Gaza is structurally intertwined with Hamas-controlled financial networks.
Analysis of the Binance Lawsuit
In late 2025, a landmark lawsuit, Balva v Binance, was filed in the US District Court for the District of North Dakota by 306 American plaintiffs, family members of those who were killed or injured in the OCtober 7 2023 Hamas attacks on Israel. The complaint alleges that Ninance, the world’s largest cryptocurrency exchange, its founder, Changpeng Zhao, and other senior executives, knowingly facilitated financial transactions for US (and internationally) designated Foreign Terrorist Organisations, including Hamas, Hezbollah, the PIJ, and Iran’s Islamic Revolutionary Guard Corps (IRGC). It argues that Binance’s platform enabled these groups to receive, move and conceal funds despite sanctions, compliance obligations, and repeated exposure of terror-linked wallets.
The lawsuit follows years of escalating regulatory scrutiny : in 2023, Binance entered a $4.3 billion plea agreement with US authorities for anti money laundering and sanctions violations, where CZ pleaded guilty, serving four months in prison before a controversial pardon earlier this year. Despite this enforcement action, the plaintiffs contend that Binance continued to process terror funds, reorganise infrastructure to evade oversight, and operate compliance controls that were weak or willfully inadequate.
From a forensic perspective, on-chain analysis reveals repeated interaction between wallets linked to designated terror actors and Binance internal deposit addresses. The lawsuit alleges that hundreds of millions of dollars in crypto value passed through Binance wallets associated with sanctioned entities, including flows that continued even after public reporting and enforcement actions.
This dynamic, terrorism networks seeking resilient funding channels and global exchanges offering deep liquidity, resonates with broader Middle Eastern financial threat patterns. Designated terror groups increasingly adapt to sanctions and traditional financial isolation by exploiting gaps in digital asset compliance, using trade-based, donation-driven, and decentralized mechanisms to sustain operations and logistics. In the Binance case, the plaintiffs argue that the exchange’s structural design, including weak KYC/AML, omnibus wallets, and off-chain transactions, functionally created a permissive environment for such abuse.
In our investigation, we examined 8,000 cryptocurrency wallets (not included in the Lawsuit itself) that have transacted with, or demonstrated behavioural proximity to, sanctioned terrorist-linked entities, including Hamas-affiliated operators such as Buy Cash, as well as Hezbollah’s and IRGC’s networks. Leveraging a combination of blockchain forensic analysis and off-chain intelligence, the NOMINIS Intelligence Team mapped inflows and outflows, timestamped transfers, counterparties and cross-entity exposures to identify transactional clusters across the Middle East and in some cases, South America. Several wallets reviewed remain active, indicating persistent operational capacity despite sanctions.
The methodology employed included wallet clustering and attribution using blockchain heuristics, off-chain data, common deposit/ withdrawal patterns, and proprietary techniques. This allowed the visibility of not only direct transactions but also extended networks of financial proximity among terror-linked actors.
Of the 8,000 wallets investigated, the investigations of 9 particular wallets were documented in entirety in the published report. These wallets have relationships with Hamas, Hezbollah, or the IRGC itself. The methodology described above allowed us to trace transactional proximity across networks, identify shared liquidity corridors, and surface exchanges of value between groups that would otherwise appear unconnected.
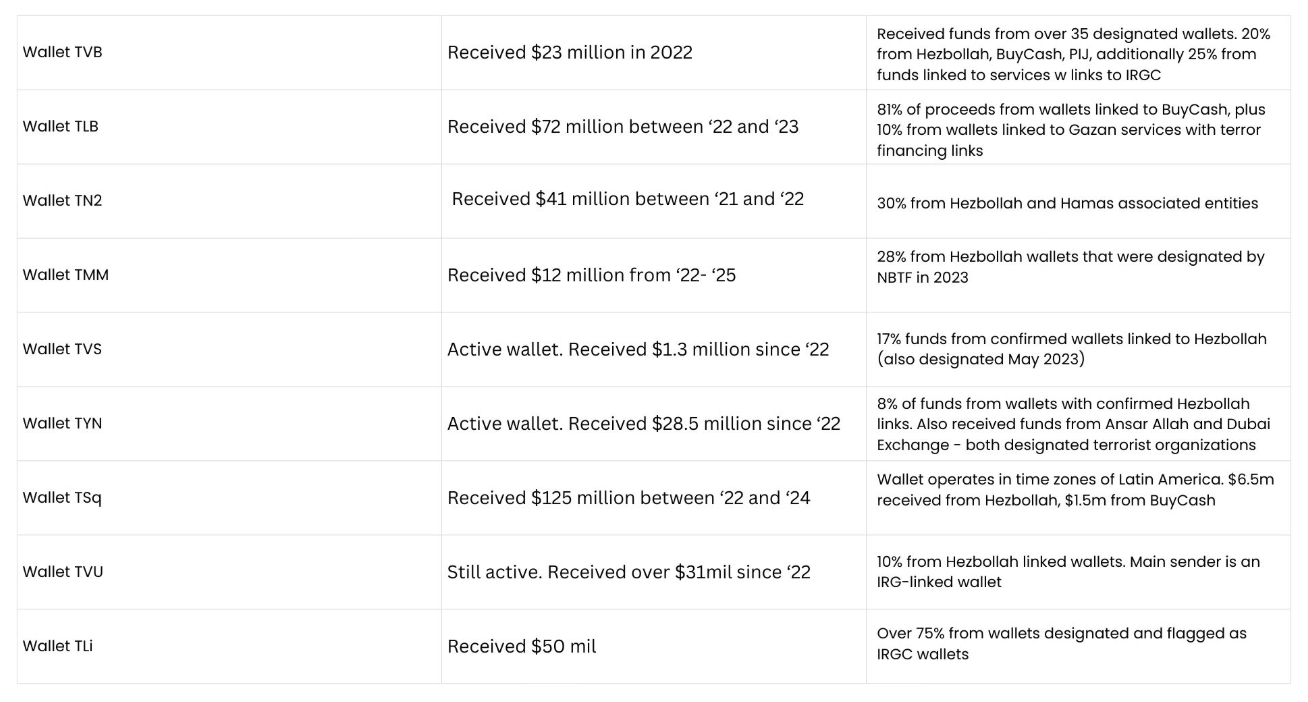
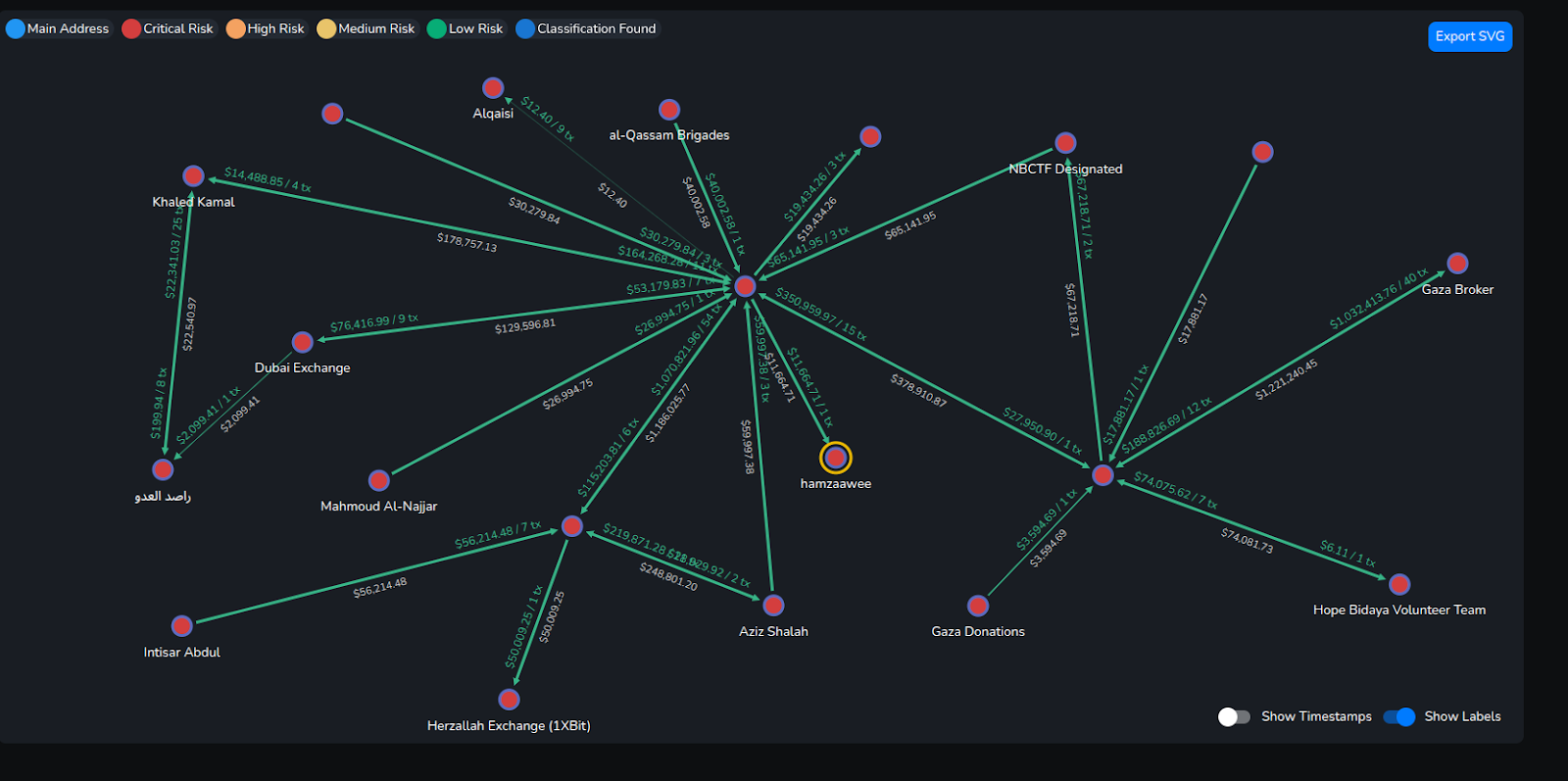
A primary focus was Buy Cash, a Hamas-linked exchange designated by the US following the attacks, discussed earlier. Buy Cash emerged as a central node in the terror-financing networks. Several wallet clusters displayed sustained interactions with entities associated directly or indirectly with Hamas, often connected to Hezbollah, IRGC-linked actors, and OTC desks with prior exposure to terror financing.
Wallet TVB is a key example, having received approximately $23 million in 2022, with over 20% of inflows from wallets later blocked due to associations with Hezbollah, Buy Cash, and PIJ. Further inflows included funds tied to Iran-related services and unnamed OTC desks linked to terror financing. Historical evidence reinforces Buy Cash’s operational role in Hamas fundraising and terror finance: NBCTF seizures in 2021 traced wallets to Hamas military operations, and previous transactions link Buy Cash to al-Qa’ida affiliates.
Two other Buy Cash-connected wallets, Wallets TLB and TN2 received significant inflows: TLB received $72 million (81% from Buy Cash-linked wallets) and TN2 received $41 million, with ⅓ from Hezbollah and Hamas sources. Collectively these patterns demonstrate how Buy Cash functions as a central financial conduit, linking Hamas, Hezbollah, IRGC, and broader terror-financing networks through virtual assets.
Another cluster of wallets revealed strong transactional alignment with Hezbollah funding structures, including Wallets TMM, TVS, TYN, TSq, and TVU. For example, Wallet TMM received $12 million over four years, with 28% from Hezbollah-designated wallets, yet Binance did not freeze the account. Wallet TVS remain active, having received %1.6 million, 17% of which came from Hezbollah-linked sources. Wallet TYN received $28.5 million, including funds from Hezbollah, Ansar Allah (Houthis) and Gaza-based exchanges connected to terror financing.
Two particularly notable wallets (Wallet TSq and Wallet TVU) illustrate cross-regional operations, linking Hezbollah’s financial networks to Latin American narcotics traffickers. TSq received over $125 million in 20 months, including $6.5 million from Hezbollah, and $1.5 million from Buy Cash, with activity spanning both Iranian and LATAM business hours, suggesting coordinated international operations (further discussed below). TVU received $31 million, over 10% from Hezbollah-linked wallets, with major inflows from an IRGC-associated wallet.
IRGC-linked wallets displayed consolidated patterns of value aggregation and redistribution across exchanges, including Binance. Wallet TLi received over $50 million from 2023-2025, more than 75% originating from designated IRGC wallets. This demonstrates that even under extensive sanctions, IRGC actors were able to access liquidity and engage in large-scale operational finance via crypto currency channels.
Our Key observations:
- The activity across these wallets are persistent, structured and cross-regional, linking the Middle East, Latin America and Iran-aligned regions.
- Exchanges may be responsible for the gap between government designations and enforcement.
- Terror linked actors integrate cryptocurrency into broader financial operations, blending it with ‘hawala’ networks, cash movement, criminal income streams, OTC channels, and global liquidity brokers. Crypto is acting as an accelerator and amplifier of traditional terror-financing mechanisms.
- Across just nine highlighted Binance wallets approximately $130 million of the $383.8 million received, ~30%, originated from terror-linked sources, underscoring the magnitude of the exposure.
The findings presented in our analysis of the Binance Lawsuit, as it stands, were intended to contribute measurable on-chain evidence to the broader discussion surrounding the allegations raised in the complaint. The analysis focuses on observable transaction behavior, the scale of fund flows, the persistence of activity over time, and the structural patterns through which value moved across wallets, services and regions.
By examining timestamped transactions, wallet interactions, clustering behavior and cross-network exposure, the investigation documents how cryptocurrency wallets linked to Hamas, Hezbollah and the IRGC continued to interact with Binance-associated deposit addressees, including after public designations and seizure actions by relevant authorities. These observations provide empirical context for understanding how illicit financial activity may operate within digital asset ecosystems, independent of legal interpretation.
