1st Place Winner
Mastercard Fintech Forum 2025
Blockchain Wallet Screening & Transaction Monitoring for AML/CFT
Complete on-chain, off-chain, behavioral and geo-location analysis.
Built for data-driven Crypto Compliance teams.
FATF, MiCA, FinCEN, VARA, ADGM, AMLD5 & Travel Rule ready.
Trusted bY LeadING VASPs, Banks and payment processors












A global leader in sanctions & blacklist data
Nominis delivers unmatched depth and global coverage by integrating court cases, law-enforcement actions, and stablecoin issuer blacklists: OFAC , DOJ, NBCTF, OFSI, USDC (Circle), USDT, PYUSD, USDP, XSGD, USDM, and PAXG.
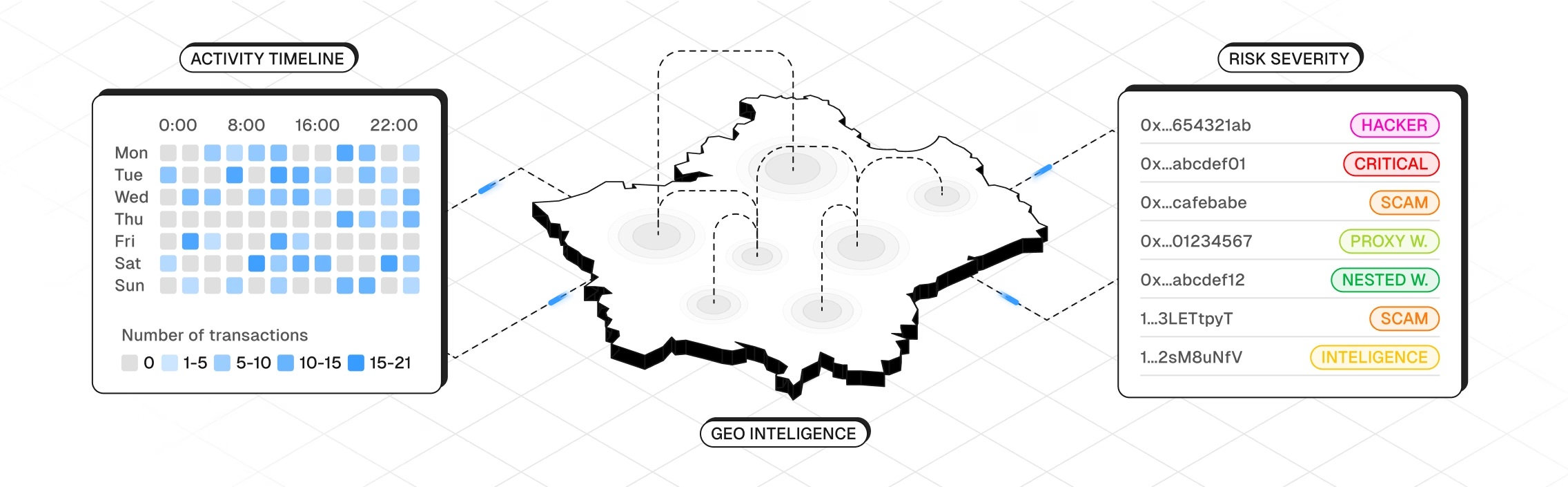
See the Full Transaction
Nominis connects on-chain, off-chain, and behavioral data — so you get the full context behind every transaction. On autopilot.
Monitoring That Never Sleeps
Always-on protection with real-time analysis. Alerts fire the moment suspicious activity appears — even if the wallet looked clean yesterday.
Pay as You Grow
Transparent pricing designed for flexibility. No lock-ins or hidden fees — just a model that scales with your business, the way SaaS should work in 2025.
Meet the Nominis Intelligence Unit
Our team investigates the Dark Web, major hacks, and crypto crime networks - and publishes real-world threat reports for the industry.
What Our Customers Say
Real stories from compliance teams who've transformed their operations with NOMINIS.
"Nominis gives us real-time clarity into wallet activity, even across 20+ transaction hops. Their proactive, off-chain intelligence helps us stay ahead of risk and remain compliant as we scale."
