91% of illicit crypto transactions were sent to exchanges in low-risk countries, according to NOMINIS Study
Executive Summary
This report examines a critical vulnerability in the global counter-terrorism financing architecture: the systematic exploitation of Virtual Asset Service Providers (VASPs) operating in jurisdictions perceived as low-risk by designated terrorist organizations and hostile state actors. Drawing on empirical data from a 24-hour observational study conducted by NOMINIS, this analysis reveals that approximately 91.5% of terror-linked cryptocurrency transactions target exchanges in low-risk and increased-risk jurisdictions, deliberately avoiding high-risk environments subject to intensive scrutiny. Statistically, this means illicit actors are 12 times more likely to use an exchange based in a ‘safe’ country, than an exchange based in a jurisdiction deemed as high risk.
This finding challenges foundational assumptions in anti-money laundering frameworks and demonstrates an urgent imperative: low-risk jurisdictions must implement robust Know Your Transaction (KYT) systems to prevent their financial infrastructure from becoming the preferred conduit for terrorist financing operations.
Introduction
The global fight against terrorist financing has traditionally focused enforcement resources on jurisdictions deemed high-risk by international bodies such as the Financial Action Task Force (FATF), currently listed as Iran, Myanmar, and North Korea. However, emerging evidence suggests that this geographic prioritization has created an inverse vulnerability: terrorist organizations and hostile state networks are increasingly routing financial operations through jurisdictions widely regarded as safe, stable, and compliant.
This counterintuitive pattern represents a fundamental miscalculation in how risk is assessed and threats are prioritised across the international financial system. When regulatory frameworks rely heavily on static jurisdictional classifications rather than dynamic behavioral analysis, they create predictable blind spots that sophisticated adversaries exploit systematically.
The cryptocurrency ecosystem amplifies this vulnerability. Digital assets enable rapid, cross-border value transfer with minimal friction, allowing hostile actors to leverage the reputational credibility of established financial centers while bypassing traditional banking oversight mechanisms. Virtual Asset Service Providers in politically stable, economically developed countries become unwitting conduits for illicit finance, precisely because their jurisdictional location signals legitimacy to both counterparties and compliance systems.
This report demonstrates why Know Your Transaction monitoring represents an essential defensive capability for low-risk jurisdictions seeking to avoid becoming systematically targeted infrastructure for terrorist financing operations.
Methodology
Data Collection Framework
NOMINIS conducted a focused empirical analysis examining terror-linked cryptocurrency transaction flows during a defined 24-hour observation period. This timeframe was deliberately constrained to provide a high-resolution snapshot of transaction velocity and destination patterns. The analysis traced funds originating from cryptocurrency wallets associated with designated terrorist organizations as they moved into exchange infrastructure across multiple jurisdictions.
Jurisdictional Risk Classification
Jurisdictions were categorised into three discrete risk tiers based on FATF classifications. Low-risk jurisdictions were defined as countries absent from both the FATF Black List and Grey List. Increased-risk jurisdictions encompassed all countries appearing on the FATF Grey List. High-risk jurisdictions included all FATF Black List countries plus Cambodia and Russia, based on documented patterns of regulatory permissiveness and enforcement gaps.
Transaction Analysis Protocol
Each transaction identified during the observation window was traced from source wallets to destination exchanges. Exchange identification utilised on-chain analysis, corporate registration data, and verified exchange wallet addresses. Critically, not all exchanges could be identified or attributed to a corporation. Transactions were categorised by destination jurisdiction and aggregated to identify concentration patterns and routing preferences.
Difficulty to identify or attribute all exchanges led the analysis to focus exclusively on transactions terminating at identifiable, operational cryptocurrency exchanges. Peer-to-peer transfers, decentralised exchange activity, and transactions to unidentified wallets were excluded to maintain analytical precision and ensure jurisdictional attribution accuracy.