Importantly, the data highlights the durability and adaptability of terror linked financial networks. On-chain evidence shows that such activity can persist cross jurisdictions, leverage exchanges and OTC services as liquidity and conversion points, and maintain operational continuity even under sanctions pressure. While on-chain analysis cannot determine intent or compliance decision-making, it can illuminate transaction pathways, exposure chains, and systemic risk patterns that are relevant to regulators, investigators and compliance stakeholders.
Taken collectively, these findings underscore the value of blockchain analytics as a tool for documenting risk exposure and financial behaviour at scale. They also demonstrate how empirical on-chain data can inform ongoing legal, regulatory, and policy discussions by grounding them in verifiable transaction activity rather than inference, or speculation.
Analysis of the Hezbollah-Cartel Crypto Pipeline
Recent investigations by the NOMINIS Intelligence Team have revealed a striking financial nexus between Iran’s Islamic Revolutionary Guard Corps (IRGC), its proxy Hezbollah, and Latin American drug cartels, including the Sinaloa Cartel, Jalisco New Generation Cartel (CJNG) and even gangs like the MS-13. The LatAm pipeline suggests that these groups have been using cryptocurrency to move illicit proceeds across continents.
What initially may have appeared as isolated on-chain movements have revealed a deeper pattern: wallets connected to the Middle Eastern militant networks interacting with addresses linked to Sinaloa, CJNG and MS-13; this connection reflects a growing trend in which terrorist organisations and cartel groups reply on one another’s strengths, using cryptocurrency as a bridge that enables fast, discreet and cross-border financial collaboration.
Terrorist organisations such as the IRGC and Hezbollah typically collect funds through a mixture of state sponsorship, donations, extortion networks, front companies and revenue from controlled territories. However, sanctions and global pressure have pushed them to reply increasingly on alternative financial channels. Cryptocurrency provides exactly what they need: an ability to move value internationally without relying on traditional banking systems that monitor, report, or block their transfers. For these groups, crypto is not simply a convenience but a strategic necessity.
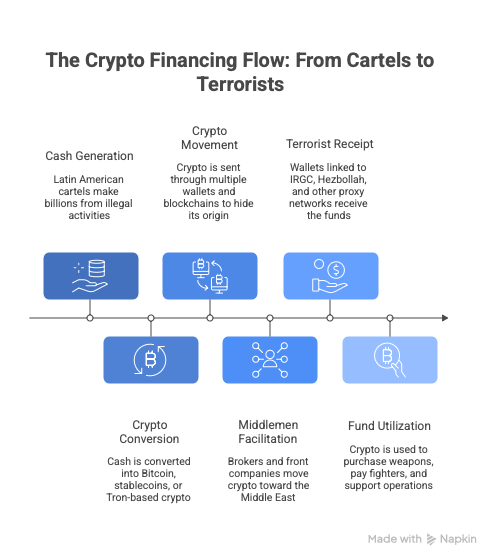
On the other end of the network are the Latin American cartels, whose financial structure is built on enormous volumes of illicit cash. Groups like the Sinaloa Cartel, CJNG and MS-13 generate billions through cocaine, methamphetamine, fentanyl and human trafficking operations, which then must be laundered and integrated into the global financial system. The US State Department explicitly describes these cartels as highly sophisticated money laundering organisations, capable of moving vast revenues through a combination of bulk cash smuggling, shell companies, and digital assets. The speed, borderless nature and decentralization of crypto makes it ideal for converting physical drug proceeds into digital value.
This overlap of needs creates a natural incentive for collaboration. Terrorist groups need access to liquid capital outside beyond the reach of sanctions, while cartels need partners who can move or store value outside the traditional finance system. Further external investigations demonstrate schemes moving drug profits through Syrian financial intermediaries before reaching the Middle East, which illustrate how integrated these networks have become.
In essence, both sides benefit enormously from this arrangement. Terrorist groups gain access to one of the world’s most profitable criminal economies, while cartels gain a politically protected partner that can offer covert networks, global contracts, and routes inaccessible to ordinary criminal syndicates. Cryptocurrency acts as the perfect facilitator for this convergence.
The revelation of a coordinated crypto-financing pipeline between Middle Eastern militant groups and Latin American cartels underscores a fundamental shift in how transnational threats operate. What once existed as siloed criminal enterprises; drug trafficking in Latin America, and extremism and terrorist activity in the Middle East, has evolved into a globalised system where actors cooperate when it benefits their operational and financial interests.
The IRGC-Hezbollah- Cartel axis is not just a threat, but a proof of concept. It demonstrates how state-backed terrorist organisations can merge with profit-driven criminal syndicates to create financial channels resilient to sanctions, border controls, and international oversight. If these groups can do it, it proves others can too. Nowhere is this more evident than Pyongyang, the capital of the world’s most aggressive and prolific state actor in crypto-enabled crime. Rather than a tool of convenience, for North Korea, crypto is a state survival mechanism, responsible for funding nuclear programs, ballistic missile development and the regime’s internal elite economy.
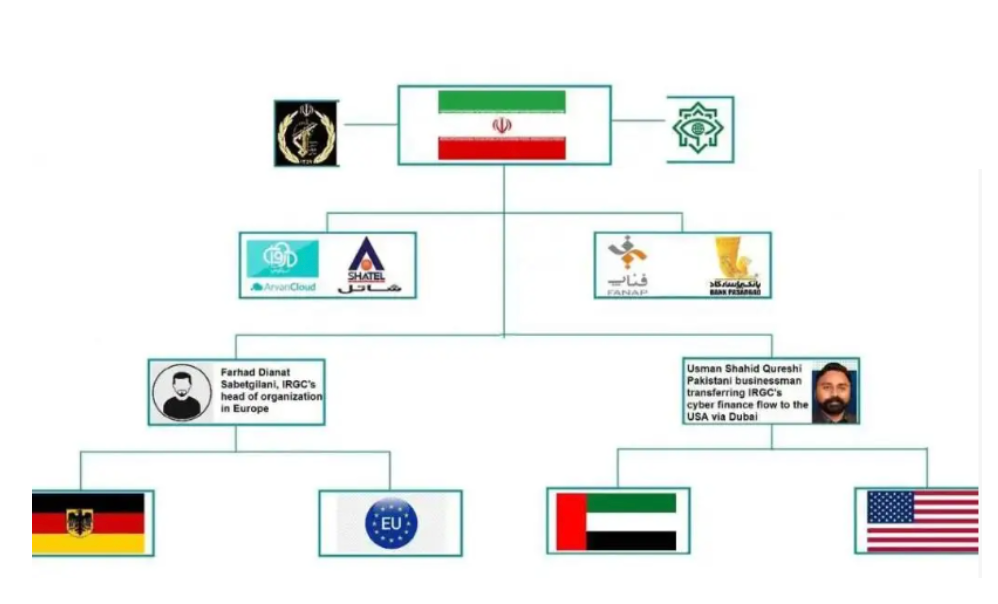
IRGC use a variety of methods to obtain finances despite sanctions, both in and out of Iran
IRGC financing via Oil
In 2025, NOMINIS identified and mapped an industrial-scale Iranian sanctions-evasion and terror-financing pipeline centered on Sa’id Ahmad Muhammed Al-Jamal, a long-designated IRGC-linked oil broker, and cryptocurrency facilitators Alireza Derakhshan and Arash Estaki Alivand. This network converts Iranian oil revenues into deployable cryptocurrency liquidity, bypassing traditional financial oversight through maritime obfuscation, shell companies, and layered documentation.
On-chain analysis conducted using our software revealed that between 2023 and 2025, hundreds of millions of dollars flowed through wallets linked to the IRGC, the Houthis, and associated facilitators, including over $190 million through an IRGC-linked wallet and significant volumes through wallets attributed to Al-Jamal, Derakhshan, and Alivand. These funds were primarily converted into high-liquidity digital assets such as USDT across Ethereum and TRON networks, enabling rapid, low-visibility cross-border transfers.
NOMINIS’ intelligence demonstrated how digitized oil proceeds were funneled into procurement and operational wallets supporting the IRGC-Quds Force and proxy groups including Hezbollah and the Houthis, enabling sustained militant activity without reliance on regulated banking channels. This use case illustrates Iran’s evolution from state-budget financing to a resilient shadow-economy model combining illicit oil trade, offshore corporate structures, and cryptocurrency, highlighting the critical role of advanced transaction monitoring in detecting and disrupting hostile state and terror-financing networks.
IRGC Crypto laundering via London-Based Exchanges: Zedcex and Zedxion
In parallel to activity observed across Middle Eastern OTC networks and major global exchanges, a separate NOMINIS investigation uncovered an IRGC-linked cryptocurrency laundering operation operating through two London-registered exchanges: Zedcex and Zedxion. This case illustrates how IRGC-affiliated actors leverage Western-facing corporate entities and regulatory jurisdictions to access liquidity, legitimacy, and global crypto rails.
The investigation identified multiple cryptocurrency wallets with direct and indirect exposure to designated IRGC entities that routed funds through Zedcex and Zedxion infrastructure. On-chain analysis revealed sustained transaction flows amounting to millions of dollars, including repeated interactions with wallets previously linked to Iranian sanctions evasion, terror financing facilitators, and regional proxy networks. These wallets exhibited classic laundering typologies, including value aggregation from multiple sources, rapid internal transfers, and onward movement into high-liquidity stablecoins such as USDT.
Critically, these exchanges were registered and operated from the United Kingdom, underscoring how jurisdictional credibility and corporate registration can be exploited to mask high-risk activity. Rather than relying solely on informal or opaque regional channels, IRGC-linked actors demonstrated the ability to embed themselves within regulated or semi-regulated crypto service providers, enabling access to global liquidity while reducing friction and suspicion. Our intelligence was featured in the Washington Post’s report, found here.
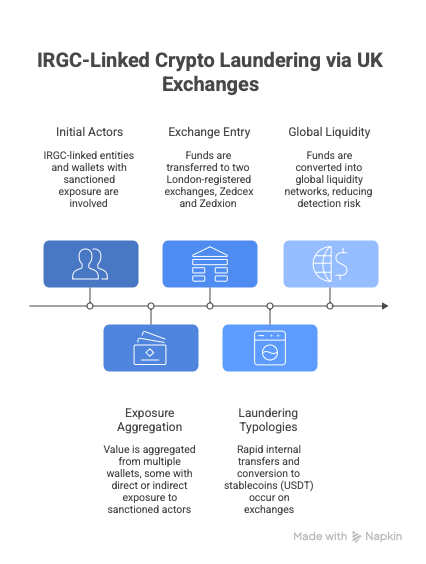
The Zedcex and Zedxion case highlights a recurring structural vulnerability: the gap between regulatory registration and effective transaction-level enforcement. While exchanges may meet baseline corporate or licensing requirements, insufficient KYT controls, weak wallet screening, and delayed response to sanctions exposure allow hostile state actors to operate within otherwise legitimate financial ecosystems.
This investigation reinforces a central conclusion of NOMINIS’ broader Middle East findings: IRGC crypto activity is not opportunistic or isolated, but systematic, adaptive, and operationally mature. By combining regional OTC networks, global exchanges, and Western-registered platforms, IRGC-linked financial actors maintain resilient access to cryptocurrency liquidity despite extensive international sanctions. For regulators, exchanges, and compliance teams, this underscores the necessity of continuous, intelligence-driven transaction monitoring that extends beyond surface-level compliance and into behavioural and network-based risk detection.
Spotlight on North Korea
North Korea remains one of the most sophisticated and persistent adversaries in the illicit finance landscape. Unlike many hostile states that separate revenue generation, intelligence operations and weapon procurement, North Korea integrates these functions, using cybercrime and digital asset exploitation as direct funding mechanisms for its nuclear and missile programs. This means that shifts in the regime's cyber tactics often reflect real-time pressure points in its weapons financing pipeline.
Over the past year, NOMINIS has played a leading role in uncovering, contextualising, and warning about these shifts. Our research has traced how North Korea has evolved from traditional laundering networks into more agile, digitally embedded operations, leveraging DeFi infrastructure, insider infiltration of Web3 projects, and highly personalised deep-fake enabled social engineering attacks.
Crucially, the work we published did not simply document incidents once they became public. We identified these patterns early, often months before formal sanctions or indictments were announced.
This early visibility was made possible through the integration of three key elements:
- Behavioural network analytics within our platform via the GeoInt tool, which surfaced clusters of wallet activity and laundering patterns
- Continuous intelligence collection from a variety of sources, including the deep and dark web, and 24/7 monitoring, linking newly observed wallet behaviour to previously attributed North Korean cyber units
- Contextual geopolitical and threat-finance analysis, allowing us to interpret these signals as strategic adaptation rather than isolation cybercrime events.
It is this analytical fusion that enabled NOMINIS to warn, ahead of OFAC actions, that North Korean operators were shifting from large exchange hacks, to high-value targeted social engineering attacks, impersonating friends of founders using deep-fake video calls and Telegram-based relationship-building strategies.
When the sanctions eventually arrived, they confirmed what our research has already made clear: these tactics were not opportunistic crime, they are part of state-driven effort to destabilise revenue streams under heightened international pressures.
An extension from Large-Scale Exchange Breaches, to Targeted, Relationship-Driven Attacks on High-Value Individuals
North Korean-backed operations throughout 2025 have demonstrated a tactical shift: Lazarus and affiliated actors continue to exploit high-yield opportunities at centralized venues, but increasingly favour smaller, relationship-driven intrusions that directly target high-value individuals and DeFi projects.
Large, lucrative breaches, most prominently the Bybit compromise (February 2025, $1.4 billion) demonstrate that exchanges remain exceptionally profitable and are still actively pursued. However, 2025 saw a growing share of suspected North Korean activity now involving phishing, social-engineering and trust-based vectors, such as Telegram interactions or mutising/phishing for protocol signage, to compromise founders, whales and custodial keys.