"Nominis is one of Depa's key partners to ensure a robust compliance framework is maintained in the blockchain. We value particularly how they deal with indirect risk exposures in centralized wallets for unidentified CASPs."
I’ve had the pleasure of working with Nominis across multiple client engagements, and they consistently deliver one of the most effective and reliable risk screening platforms available. Their team deeply understands the needs of compliance professionals and brings real value to every project.
Why Choose NOMINIS
NOMINIS provides the complete intelligence you need to protect your platform, ensure compliance, and stay ahead of evolving threats.
Full Transaction Stories
On-chain, off-chain (deep/dark/open web) and behavioral signals combined.
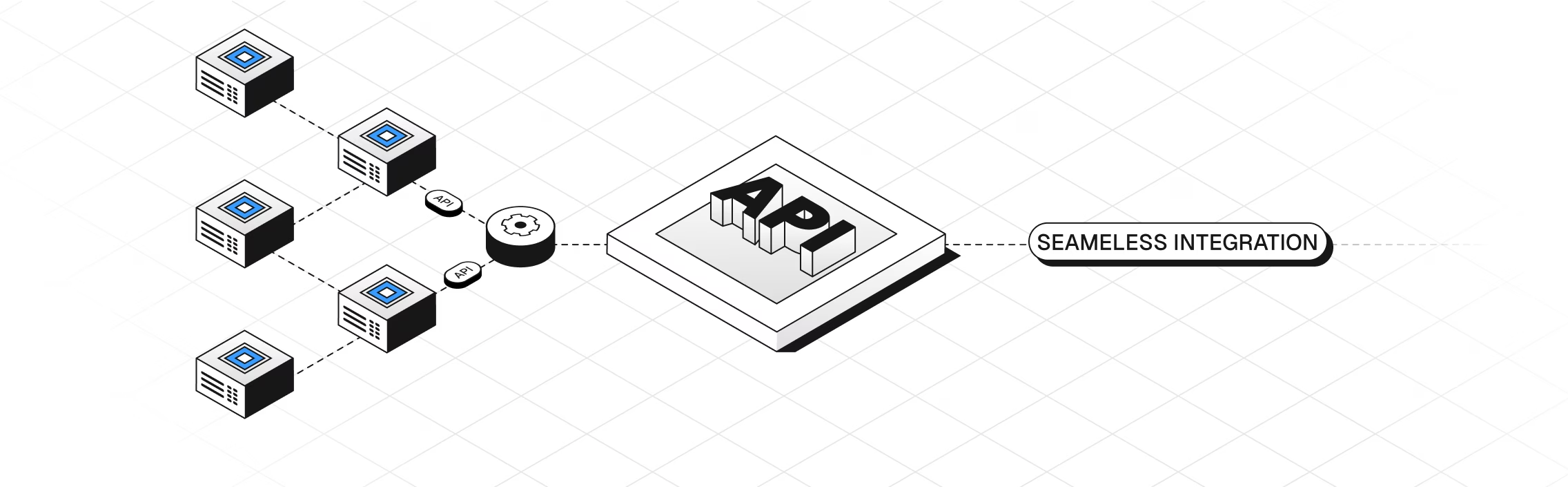
Industry-leading API
Receive the complete money-trail and transaction data via a single endpoint.
Continuous Monitoring
Real-time alerts whenever a previously scanned transaction or wallet changes.
Critical Gap
The Problem with KYT Today
Traditional tools focus mostly on source of funds and on-chain intelligence, missing the actual illicit funding red flags context found off-chain in dark net, open web, and deep web.

Comprehensive Intelligence
NOMINIS provides comprehensive intelligence across on-chain, dark web, open web, and deep web sources that serious compliance operations require.
Ready to experience the NOMINIS advantage?
Schedule a personal demo to see how our platform illuminates what legacy tools miss and protects your business with automated intelligence.





%20.jpg)