Findings
Overall Transaction Distribution
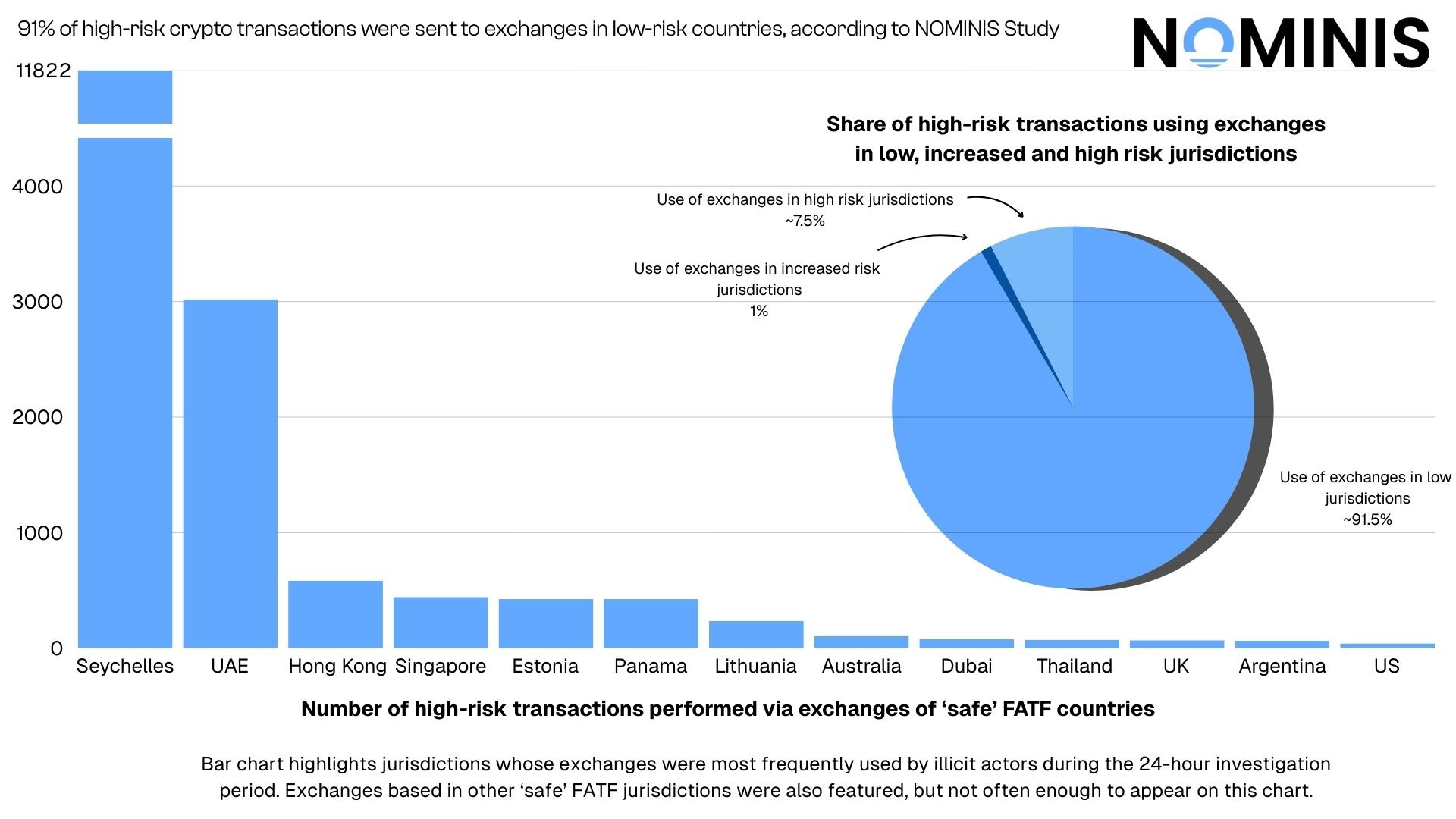
The 24-hour analysis identified 20,322 transactions originating from wallets associated with terrorist organizations and hostile state networks that were sent to identifiable cryptocurrency exchanges. The distribution of these transactions across jurisdictional risk categories revealed a striking pattern that contradicts conventional assumptions about illicit finance routing.