Examples include John-Paul Thorbjornsen, the Thorchain founder who experienced a wallet drain of $1.35 million in September 2025, and Kuan Sun, the Venus Protocol whale who was attacked for $13 million, before recovering the funds.
The year also saw several DeFi / launchpad private-key compromises, such as Seedify on 23 September .
This dual approach, continuing large CEX strikes while simultaneously moving ‘down the stack; to exploit human relationships, compromised developer infrastructure, and single-wallet weaknesses, both diversified the attackers revenue streams and reduced detection risk, since targeting intrusions are harder to spot and trace than mass heists.
Greater Efforts to Infiltrate Crypto Entities to Insert Malware and Gain Insider information
NOMINIS research has identified a sharp escalation in the regime of North Korea, moving beyond hacks to obtain cryptocurrency for Proliferation Financing, but also targeted infiltration into Western crypto entities. Our insights exposed how state-backed operatives pose as Web3 developers, secure roles with falsified credentials, access critical systems, and siphon both earnings and project-intelligence back to North Korea.
These findings corroborate with external reports that North Korean cyber-spies established facade US Firms, such as Blocknovas LLC and Softglide LLC, to lure crypto-developers into malware-laden engagements and deploy hostile code from within. The result is a dual threat - not only is intellectual property and credential access compromised, but malicious code inserted via legitimate channels create a conduit for sanctions-evading finance and provide covert entry points for otherwise secure organisations.
In this context, compliance frameworks like AML/CTF programs become frontline defences. Through transaction monitoring, it is possible to track payments tied to fictitious employment structures, detecting unusual behaviour before full exploitation.
Spotlight on Russia
Russia represents a distinct case in the illicit finance landscape. In the wake of sweeping sanctions, restricted international banking access, and sustained geopolitical isolation, Russia has increasingly turned to a cryptocurrency and alternative payment infrastructure to maintain financial continuity. Crypto, in this context, is not simply an investment or speculative asset class; it has become a functional component of the country’s economic resilience strategy, used by both state-aligned actors and wider criminal ecosystems to preserve liquidity, transact across borders, and finance operations beyond the reach of formal insight.
This financial environment operates alongside, and is reinforced by, a well established Russian-language dark-web ecosystem. Ransomware groups, illicit marketplaces, money laundering networks and bulletproof hosting services have deep cultural, technical and infrastructural roots in the region. These networks frequently interface with digital-asset payment flows, creating blurred boundaries between cybercrime, state-linked activity and sanction evasive finances.
Continued Dependence on Crypto as a Sanctions Workaround
As access to traditional international rails remains limited, Russia expanded its reliance on cryptocurrency as a strategic alternative. Beyond direct wallet usage, our research highlighted how domestic payment systems such as MIR Pay are being used as high-risk fiat on-ramps into crypto, allowing funds to move from the ruble environment into digital assets with minimal friction.
In our investigation concerning MIR Pay, we outlined how QR-based payment flows, OTC brokers, and cross-border P2P conversion channels are enabling sanctioned users and intermediaries to shift value while avoiding controls that would typically be triggered in traditional banking environments. This demonstrates that the threat surface is no longer limited to where funds end up, but how they get there.
A persistent and embedded dark-web eco system enabling illicit financing
Russia’s darknet ecosystem remains deeply interconnected with ransomware operators, illicit marketplaces and cryptocurrency-based laundering services. These networks are not peripheral; they form part of the broader infrastructure through which sanctioned actors and cybercriminal entities transact, store value, and finance ongoing operations.
Nominis highlighted this infrastructure layer in research into the Aeza Group, a Russian-based bulletproof hosting provider. In our publication of the investigation, we mapped the wallet behaviour associated with Aeza’s hosting operations, demonstrating clear transactional connectivity to Russian-language darknet marketplaces and ransomware-linked entities. Critically, we identified additional wallet addresses that ought to be sanctioned, alongside those that had already been identified by OFAC.
In both cases, whether through alternative payment rails such as MIR Pay or infrastructure providers like Aeza Group, the Russian illicit finance landscape shows how crypto, darknet ecosystems and sanctions evasion are now structurally linked. Our investigations in this space have focused on identifying these enabling networks early, translating complex behavioural and infrastructural patterns, into actionable, pre-emptive risk controls for compliance and investigative teams.
With this foundation established, our next priority is to ensure that organisations are equipped to understand and respond to these evolving threats in practice.
Identifying High Risk Jurisdiction Wallets through Geolocations
Nominis’ 2025 research uncovered a striking pattern in user geolocation behavior: many Iranian users appear as U.S. or German traders on centralized exchanges. In reality, these users routinely access platforms through VPNs and proxy networks, masking their true origin behind jurisdictions perceived as low risk and highly regulated. This trend creates false comfort for compliance teams that still rely on IP-based location checks or country filters as primary risk indicators. What appears to be a benign U.S. or EU user session can, in fact, represent activity from a sanctioned jurisdiction.
This finding highlights why geolocation intelligence must evolve beyond static IP data.
Effective monitoring requires combining IP analysis with behavioral and network telemetry, looking at:
- Proxy and VPN detection through ASN anomalies, latency patterns, and known exit-node databases.
- Correlation with on-chain wallet behavior, such as interaction with flagged addresses, mixers, or previously exploited contracts.
- Contextual risk weighting, where a “U.S.” IP linked to high-risk transactions triggers enhanced due diligence rather than blind trust.
Modern compliance demands multi-layered location intelligence, not checkbox geofencing. Geolocation should be treated as an enrichment layer that validates, or contradicts, other signals, not as a standalone control.
Hence, our integration of session-level telemetry, device signals, and wallet intelligence to identify mismatches between where users claim to be and where their activity truly originates. This approach transforms raw IP data into actionable insights, empowering exchanges to detect sanctions evasion and cross-border laundering patterns that would otherwise remain invisible.
The Growth of the Nominis Terror Financing Database
2025 saw NOMINIS undertake one of its most ambitious intelligence initiatives: the creation of the largest known Crypto Terror Financing Database. Built through close collaboration with law enforcement agencies, investigative partners, and select private-sector initiatives, the database consolidates years of fragmented intelligence into a unified and operationally valuable source. This effort was made possible by another major milestone reached this year: the clustering of over 1 billion crypto wallets across multiple chains, dramatically expanding the granularity ouf our attribution capabilities.
Over the course of the year, our dedicated task force successfully identified and flagged thousands of wallets connected to OTC (Over the Counter) brokers, facilitators and individuals either directly controlled by, or strongly affiliated with, terrorist organisations. Each wallet was verified through a combination of on-chain behavioral analytics, cross-chain network tracing and off-chain intelligence, ensuring both precision and evidentiary robustness.
The scope of exposure through this project is significant, as we detected indirect contagion across banks, payment processors, exchanges and smaller digital services, many of which were unknowingly transacting with, or provided infrastructure to, terror linked entities.
This database serves as a cornerstone for both strategic intelligence and operational defence, empowering our partners to screen, monitor and block terror-associated wallets in real time, while also adapting, given the evolving nature of terrorist organizations we aim to combat.
Terror Finance Prevention through Education
Education and awareness remain critical tools in the fight against crypto-based terror financing. Over the past year, Nominis has partnered with dedicated professional bodies, including the Association of Certified Anti-Money Laundering Specialists (ACAMS) to provide targeted guidance to compliance officers, investigators and financial institutions.
Our webinar with ACAMS, we explored the full scope of terror financing, emphasizing that it extends well beyond the procurement of weapons. Funding often supports training, travel, propaganda, recruitment, and operational infrastructure. Understanding these broader objectives is essential for effective detection and intervention.
Our presentation also highlighted the unique characteristics of terror financing on the blockchain. These included seemingly legitimate fundraising campaigns disguised as charitable contributions, individual donations, and transfers purporting to support humanitarian aid. For example, certain ‘fronting’ charities have been used to channel funds to Gaza or Lebanon, while masking transfers to militant wings.
Education and awareness remain as critical tools in the fight against crypto-based terror financing. Over the past year, NOMINIS has partnered with dedicated professional bodies, including the Association of Certified Anti-Money Laundering Specialists (ACAMS) to provide targeted guidance to compliance officers, investigators and financial institutions.
Through a dedicated webinar, together with ACAMS, we explored the full scope of terror financing, emphasizing that it extends well beyond the procurement of weapons. Funding often supports training, travel, propaganda, recruitment and operational infrastructure. Understanding these broader objectives is essential for effective detection and intervention.
Our presentation also highlighted the unique characteristics of terror financing on the blockchain. These include seemingly legitimate fundraising campaigns disguised as charitable contributions, individual donations, and transfers purporting to support humanitarian aid. For example, certain ‘fronting’ charities have been used to channel funds to Gaza or Lebanon, while masking transfers to militant wings.
To differentiate legitimate campaigns from illicit activity, we outlined a methodology based on transaction monitoring, source tracing, and contextual analysis. Key indicators include unusually high inflows or outflows, anomalous geographic patterns, and intermediary wallets that function as financial bridges, connecting unwitting donors to actual terror-linked wallets. Identifying these intermediary nodes is vital, as they enable terror financing networks to operate covertly and sustain their operations over time.
By equipping institutions with this knowledge, Nominis strengthens the broader ecosystem’s capacity to recognise, assess and disrupt terror financing activity. Collaborations with associations like ACAMS amplify this impact, ensuring that education translates into operational vigilance, enhanced compliance, and more robust transaction monitoring frameworks.
Through these initiatives we demonstrate that technology alone is not sufficient: combining intelligence, analytic tools, and education, is essential to safeguarding the financial system from abuse by terror networks.
NOMINIS Exchange Infrastructure Analysis
Throughout 2025, Nominis’ investigations revealed a clear shift in illicit crypto activity, moving away from isolated abuses and toward the structural exploitation of legitimate infrastructure. This pattern is reinforced by high-profile cases, including the Binance lawsuit, in which the platform allegedly continued to facilitate the movement of funds between known illicit actors. Rather than relying on novel techniques, threat actors increasingly leveraged the design, speed, and jurisdictional gaps of existing crypto systems to scale their operations while minimizing detection risk.
In response, Nominis prioritized a deep examination of the evolving risk architecture of crypto exchanges, focusing not on individual incidents, but on the structural design choices that consistently enable illicit finance. Our research concentrated on three interrelated exchange models: instant swap platforms, nested exchange infrastructures, and offshore or no-KYC exchanges. Each represents a distinct layer of exposure, yet together they form a continuous laundering pathway, enabling sanctions evasion, post-exploit fund movement, and anonymized value extraction across the digital asset ecosystem.
The findings summarized below draw on hundreds of on-chain traces, OSINT reviews, and exchange-by-exchange comparative assessments conducted throughout 2025, highlighting the most consequential structural trends observed across exchanges, wallets, and transaction flows.
In the sections that follow, Nominis spotlights the key structural trends shaping illicit finance in 2025: transaction speed as a laundering vector in instant exchanges, compliance infrastructure repurposed as a proxy layer in nested exchanges, and jurisdictional arbitrage at scale in offshore and no-KYC platforms.
Spotlight on Instant Exchanges
Transaction speed emerged as a primary laundering vector, allowing illicit funds to move faster to avoid detection.
Throughout 2025, instant exchanges increasingly occupied a critical position in post-exploit and post-sanctions laundering chains. While often framed as neutral tools for fast asset conversion, their architectural design, particularly when paired with the absence of Know-Your-Customer (KYC) requirements, has made them a recurring feature in investigations involving stolen, sanctioned, or otherwise tainted funds.
These platforms market themselves on radical simplicity. Users are invited to select two assets, transmit funds, and receive the swapped currency within minutes. There is no account creation, no identity verification, and no waiting period. From a usability perspective, this model lowers barriers to entry. From a financial crime perspective, it collapses the time window in which exposure can be identified, attributed, and disrupted.
In practice, this compression of time has proven decisive. Our 2025 investigations confirmed that instant exchanges are routinely integrated into the earliest phases of laundering activity following DeFi protocol hacks, bridge exploits, and ransomware incidents. Funds are often routed through instant swaps within minutes of theft, well before public disclosures, sanctions alerts, or wallet flagging propagate across monitoring systems.
The Terra IBC exploit in 2024 offers a clear illustration. Despite the attacker’s wallet being publicly flagged, eXch.cx continued to accept deposits long after risk signals were available, enabling further conversion and dispersal of illicit funds. Similarly, analysis of the DeltaPrime exploit in November 2024 demonstrated how FixedFloat was immediately leveraged to convert stolen assets through rapid swaps and layered transactions, accelerating the transition from identifiable exploit proceeds to fragmented, harder-to-trace balances.
Beyond on-chain evidence, community discourse reinforces this pattern. Reddit threads, Telegram channels, and informal user forums consistently reveal a dual narrative. Retail users celebrate instant exchanges for their speed, convenience, and perceived neutrality. At the same time, blockchain investigators repeatedly encounter the very same platforms embedded within post-exploit laundering trails. This convergence highlights a structural tension: the features that drive legitimate adoption are the same features that make these services attractive to illicit actors.
Regulatory scrutiny intensified throughout 2025. Germany’s “Operation Final Exchange” and multiple OFAC sanctions designations targeted instant-swap operators with repeated exposure to darknet markets, exploit-linked wallets, and sanctioned entities. Yet enforcement has struggled to keep pace with adaptation. Many of these services remain operational under new domains, rebranded identities, or altered front-end interfaces, often sourcing liquidity through decentralized exchanges and peer-to-peer layers that lack consistent oversight.
In effect, instant no-KYC exchanges now operate as real-time laundering routers. They bridge the gap between on-chain exploitation and eventual fiat exit points, transforming stolen or sanctioned assets into liquid, mobile value at speed. Their criminal utility is not accidental; it is derived from the same characteristics that underpin their commercial appeal: speed, liquidity depth, and anonymity.
As long as transaction velocity remains unconstrained by identity, monitoring, or delay mechanisms, instant exchanges will continue to function as a first-response tool for illicit actors seeking to outrun detection in the moments immediately following compromise.
Spotlight on Nested Exchanges
Compliance infrastructure is increasingly repurposed by nested exchanges as a proxy layer, masking high–risk downstream activity
Compliance infrastructure was increasingly repurposed as a proxy layer, masking high-risk downstream activity.
Throughout 2025, Nominis identified nesting as one of the most structurally significant, and least visible, risks within centralized exchange infrastructure. Nesting, the practice of one exchange, broker, or third-party service operating through another exchange’s custodial environment, has evolved into a scalable method for laundering, sanctions evasion, and regulatory arbitrage.
Rather than interacting directly with end users, nested services process transactions on behalf of hundreds or thousands of downstream clients while relying on a small number of verified host accounts. This creates a synthetic compliance façade, where regulatory legitimacy is inherited rather than enforced, and where attribution of source-of-funds becomes materially degraded.
How Nesting Emerges in Practice
Our Nesting Exchange Risk investigation, which analysed proxy activity across more than 15 centralized exchanges, identified a consistent set of technical and behavioural indicators that enable nesting at scale:
- Weak or optional KYC, allowing nested services to aggregate many users under a single verified identity.
- Custodial wallet architectures, including shared deposit addresses and internal ledgers, that obscure individual fund ownership
Sub-account and API functionality, enabling automated routing of transactions on behalf of downstream clients - High withdrawal limits for unverified users, reducing friction for laundering large volumes
- Merchant and white-label tools, often used by OTC brokers or payment processors to mask the true origin of funds
These features, when combined, allow nested operators to function as parasite exchanges, embedded within compliant platforms while remaining largely invisible to standard transaction monitoring systems.
Licensing as a Structural Control, or Structural Gap
Licensing emerged as a decisive factor in nesting risk. Licensed exchanges are subject not only to KYC and AML requirements, but also to auditability, regulator engagement, and data-sharing obligations that materially constrain proxy abuse.
This contrast was evident in comparative assessments such as Kraken versus Bitget. Kraken’s multi-jurisdictional licensing framework enforces full KYC, maintains detailed audit logs, and actively detects proxy behaviour, making sustained nesting difficult. By contrast, offshore-registered platforms with no Tier-1 licenses face minimal external pressure to detect or disrupt nested services.
Our analysis of unlicensed or ambiguously licensed exchanges, including Yobit, HitBTC, Bitglobal, Cryptomus, and Coinsbit, revealed repeated indicators of proxy behaviour, such as address reuse across unrelated services, OTC-style aggregation flows, and merchant tooling that enables fund commingling under a single account.
Without licensing, there is no regulator to compel remediation, no audit trail to reconstruct abuse, and no jurisdictional authority to enforce corrective action.
Custodial Architecture as an Enabler
Nesting is fundamentally a custodial risk. In custodial exchanges, users do not control private keys; the exchange does. This allows multiple services to share deposit addresses, reuse internal ledgers, and conduct “silent integrations” where third parties route client funds without disclosing their existence.
Nested services exploit this architecture to process transactions “on behalf” of downstream users while concealing true ownership and intent. In contrast, non-custodial platforms, such as DEXs, inherently resist nesting due to transparent wallet ownership and on-chain accountability.
Common tactics observed in 2025 included:
- API-driven master accounts controlling multiple sub-accounts
Address pooling across unrelated services - Internal transfers that never hit the blockchain
- Merchant wrappers that present as payment tools but function as proxy exchanges
These patterns consistently appeared on platforms offering broad API access, shared custody models, and weak source-of-funds attribution policies.
Asset Support and Withdrawal Limits as Risk Signals
Two additional indicators proved critical in identifying nesting-prone platforms: supported assets and withdrawal thresholds.
Exchanges supporting hundreds or thousands of tokens, particularly privacy coins such as Monero (XMR) or low-liquidity altcoins, provide nested services with multiple obfuscation paths. Funds are routinely layered through asset conversions (e.g., ETH → privacy token → stablecoin) before re-entry into major liquidity pools.
Similarly, high no-KYC withdrawal limits dramatically expand nesting capacity. Platforms allowing hundreds of thousands of dollars per day to be withdrawn without identity verification enable nested services to move millions weekly through just a handful of “clean” accounts, often staying just below KYC trigger thresholds.
Exchange-Level Risk Patterns
Applying these indicators across major platforms revealed clear structural risk tiers. Exchanges including Binance, KuCoin, Gate.io, MEXC, CoinEx, PrimeXBT, BingX, Zoomex, OKX, Bitget, and Cryptomus exhibit combinations of custodial architecture, API and sub-account flexibility, optional KYC, high withdrawal limits, and offshore or partial licensing that make them structurally attractive for nesting, regardless of stated compliance policies.
By contrast, platforms such as Crypto.com demonstrate that custodial exchanges can meaningfully reduce nesting risk through strict KYC enforcement, comprehensive licensing, transparent governance, and active controls against VPN or proxy access.
Geopolitical Exposure and Regional Demand
Geopolitical risk further compounds nesting exposure. Our regional mapping confirmed sustained usage of major exchanges across Russia, Iran, Turkey, China, and Pakistan, often via VPNs, P2P intermediaries, or non-sanctioned banking channels.
Certain recognised exchanges repeatedly appear across multiple high-risk jurisdictions, signalling both their popularity and their potential role as nesting hubs. In these environments, nesting enables sanctioned or high-risk actors to access global liquidity while remaining insulated from consistent regulatory oversight.
Why Nesting Matters
In effect, nesting converts compliant infrastructure into laundering-as-a-service, allowing illicit actors to scale activity without building their own exchanges or custody solutions. Because the abuse occurs inside otherwise legitimate platforms, it is often misclassified as normal exchange flow rather than proxy behaviour.
Addressing nesting risk requires structural interventions, not reactive enforcement. Licensing reciprocity, cross-exchange intelligence sharing, granular monitoring of API and sub-account activity, and KYT systems capable of detecting aggregation behaviour are essential. Without these measures, nesting will remain one of the most effective and least visible mechanisms for laundering and sanctions evasion in the crypto ecosystem.
Spotlight on Off-Shore and No-KYC Exchanges
Offshore exchanges increasingly relied on jurisdictional arbitrage as an operating strategy, allowing them to function at scale beyond the reach of consistent regulatory oversight.
The third category in our 2025 research focuses on offshore and no-KYC exchanges that continue to capture significant global transaction volume by positioning themselves outside traditional compliance frameworks. These platforms are not fringe actors. Collectively, they serve millions of users and process substantial value by leveraging anonymity, opaque corporate structures, and regulatory fragmentation across jurisdictions.
Our analysis of 18 platforms, revealed a striking degree of structural convergence. While branding, user interfaces, and marketing narratives vary, the underlying compliance posture and risk profile are remarkably consistent.
Across these platforms, identity verification is either minimal, optional, or deliberately deferred until transaction volumes exceed unusually high thresholds. In practice, this allows users to move significant sums without attribution, particularly when activity is distributed across multiple wallets or structured below triggering limits. For illicit actors, this creates a predictable operating environment in which exposure can be managed, delayed, or avoided altogether.
Ownership and governance opacity further compound this risk. Many of the reviewed exchanges are registered in offshore jurisdictions such as Seychelles, Belize, or St. Vincent and the Grenadines. These locations offer limited public disclosure requirements, weak enforcement mechanisms, and minimal regulatory pressure. In several cases, beneficial ownership information was unavailable or unverifiable, making accountability and enforcement extremely difficult even when illicit activity is identified.
From a technical perspective, the widespread use of custodial wallet systems introduces additional vulnerabilities. Users do not control their private keys, funds are pooled across shared infrastructure, and there is often no proof-of-reserves, independent audit, or transparent custody architecture. This not only enables internal obfuscation of fund flows but also creates fertile conditions for proxy activity, nested services, and silent third-party integrations operating behind a single platform façade.
User-reported data reinforces these structural concerns. Recurrent complaints across forums and review platforms describe frozen assets, unexplained account restrictions, and support channels that are either unresponsive or unverifiable. While such issues are often framed as customer service failures, they also reflect deeper governance gaps and a lack of enforceable consumer protections typical of offshore, lightly regulated environments.
Geographically, many of these platforms continue to operate openly in sanctioned or high-risk regions, frequently facilitating peer-to-peer crypto–fiat conversions. Countries such as Russia, Pakistan, and China remain heavily dependent on VPN access, informal intermediaries, and unlicensed services to reach global liquidity. This sustained demand creates a symbiotic relationship: users seek anonymity and access, while offshore exchanges supply infrastructure without meaningful regulatory friction.
Several entities in our dataset demonstrate direct or indirect exposure to sanctioned jurisdictions. Excoino’s activity within Iran and Kyrrex’s interactions with Russian-linked wallets are illustrative examples. These exposures are not incidental; they highlight how the offshore exchange model can accommodate sanctioned flows by operating in legal gray zones where enforcement is inconsistent or politically constrained.
Taken together, offshore no-KYC exchanges form the final unregulated layer of the global crypto ecosystem. They sit at the intersection of darknet markets, DeFi exploits, ransomware operations, and eventual fiat off-ramps, enabling the transition from illicit on-chain activity to real-world liquidity. Their persistence underscores a systemic challenge: as long as jurisdictional arbitrage remains viable, enforcement efforts in regulated markets will continue to be undermined elsewhere.
The continued operation and growth of these platforms reinforces the urgency of unified KYC standards, KYT-driven transaction monitoring, and coordinated cross-border enforcement. Without alignment across jurisdictions, offshore exchanges will remain a durable pressure point in the global fight against illicit crypto finance.
NOMINIS OSINT- Driven Insights
The breadth of NOMINIS’ OSINT work demonstrates how blockchain intelligence can illuminate both financial and operational threats. Across 2025, our investigations spanned the tracing of terror-linked cryptocurrency transactions to exchanges worldwide, as well as the analysis of real-world threats orchestrated through digital finance channels, such as copycat bomb threat emails demanding Bitcoin payments in the United States.
Although these cases differ in scale and immediate impact, they share a common thread: illicit actors leveraging digital infrastructure, whether to move funds, obfuscate ownership, or execute threats, within a partially pseudonymous environment. By combining on-chain analytics, wallet clustering, transaction flow mapping, and traditional OSINT, NOMINIS has been able to uncover operational patterns, attribute activity to actors, and provide actionable intelligence that informs law enforcement, financial institutions, and industry stakeholders.
This section highlights the dual scope of our OSINT approach: from tracking terror-linked financial flows to exposing sophisticated crypto fraud schemes, demonstrating the value of integrated intelligence in understanding and mitigating risk across the rapidly evolving crypto landscape.
Blockchain Intelligence in action: Investigating Bomb Threats Targeting US Synagogues
In the past year, NOMINIS leveraged its expertise in blockchain-focused OSINT to investigate a wave of copycat bomb threat emails targeting synagogues across the United States. These threats, which demanded Bitcoin payments, represented a complex intersection of digital extortion, antisemitic targeting, and cryptocurrency misuse. Through meticulous tracing of the Bitcoin addresses involved, analysis of associated wallets, and clustering of related activity, our team was able to identify operational patterns and provide actionable insights into the scope and mechanics of the threats.
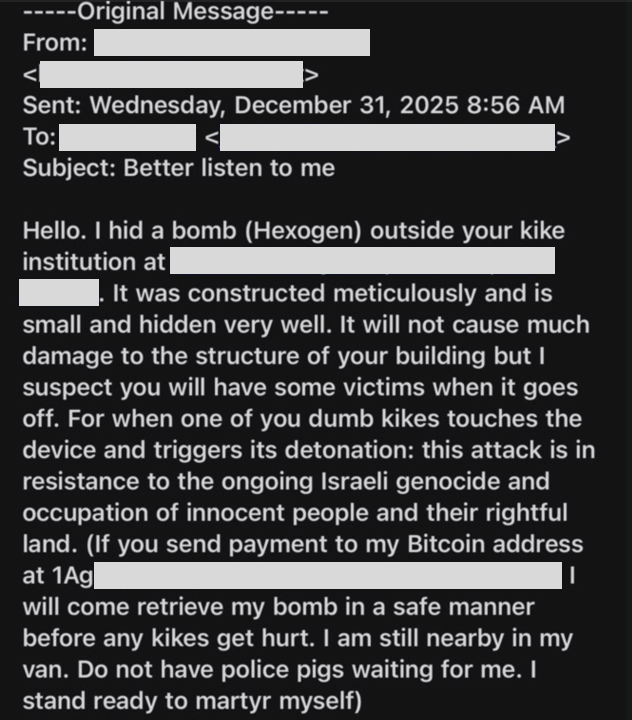
Our findings were significant not only for law enforcement and affected communities but also for the broader financial intelligence and OSINT ecosystem. The investigation demonstrated the practical value of blockchain OSINT: by following the flow of funds through pseudonymous networks, it is possible to map the digital infrastructure underpinning illicit activity, uncover links between actors, and inform both preventive and reactive measures.
The work conducted by NOMINIS in this case was subsequently cited and amplified by international news outlets, highlighting the broader societal impact of our efforts. This case exemplifies how blockchain OSINT can serve as a force multiplier for security agencies, journalists, and compliance professionals, bridging the gap between technical cryptocurrency analysis and real-world threat mitigation. Our contribution reinforces the role of specialized OSINT in understanding, contextualizing, and countering emerging threats in the crypto-enabled landscape.