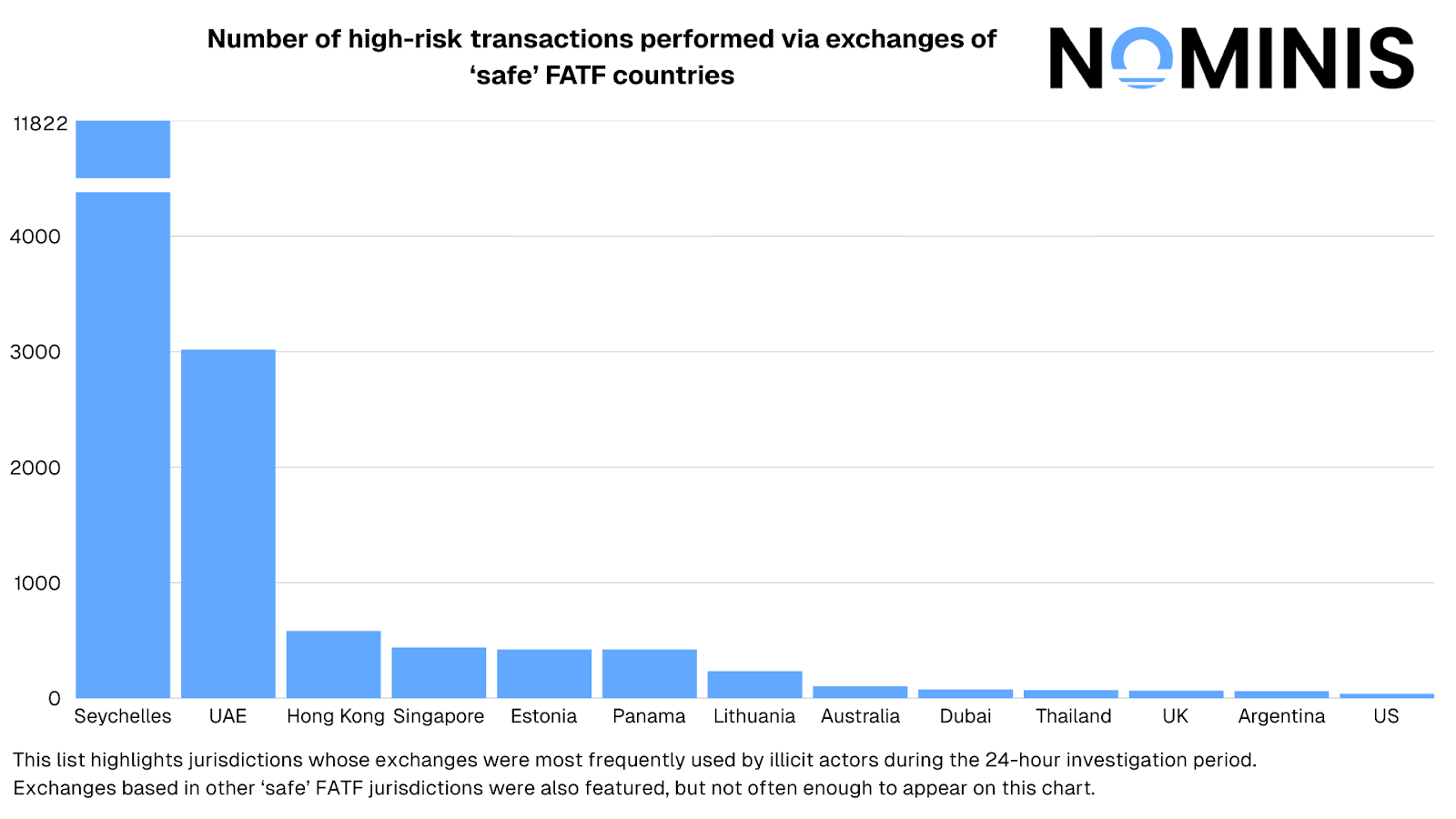
The overwhelming majority of transactions, totaling 18,597 were directed to exchanges operating in low-risk jurisdictions. This represents approximately 91% of all identified terror-linked transactions during the observation period. These transactions were distributed across established financial centers including, but not limited to, the United Arab Emirates, Dubai, Singapore, Australia, the United Kingdom, Cyprus, France, South Africa, and the United States.