Uncovering a Connected Web of Crypto Game Fraud: Epic Ballad and Legend of Constellations
In 2025, Nominis conducted an exclusive OSINT and on-chain investigation that revealed a previously unknown connection between two seemingly separate crypto gaming scandals: Epic Ballad, an NFT-based game operating as a Ponzi-style scheme, and Legend of Constellations (LOC), a play-to-earn project that ultimately executed a rug pull.
While both projects presented themselves as independent blockchain games targeting different regions and user bases, wallet clustering and behavioral analysis performed by Nominis demonstrated that the two operations were financially connected, strongly suggesting shared operators, infrastructure, or coordination behind the scenes.
This finding represents a critical example of how crypto fraud actors reuse wallets, funding paths, and laundering patterns across multiple projects, assuming that fragmented communities and surface-level analysis will prevent attribution.
Epic Ballad: A Ponzi Disguised as a Blockchain Game
Epic Ballad marketed itself as a blockchain-based NFT role-playing game, promising players yield generation, in-game rewards, and long-term token appreciation. In practice, the project’s economic model relied almost entirely on continuous inflows of new user funds rather than genuine gameplay revenue.
Key characteristics identified by NOMINIS included:
- Users were required to deposit stablecoins, which were internally converted into the project’s native token.
- Token liquidity, pricing, and withdrawal mechanics were fully controlled by insider wallets.
- Early participants could extract limited returns, funded directly by later entrants.
- The token contract retained centralized control, allowing the operators to manipulate supply and liquidity.
On-chain activity showed circular fund movements and artificial volume generation, creating the illusion of a healthy in-game economy while value steadily accumulated in wallets controlled by the project operators.
Legend of Constellations: A Classic Rug Pull Execution
Legend of Constellations (LOC) followed a more traditional play-to-earn trajectory. The project gained traction through NFT sales, token launches, and community-driven hype, particularly in Southeast Asian markets.
Unlike Epic Ballad’s slow Ponzi mechanics, LOC’s collapse was abrupt: Liquidity pools were drained, development activity ceased, social media channels went silent, and token value collapsed, leaving users unable to recover funds.
Public reporting correctly identified LOC as a rug pull. However, until NOMINIS’ investigation, the project was treated as an isolated incident, disconnected from other gaming-related fraud.
Using proprietary wallet clustering techniques, behavioral heuristics, and transaction flow analysis, Nominis identified direct and indirect financial links between Epic Ballad and Legend of Constellations.
These connections included:
- Shared intermediary wallets used to move funds post-collection.
- Overlapping timing patterns in fund consolidation.
- Identical laundering behaviors following liquidity extraction.
- Reuse of wallet infrastructure across both schemes.
This analysis strongly indicates that the same operators, or a tightly coordinated group, were behind both projects, deploying different fraud models to maximize reach, longevity, and profit.
This finding was not publicly known at the time and was uncovered exclusively through NOMINIS’ multi-source intelligence approach, combining on-chain analytics with OSINT methodology.
The significance of this discovery extends beyond these two cases.
Firstly, it demonstrates that crypto fraud is rarely a single-project event. Actors frequently rebrand, relaunch under new narratives, target new regions or demographics, and alternate between Ponzi-style slow drains and fast rug pulls in order to pull off such scams.
Secondly, it highlights the limitations of surface-level project analysis. Without wallet clustering and cross-case intelligence, Epic Ballad and LOC appeared unrelated, allowing the same actors to continue operating undetected.
Finally, this case underscores the importance of proactive transaction monitoring and historical wallet intelligence for VASPs, gaming platforms, and regulators. Funds originating from such schemes often re-enter the broader crypto ecosystem, creating downstream compliance, reputational, and regulatory risks for legitimate businesses.
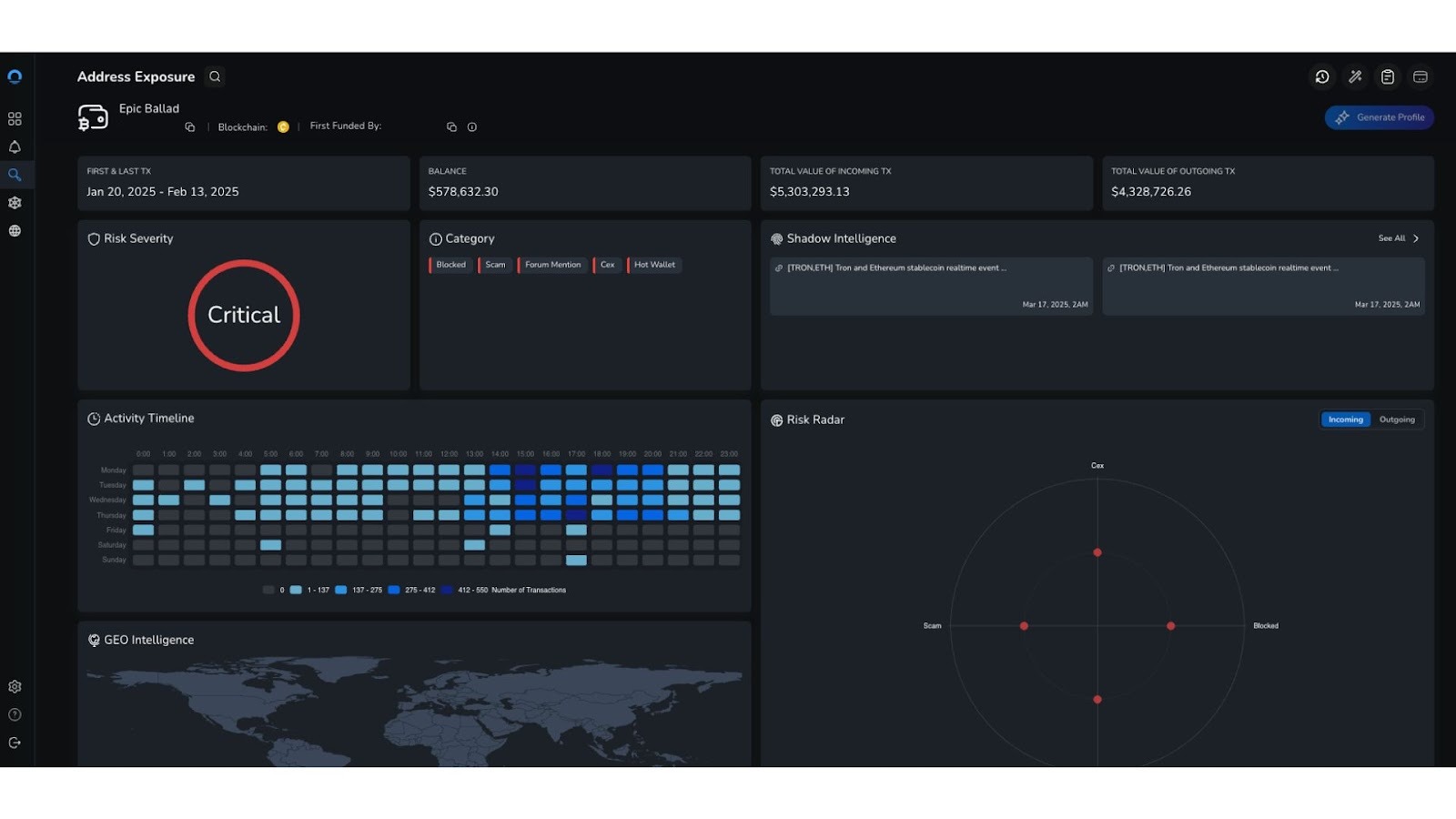
Example of an Epic Ballad wallet, as screened using the NOMINIS platform, to recognise the critical-level risk score. This wallet in particular has seen millions of dollars in cryptocurrency moving both in and out
NOMINIS SOCMINT- Driven Insights
Huione Guarantee Operated as Centralized Hub for Large-Scale Crypto Enabled-Fraud and Money-Laundering
As part of our ongoing SOCMINT monitoring, Nominis has been monitoring Huione Guarantee and Huione Group.
Huione Group is a Cambodia based financial and technology conglomerate that for years positioned itself publicly as a legitimate provider of payment services, digital finance tools, remittance solutions, and cryptocurrency related infrastructure. Through brands such as Huione Pay and Huione Crypto, the group sought to operate across both traditional financial services and emerging digital asset markets, offering mobile payments, exchange services, and supporting applications that appeared, on the surface, comparable to other regional fintech providers. This public facing legitimacy allowed Huione Group to build brand recognition, partnerships, and user trust within Southeast Asia and among Chinese speaking user bases operating internationally.
Within this broader corporate ecosystem, Huione Guarantee emerged as a distinct but connected entity. While often framed as a neutral escrow or “guarantee” service facilitating peer to peer transactions, Huione Guarantee operated primarily as a large-scale marketplace hosted on Telegram. Over time, this marketplace evolved into a central coordination and settlement layer for cyber enabled crime, particularly scams, fraud operations, and money laundering services. The platform functioned by connecting merchants, service providers, and buyers through thousands of Telegram channels, with Huione Guarantee acting as the trusted intermediary that held and released funds, almost exclusively using USDT stablecoins.
The connection between Huione Guarantee and Huione Group is not incidental or superficial. Multiple investigations and open source findings have shown shared branding, technical infrastructure, financial rails, and historical corporate ties between the marketplace and the parent group. Huione Guarantee relied heavily on Huione affiliated payment channels, wallet infrastructure, and reputation to present itself as a safe and reliable escrow service. When scrutiny intensified, Huione Guarantee attempted partial rebranding under names such as Haowang Guarantee, but continued to acknowledge ownership links and operational dependence on Huione Group resources. These changes appeared reactive rather than transformative, aimed at distancing the marketplace from growing allegations while maintaining continuity for its user base.
As part of the investigation, NOMINIS uncovered hundreds of Telegram groups operated by or directly affiliated with Huione Guarantee and the wider Huione eco-system. These groups function as merchant hubs, service marketplaces, and coordination channels for illicit activity, such as Tudou Guarantee (the primary successor to Huione Guarantee), Huihai Guarantee (an example of an alternative name used), as well as lesser-known groups such as Suncity Guarantee and Pacific Guarantee, to name a few.
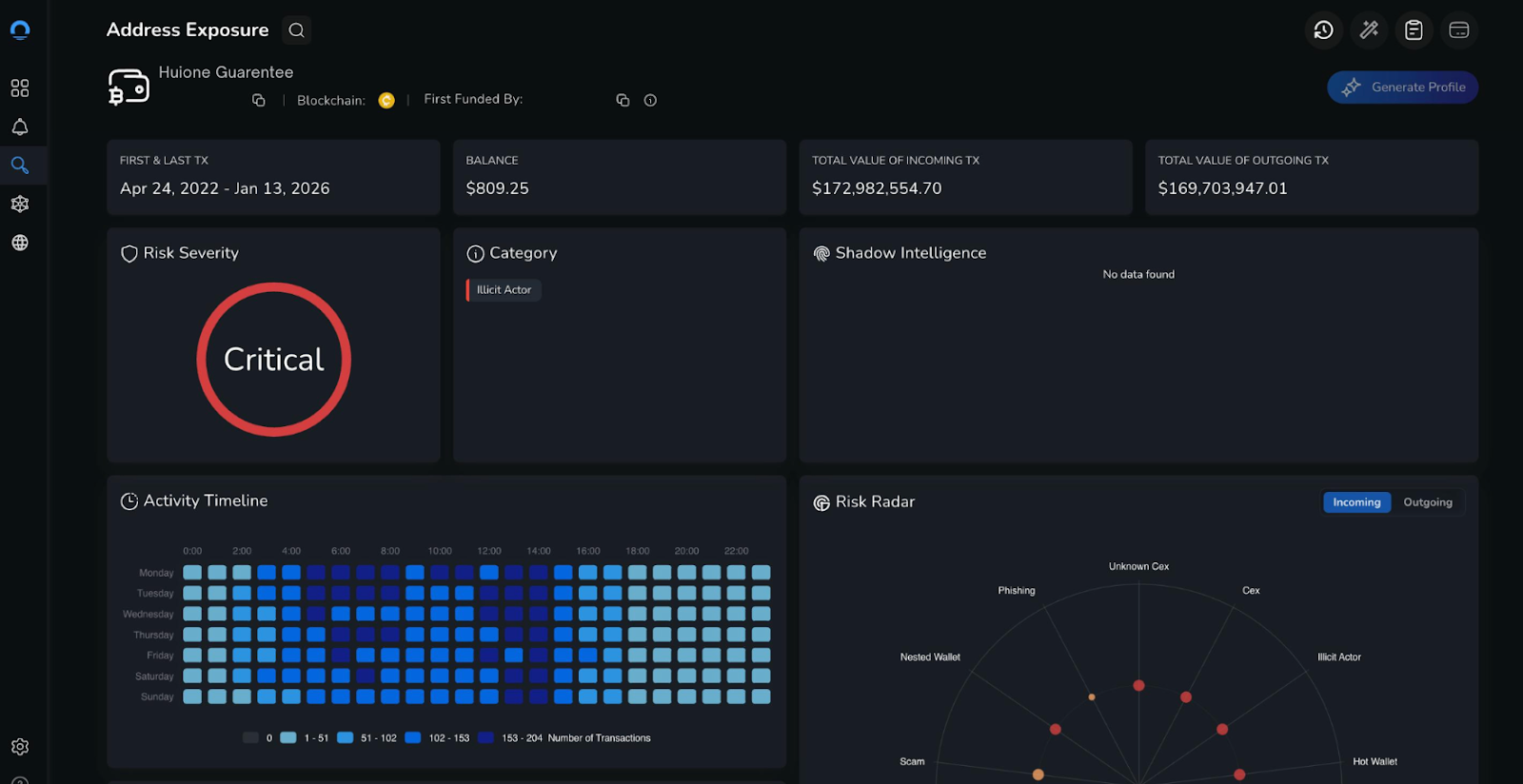
As well as Huione’s eco system, NOMINIS also uncovered wallets belonging to their greatest competitor, Xinbi. Xinbi is a Chinese Illicit marketplace, allegedly registered in the US. Also using Telegram, Xinbi facilitates a wide range of cybercrime, including money laundering and the sale of stolen data.
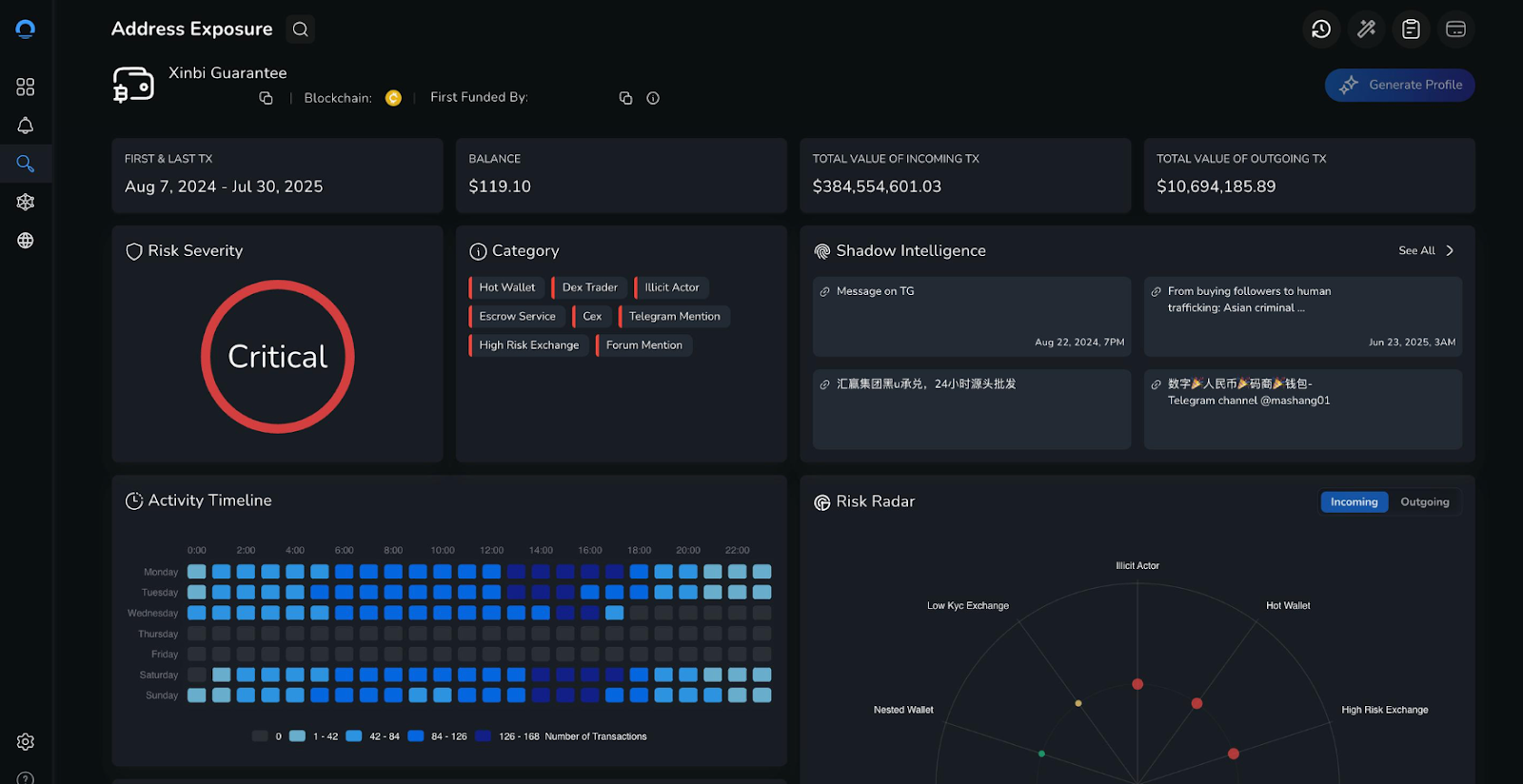
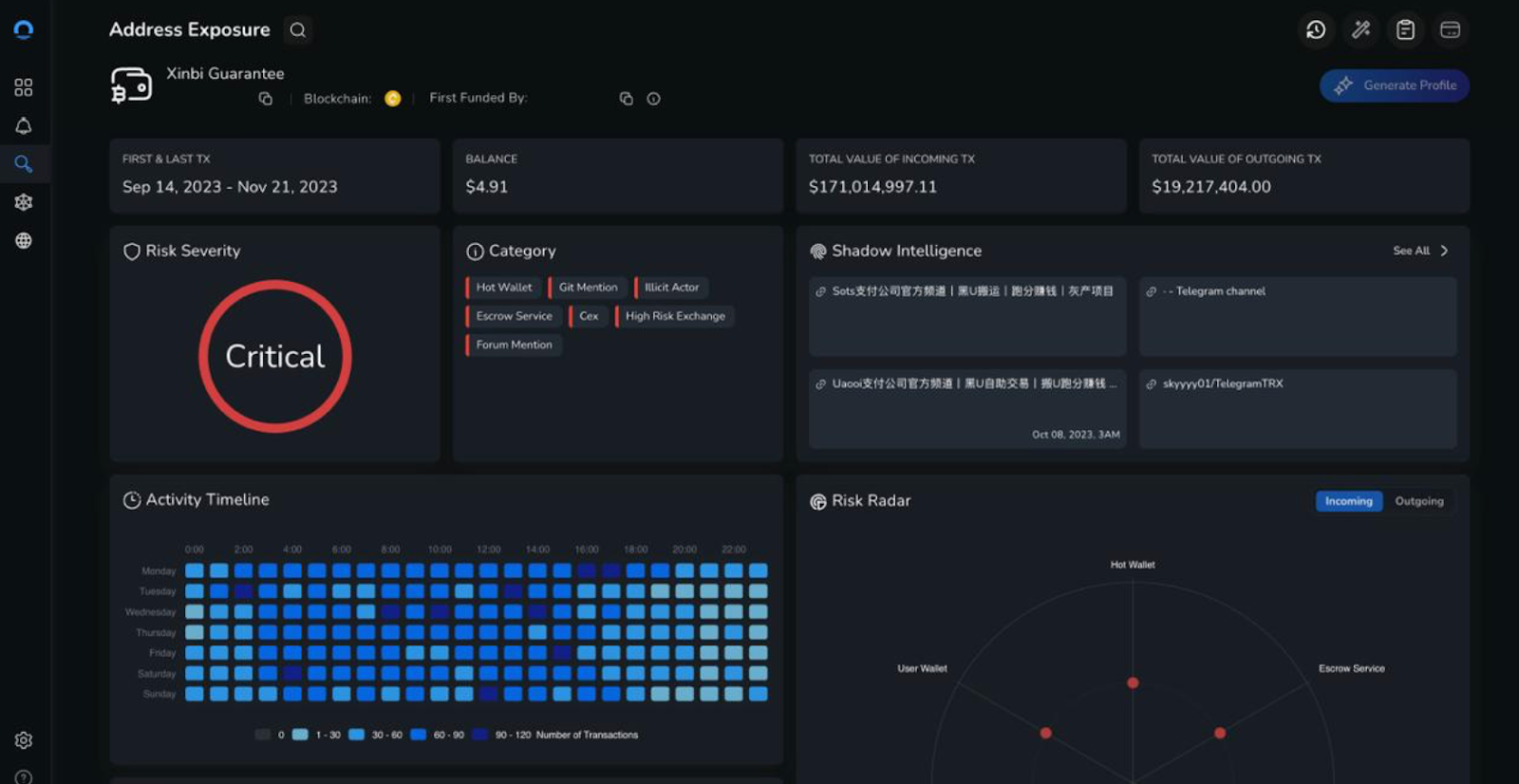
NOMINIS identified and continuously monitored these groups, clustering the cryptocurrency wallets associated with their operations and tracing fund flows across multiple blockchains. Each wallet cluster was reviewed and verified for its role in facilitating or receiving proceeds linked to scams, fraud, and laundering services. Once verified, these wallets were added to the Nominis risk database, enabling clients to identify exposure and prevent accidental interaction with Huione linked illicit activity, thereby reducing the risk of becoming indirectly complicit.
Operationally, Huione Guarantee became deeply embedded in global scam ecosystems. Vendors on the platform offered services that directly supported large scale fraud operations, including pig butchering scams, romance investment fraud, phishing infrastructure, mule account coordination, laundering services, and technical tooling for scam call centers. The marketplace’s design reduced friction for criminal collaboration by combining social coordination on Telegram with stablecoin settlement that avoided traditional banking oversight. The result was an ecosystem that could scale rapidly, operate across jurisdictions, and continuously onboard new participants with minimal identity verification or compliance controls.
Blockchain analysis conducted by multiple intelligence providers has shown that the volume of funds moving through wallets associated with Huione Guarantee reached unprecedented levels. Estimates place the total transaction value in the tens of billions of dollars, surpassing the lifetime volumes of many historically significant darknet markets. These figures reflect only the flows that could be confidently attributed through on chain analysis and known wallet clusters, indicating that the true scale of activity may be higher. The dominance of USDT in these flows highlights the role of stablecoins as a preferred medium for illicit settlement due to their liquidity, price stability, and ease of transfer across chains and platforms.
As scrutiny increased, Huione Group and its affiliated entities began to experience escalating enforcement and platform level consequences. Cambodian authorities moved to revoke Huione Pay’s banking license, citing compliance failures and concerns related to money laundering and scam facilitation. International pressure intensified as regulators and financial intelligence bodies flagged Huione Group as a high risk actor within the global financial system. In parallel, major technology platforms including Apple and Google removed applications associated with Huione Group from their app stores, significantly limiting the group’s ability to distribute and maintain its consumer facing financial products.
A decisive blow to Huione Guarantee came when Telegram undertook a large-scale enforcement action targeting criminal marketplaces operating on its platform. Thousands of channels, usernames, and merchant groups associated with Huione Guarantee and related marketplaces were removed in a coordinated purge. Following this action, Huione Guarantee announced that it was ceasing operations, acknowledging that the Telegram takedown had dismantled the infrastructure on which the marketplace depended. This event marked one of the largest disruptions of a crypto-enabled illicit marketplace to date.
Despite this shutdown, the underlying networks did not disappear entirely. Intelligence monitoring has shown that merchants, facilitators, and service providers previously active on Huione Guarantee began migrating to successor platforms and newly established guarantee style marketplaces. This pattern reflects a broader trend in cybercrime ecosystems, where enforcement actions fragment infrastructure but rarely eliminate demand or expertise. The Huione case demonstrates how quickly these networks can adapt, rebrand, and reconstitute themselves when pressure is applied.
From a SOCMINT and blockchain intelligence perspective, Huione Guarantee and Huione Group represent a critical case study in how ostensibly legitimate fintech ecosystems can coexist with, enable, or directly support large scale illicit activity. The blending of corporate branding, consumer applications, messaging platforms, and stablecoin based settlement created a resilient environment that obscured risk until transaction volumes reached extraordinary levels. Continued monitoring of successor platforms, affiliated wallets, and social coordination channels remains essential to understanding how these networks evolve and to preventing their reintegration into compliant financial systems.
NOMINIS Dark Web Investigations
Throughout the past year, the NOMINIS Intelligence Unit has conducted extensive monitoring and analysis of cryptocurrency wallets and services operating within dark web ecosystems. Our findings reveal several dominant criminal economic trends, concerning how established cryptocurrencies continue to power the majority of underground economies, while privacy-oriented assets are gradually expanding their footprint. The data underscores the persistent role of digital assets in enabling transnational crime, ranging from drug trafficking and financial fraud to the sale of weapons and hacking services.
Bitcoin and Tron Remain Dominant on the Dark Web, while Monero’s Presence Grows
Across dark web ecosystems in 2025, Bitcoin (BTC) and Tron (TRX) maintained their position as the most widely used blockchains for illicit transactions, serving as the backbone of criminal marketplaces and peer-to-peer exchanges. Together, they account for the vast majority of all cryptocurrency blockchains identified by the NOMINIS Intelligence Unit throughout the year.
Bitcoin continues to serve as the primary currency of the dark web, favored for its liquidity, ease of access, and deep integration into darknet infrastructure. Tron, meanwhile, may have increased in popularity for lower-tier vendors, and small illicit operations, due to its low transaction fees and speed, perhaps making it a preferred alternative for frequent microtransactions.
In parallel, Monero (XMR) has seen steady adoption growth. Despite its strong privacy features, most marketplaces that accept Monero also continue to support Bitcoin as a secondary payment option, signalling that while privacy coins are gaining traction, NTC remains the central medium of exchange in the dark web economy.
In total, ~64% of the wallets used to accept payment on the dark web this year were BTC, followed by ETH (~13%), LTC (~13%), DOGE (~7%) and TRON (~5%). This distribution illustrates that while alternatives and privacy-centric assets are expanding, established blockchains continue to dominate illicit financial activity.
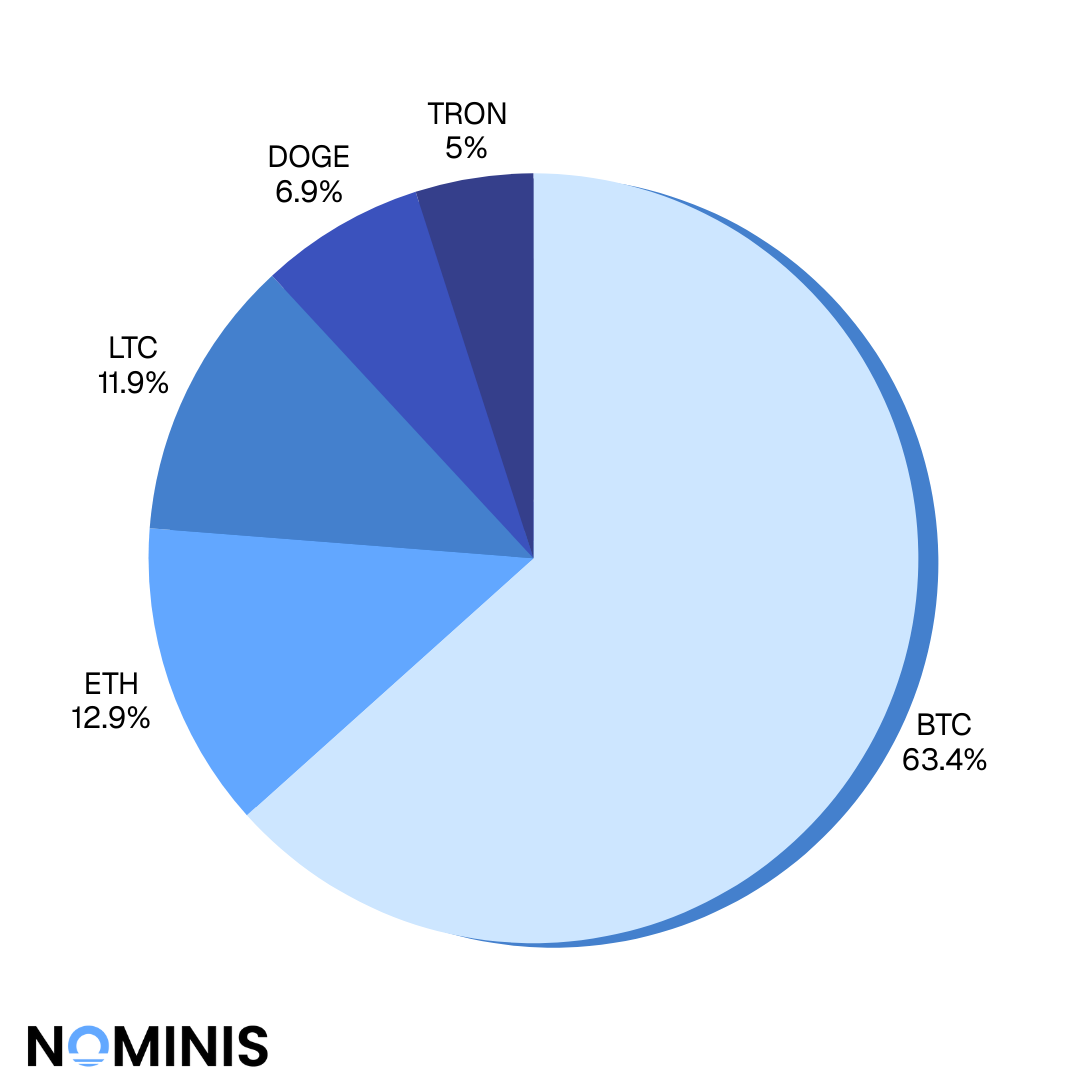
The Drug Trafficking Market remains the most prevalent industry on the Dark Web, followed by Stolen Credit Cards
The largest portion of dark web activity this year was linked to drug trafficking, representing approximately 36% of total dark web findings. These networks are primarily based in Latin America, exporting cocaine, heroin, and methamphetamine internationally to mostly North America and Europe, with Bitcoin serving as the dominant settlement currency.
Meanwhile, stolen credit cards for sale made up 14% of our total analysis. Weapons trafficking contributed 13%, and paid hacking services made up approximately 12%. Stolen or hacked Paypal accounts and transfers for sale amounted to approximately 11% of analysed vendors.
These figures underscore that despite increased law enforcement focus and regulatory measures, cryptocurrency continues to fuel established underground economies, from cybercrime and fraud, to the global narcotics trade.
A smaller but deeply concerning share of this year’s findings involved human organ trafficking, child exploitation material, and extreme violence content, inclduing rape and murder images and videos, comprising approximately 3% of total discoveries.
Such cases highlight the most severe and disturbing use cases of blockchain-enabled anonymity. They reinforce the importance of continued monitoring, intelligence sharing, and cross-platform compliance solutions to ensure that exchanges, payment processors, and investigators can identify and isolate high-risk activity before it reaches regulated environments.
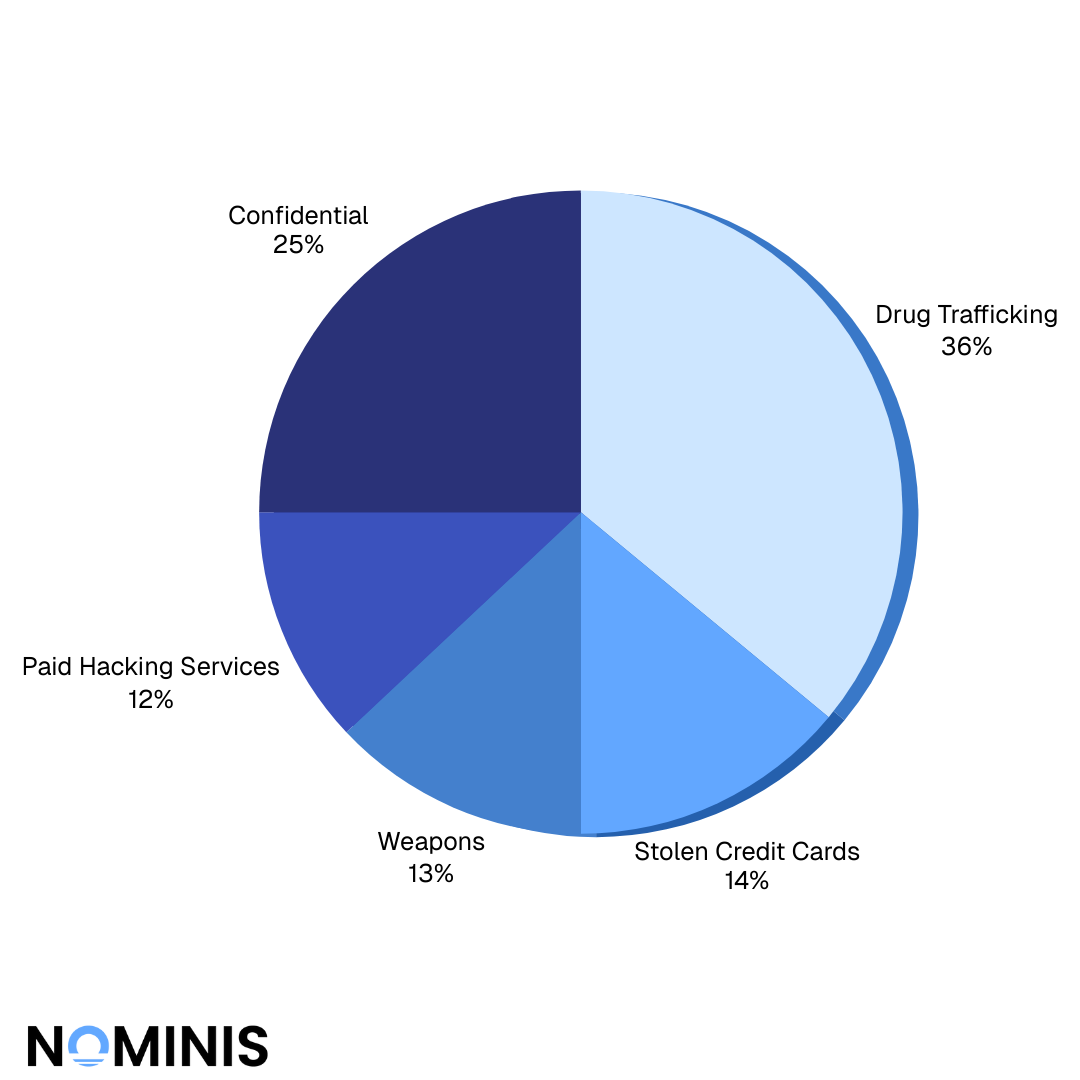
2025 developments of the NOMINIS platform
The last year marked a significant evolution of NOMINIS, shifting the focus exclusively from risk-screening over to creating a comprehensive platform that combines advanced screening with high-level forensic investigation capabilities. These developments have not only enhanced the functionality available to our clients but have also contributed meaningful advancements to the broader crypto compliance industry.
A standout innovation in 2025 was AsKYT, a Bitcoin-native analytics project centered around a simple challenge: making complex on-chain investigations fast, accurate, and genuinely usable, without sacrificing analytical rigor. Built as a Custom GPT, AsKYT allows users to ask clear, natural-language questions about wallets, transactions, and activity, and receive structured, explainable insights grounded in on-chain data. Users can move seamlessly from high-level exploration to focused investigative conclusions, benefiting from an interface that is both intuitive and powerful. By reducing friction while maintaining trust in the underlying data, AsKYT sets a new standard for blockchain intelligence, making sophisticated analytics accessible without compromising depth or reliability. AsKYT is available via ChatGPT's GPT Store and can also be accessed directly through NOMINIS.
In parallel, we launched CryptoSanctions.net, a one-stop, structured resource for assessing sanctioned wallets and entities. By consolidating a comprehensive list of sanctions into a searchable, accessible interface, CryptoSanctions.net empowers compliance professionals, researchers, and analysts to rapidly identify high-risk counterparties. Beyond detection, this initiative represents NOMINIS’ commitment to transparency in the crypto ecosystem, providing the industry with actionable intelligence that strengthens regulatory adherence and risk management.
Other enhancements within NOMINIS in 2025 continued to refine investigative workflows. Our new case management tool enables users to document, track, and resolve investigations entirely within the platform, improving auditability, collaboration, and consistency across teams. Risk Radar, an interactive visualization of wallet exposure, transforms raw blockchain activity into intuitive radial maps, instantly showing risk concentration and interaction with counterparties such as CEXs, DEXs, liquidity pools, and proxy wallets. Complementing this, Shadow Intelligence integrates off-chain context, from OSINT, security reports, and deep web sources, into the , giving investigators the situational awareness needed to connect on-chain patterns with real-world events.
Together, these developments demonstrate NOMINIS’ continued focus on not just identifying risk, but equipping the industry with tools, intelligence, and workflows that set new standards in blockchain investigations and crypto compliance. By integrating AI-driven search, comprehensive sanctions data, and combined on-chain/off-chain visibility, NOMINIS is helping shape the next generation of investigative and compliance solutions.
Looking ahead to 2026, we prepare to expand NOMINIS into a robust forensic suite used not only by compliance teams and intelligence analysts, but also law enforcement and private investigators. Our upcoming forensic tools will bring advanced tracing, attribution and pattern-linking capabilities to the platform, which enables users to conduct full source-of-fund investigations entirely within. These additions will bridge the gap between commercial compliance tools and professional digital-forensics software, making high quality investigations accessible to a broader community of users.
Conclusion: Lessons from 2025
The evidence presented throughout this report demonstrates that 2025 was not simply another year of crypto-related crime; it was a year that revealed the maturation, sophistication, and strategic integration of digital assets into the operational frameworks of hostile states, terrorist organizations, and transnational criminal networks. The findings documented across hundreds of investigations, billions of dollars in traced transactions, and thousands of flagged wallets collectively illustrate a fundamental reality: cryptocurrency has evolved from a peripheral tool of illicit finance into a core infrastructure enabling some of the most consequential threats to global security and financial integrity.
What makes 2025 particularly instructive is not the volume of incidents alone, but the patterns of adaptation, exploitation, and resilience that emerged across every category of threat actor we monitored. From North Korea's Lazarus Group executing the largest single exchange breach in history, to Hamas leveraging humanitarian narratives to fund military operations, to the IRGC moving hundreds of millions through Western-registered exchanges, to billion-dollar criminal marketplaces operating openly on Telegram, each case study reinforces a consistent conclusion: adversaries are not simply using cryptocurrency; they are systematically exploiting the structural gaps, jurisdictional fragmentation, and compliance assumptions that define the current global regulatory landscape.
The Strategic Exploitation of Trust and Fragmentation
Perhaps the most critical insight from 2025 is the deliberate targeting of jurisdictions and platforms perceived as "low-risk." Our analysis revealed that approximately 94% of terror-linked transactions flowed through exchanges operating in Grey listed countries, or countries that do not appear on a list, environments characterized by political stability, economic development, and formal AML/CTF frameworks. This is not accidental. It reflects a sophisticated understanding by hostile actors that compliance frameworks are often calibrated to jurisdictional reputation rather than behavioral risk, and that enforcement resources are disproportionately concentrated in regions already designated as high-risk.
The result is a strategic vulnerability: the very characteristics that make a jurisdiction appear safe, regulatory maturity, financial stability, institutional credibility, become operational camouflage for illicit activity. In Australia, we documented terror-linked funds moving through licensed exchanges and banks under the guise of humanitarian fundraising. In the United Kingdom, IRGC-linked wallets routed millions through London-registered crypto platforms. Across the UAE, Singapore, Canada, and the United States, terrorist facilitators and sanctions evaders accessed global liquidity with minimal friction, precisely because these jurisdictions were assumed to pose lower exposure.
This dynamic exposes a fundamental flaw in traditional risk modeling. When adversaries intentionally distribute their financial activity across trusted environments, geography ceases to be a reliable indicator of actual threat. Compliance that relies on static jurisdiction-based assessments, rather than continuous behavioral and network analysis, creates blind spots that can be, and demonstrably have been, systematically exploited at scale.
Structural Vulnerabilities in Exchange Infrastructure
Beyond jurisdictional arbitrage, our investigations into exchange architectures revealed that design choices themselves have become weaponized by threat actors. Instant exchanges enable post-exploit funds to move faster than detection systems can propagate alerts, collapsing the intervention window to minutes rather than hours or days. Nested exchange structures allow proxy services to aggregate high-risk activity beneath compliant façades, obscuring ultimate beneficial ownership and source-of-funds attribution. Offshore and no-KYC platforms provide anonymity at industrial scale through weak identity controls, opaque ownership, and regulatory fragmentation across jurisdictions where enforcement is inconsistent or politically constrained.
These are not isolated edge cases. They represent core components of the global crypto ecosystem's operational architecture. The FixedFloat and eXch.cx cases demonstrated how quickly stolen funds can be converted and dispersed through instant swaps. The Binance lawsuit analysis revealed how wallets with direct exposure to Hamas, Hezbollah, and the IRGC maintained sustained access to one of the world's largest exchanges. The Huione Guarantee investigation documented a criminal marketplace ecosystem processing tens of billions of dollars through Telegram-coordinated escrow and USDT settlement, operating openly for years before coordinated enforcement action.
What unites these cases is a recurring pattern: illicit actors do not need to build their own infrastructure; they exploit existing, ostensibly legitimate platforms by leveraging features designed for speed, liquidity, and user convenience. Transaction velocity, custodial pooling, API flexibility, high withdrawal limits, and jurisdictional opacity, each individually defensible as a competitive or operational feature, collectively create an environment where large-scale laundering, sanctions evasion, and terror financing can persist with limited detection or disruption.
The Integration of Cryptocurrency into Hostile State and Terror Operations
The findings from our Middle East, North Korea, and Russia investigations underscore that cryptocurrency is no longer experimental for these actors, it is operational, embedded, and strategic.
For Hamas, cryptocurrency enables financial resilience in an environment of extreme banking restrictions and international isolation. The Buy Cash network, despite repeated designations and seizures, continued to facilitate flows between fundraising campaigns, OTC brokers, and military-wing operations, demonstrating both technical adaptability and organizational continuity. Our analysis of humanitarian-themed fundraising revealed how emotional narratives, community trust, and fragmented oversight allowed terror-linked actors to solicit funds from unwitting donors across multiple countries, routing proceeds through intermediary wallets into confirmed terrorist infrastructure.
For Hezbollah and the IRGC, cryptocurrency functions as a sanctions-bypass mechanism at state-aligned scale. The cross-regional pipeline linking Hezbollah financial networks to Latin American drug cartels, documented through wallet clustering and transaction-flow analysis, illustrates how terrorist organizations and profit-driven criminal syndicates now collaborate operationally, using digital assets as the connective infrastructure. IRGC oil-revenue laundering, conducted through wallets processing hundreds of millions of dollars and converting proceeds into high-liquidity stablecoins, demonstrates how digitized commodity revenues can sustain proxy warfare, procurement networks, and regional destabilization efforts without reliance on formal banking channels.
For North Korea, cryptocurrency is not merely a revenue stream, it is a state survival mechanism directly funding nuclear weapons development, ballistic missile programs, and the regime's internal elite economy. The evolution from large-scale exchange hacks (Bybit, $1.4 billion) to targeted, relationship-driven social engineering attacks against DeFi founders and high-net-worth individuals reflects real-time adaptation under sanctions pressure. The infiltration of Western crypto entities via falsified developer credentials, documented in our OSINT research, reveals a longer-term strategy: embedding operatives within legitimate organizations to siphon intelligence, insert malware, and gain insider access to systems and funds.
In Russia, cryptocurrency serves as a financial resilience layer in the face of comprehensive sanctions and restricted international banking access. The MIR Pay investigation demonstrated how domestic payment rails can function as crypto on-ramps, enabling sanctioned users to convert rubles into digital assets with minimal friction. The Aeza Group case revealed how bulletproof hosting infrastructure, ransomware networks, and darknet marketplaces interlock with crypto payment flows, creating a self-reinforcing ecosystem where cybercrime, sanctions evasion, and state-aligned activity operate in parallel, often indistinguishably.
Across all of these actors, cryptocurrency provides speed, borderless transferability, reduced reliance on regulated intermediaries, and operational continuity when traditional channels are frozen or blocked. These are not opportunistic crimes, they are deliberate, systematic, and strategically essential adaptations by adversaries facing coordinated international pressure.
The Necessity of Intelligence-Driven, Behavioral Detection
The challenges documented in this report cannot be addressed through reactive enforcement alone. Static sanctions lists, jurisdiction-based risk tiers, and post-incident forensics are necessary but insufficient. What is required is a fundamental shift toward continuous, intelligence-driven transaction monitoring that prioritizes behavioral analysis, network proximity, and adversarial pattern recognition over surface-level compliance checks.
NOMINIS' approach throughout 2025 exemplifies this shift. By clustering over 1 billion wallets across multiple blockchains, we enabled granular attribution and network mapping at unprecedented scale. By integrating on-chain analytics with OSINT, SOCMINT, and deep/dark web intelligence, we surfaced connections and exposure chains invisible to single-source analysis. By collaborating directly with law enforcement, regulatory bodies, and industry partners, we translated raw data into actionable intelligence, flagging high-risk wallets, identifying emerging typologies, and providing early warnings ahead of formal sanctions or public disclosures.
Our Terror Financing Database, built through close collaboration with investigative agencies and now encompassing thousands of verified wallets, demonstrates how proactive intelligence sharing can disrupt illicit networks in real time. Our geolocation analysis, revealing how Iranian users masquerade as U.S. or German traders via VPN/proxy networks, underscores the necessity of multi-layered verification beyond static IP checks. Our exchange infrastructure assessments provide compliance teams with structural risk indicators, licensing status, custodial architecture, API flexibility, withdrawal limits, that predict vulnerability to nesting, laundering, and sanctions evasion before incidents occur.
Education remains equally critical. Through partnerships with ACAMS and targeted webinars, we have equipped compliance officers, investigators, and financial institutions with the contextual knowledge needed to distinguish legitimate activity from abuse, recognize intermediary wallets functioning as financial bridges, and understand that terror financing extends far beyond weapons procurement into training, travel, propaganda, recruitment, and operational infrastructure. Technology without education produces noise; education without technology produces blind spots. Both are essential.
The Limitations and Persistence of Adversarial Networks
It is important to acknowledge that enforcement actions, while necessary and impactful, rarely eliminate the underlying networks or demand that sustain illicit activity. The Telegram takedown of Huione Guarantee, which dismantled thousands of channels and forced the marketplace to announce its closure, represented one of the largest disruptions of a crypto-enabled criminal ecosystem to date. Yet our monitoring confirmed that merchants, facilitators, and service providers immediately began migrating to successor or alternative groups, Tudou Guarantee, Suncity Guarantee, Pacific Guarantee, demonstrating that enforcement fragments infrastructure but does not erase expertise, relationships, or economic incentives.
Similarly, Buy Cash's repeated rebranding efforts, Binance's continued processing of terror-linked wallets even after public designations, and North Korea's shift from exchange hacks to social engineering attacks all illustrate a consistent pattern: adversaries adapt faster than systems can harden. They rebrand, migrate to new platforms, target new jurisdictions, exploit emerging technologies, and continuously probe for gaps in detection and enforcement.
This does not mean that enforcement is futile; far from it. Each disruption increases operational costs, reduces trust within criminal networks, forces migrations that create attribution opportunities, and demonstrates to illicit actors that their activity is visible, traceable, and subject to consequences. However, it does mean that one-time interventions, isolated sanctions designations, or platform-by-platform enforcement will always lag behind adversarial innovation.
What is needed is persistent, adaptive, intelligence-driven monitoring that treats illicit finance as an ongoing operational challenge rather than a series of discrete incidents. This requires sustained investment in blockchain analytics, cross-jurisdictional coordination, intelligence sharing between public and private sectors, and regulatory frameworks that incentivize proactive detection over reactive compliance.
Toward a Resilient and Accountable Ecosystem
The cryptocurrency ecosystem stands at a critical juncture. The technology's transformative potential, borderless value transfer, financial inclusion, programmable assets, decentralized governance, remains compelling and worthy of continued development and adoption. However, that potential is fundamentally undermined when the same infrastructure enables hostile states to fund nuclear programs, terrorist organizations to sustain military operations, ransomware groups to extort hospitals and critical infrastructure, and criminal marketplaces to facilitate fraud at billion-dollar scale.
The question is not whether cryptocurrency will be used by illicit actors, it demonstrably will be, as this report exhaustively documents. The question is whether the ecosystem can evolve rapidly enough to detect, disrupt, and prevent that misuse before it causes irreversible harm.
This evolution requires several interrelated commitments:
Unified KYC and KYT Standards Across Jurisdictions: Regulatory fragmentation creates exploitable gaps. Harmonized identity verification, transaction monitoring, and suspicious activity reporting standards, enforced consistently across jurisdictions, would significantly reduce the viability of jurisdictional arbitrage as an evasion strategy.
Licensing as a Baseline Control: Our exchange analysis demonstrated that licensing imposes auditability, regulator engagement, and data-sharing obligations that materially constrain proxy abuse and nesting. Expanding licensing requirements globally, with reciprocal recognition and enforcement mechanisms, would reduce the operational space available to offshore and no-KYC platforms.
Behavioral and Network-Based Risk Detection: Moving beyond static sanctions lists and IP-based geolocation toward continuous behavioral monitoring, wallet clustering, transaction-pattern analysis, and network-proximity scoring. This requires investment in advanced analytics, machine learning, and intelligence integration, but it is the only approach capable of identifying adaptive adversaries in real time.
Intelligence Sharing Between Public and Private Sectors: Law enforcement possesses investigative authorities and classified intelligence; private-sector analytics firms possess scale, speed, and technical infrastructure. Structured partnerships, already demonstrated through NOMINIS' collaboration with agencies, exchanges, and regulatory bodies, enable both sectors to operate more effectively than either could in isolation.
Transparency and Accountability in Platform Design: Exchanges, DeFi protocols, and service providers must recognize that their design choices have security externalities. Transaction speed, custodial opacity, API flexibility, and withdrawal limits are not neutral features, they create attack surfaces. Platforms willing to prioritize security, transparency, and accountability over unconstrained convenience will differentiate themselves and contribute to ecosystem resilience.
Education and Operational Vigilance: Compliance is not a checklist, it is a continuous practice informed by evolving intelligence. Training compliance teams to recognize terror financing typologies, understand intermediary wallet functions, and interpret behavioral anomalies is as critical as deploying technology. Vigilance requires both tools and expertise.
NOMINIS' Role and Commitment Moving Forward
Throughout 2025, NOMINIS demonstrated that independent intelligence providers can play a decisive role in shaping the crypto ecosystem's response to illicit finance. By identifying North Korean social engineering tactics months before OFAC sanctions, exposing IRGC laundering through London-based exchanges before media coverage, mapping Hamas fundraising infrastructure ahead of law enforcement actions, and flagging Huione Guarantee's criminal marketplace ecosystem at unprecedented scale, we have consistently provided early warnings and actionable intelligence that empowered stakeholders to act proactively rather than reactively.
Our contributions extend beyond individual investigations. The Terror Financing Database, AsKYT AI-driven analytics, CryptoSanctions.net resource, GeoIntelligence platform, and continuous dark web monitoring collectively represent an integrated approach to threat detection that combines technology, intelligence, and operational expertise. Our partnerships with ACAMS, law enforcement agencies, and exchanges demonstrate that collaboration amplifies impact, translating intelligence into real-world prevention.
Looking toward 2026, we are committed to expanding the NOMINIS platform into a comprehensive forensic suite used by compliance teams, intelligence analysts, law enforcement, and private investigators. Advanced tracing, attribution, and pattern-linking capabilities will enable users to conduct full source-of-funds investigations entirely within the platform, bridging the gap between commercial compliance tools and professional digital forensics software. This evolution reflects our broader mission: making sophisticated blockchain intelligence accessible, actionable, and operationally decisive for all stakeholders working to prevent the misuse of digital assets.
Final Reflection
The findings in this report are sobering. They document billions of dollars stolen, laundered, and weaponized. They reveal hostile states funding nuclear programs through crypto theft, terrorist organizations sustaining military operations through humanitarian-themed fundraising, and criminal marketplaces processing transaction volumes exceeding historical darknet markets. They expose structural vulnerabilities in exchange architectures, jurisdictional blind spots in compliance frameworks, and the systematic exploitation of trust by adversaries who understand the ecosystem's weaknesses better than many of its defenders.
Yet this report also demonstrates what is possible when intelligence, technology, and collaboration converge. Every wallet cluster mapped, every fraudulent fundraising campaign exposed, every exchange vulnerability identified, and every early warning delivered represents progress toward a more resilient, accountable, and secure ecosystem. The adversaries documented in these pages are sophisticated, adaptive, and well-resourced, but they are not invisible, and they are not invincible.
The cryptocurrency industry, regulatory bodies, law enforcement agencies, and intelligence providers now possess the tools, data, and understanding needed to confront these threats with precision and resolve. What is required is the collective will to prioritize security alongside innovation, accountability alongside growth, and long-term resilience alongside short-term convenience.
The threats documented in 2025 will persist into 2026 and beyond. Adversaries will continue to adapt, exploit new technologies, migrate to emerging platforms, and probe for weaknesses. However, by maintaining continuous vigilance, investing in intelligence-driven detection, fostering cross-sector collaboration, and committing to transparency and education, the ecosystem can evolve to meet these challenges with the seriousness and sophistication they demand.
NOMINIS remains committed to this mission. We will continue to investigate, expose, and disrupt illicit finance across digital assets. We will continue to provide the industry with actionable intelligence, advanced analytics, and the strategic insights needed to stay ahead of adversaries. And we will continue to demonstrate that while the threats are formidable, they are not insurmountable, provided we approach them with rigor, collaboration, and an unwavering commitment to protecting the integrity of the global financial system.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.