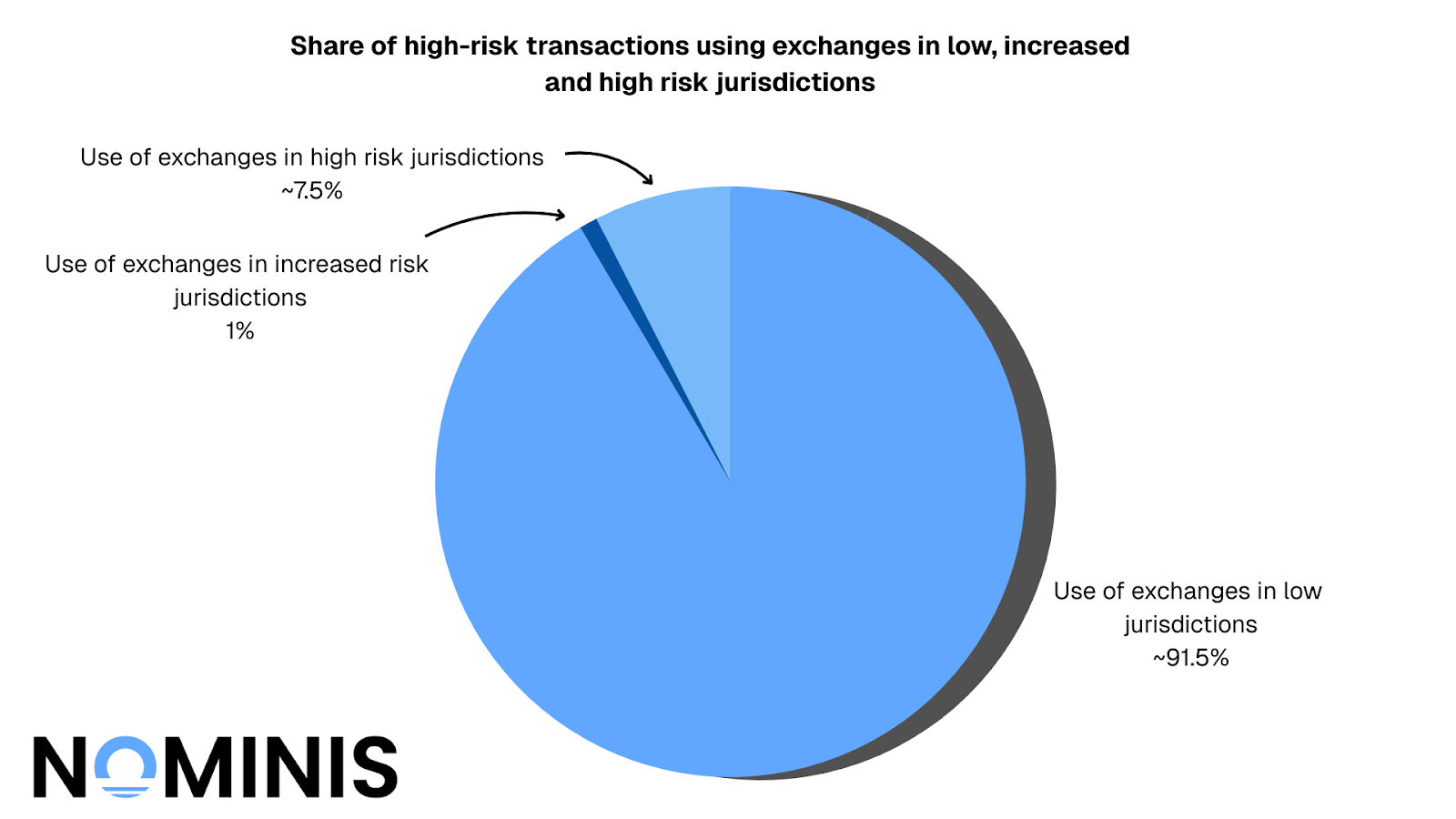
Just 203 transactions, representing merely 1% of the total, were sent to exchanges located in increased-risk jurisdictions appearing on the FATF Grey List, with a notable concentration in the British Virgin Islands.
By contrast, 1522 transactions, representing 7.5% of the total volume, were directed toward exchanges operating in high-risk jurisdictions. This comparatively minimal flow to explicitly high-risk environments demonstrates a clear pattern of avoidance rather than opportunistic exploitation of the weakest regulatory environments.
Strategic Implications of Distribution Patterns
The combined total of transactions sent to low-risk and increased-risk jurisdictions reaches 18,800 representing approximately ~92.5% of all identified terror-linked cryptocurrency transactions during the observation period. This distribution fundamentally challenges the assumption that terrorist financing flows naturally toward the jurisdictions with the weakest regulatory frameworks.
Instead, the data suggests more sophisticated efforts. Terrorist organisations appear to prioritise jurisdictional credibility, operational sustainability, and reduced investigative scrutiny over pure regulatory permissiveness.
Low-risk jurisdictions offer established regulatory frameworks that provide legitimacy, financial infrastructure that connects seamlessly to global markets, and political stability that ensures operational continuity. Most critically, their designation as low-risk, or ‘safe’ often translates into reduced investigative urgency and less aggressive transaction-level scrutiny.
The concentration of terrorist financing activity in these jurisdictions reveals a disturbing reality: the very credibility that low-risk jurisdictions have cultivated through regulatory diligence now serves as a vulnerability that terrorist networks systematically exploit. Without transaction-level monitoring capabilities that look beyond customer identity to analyze behavioral patterns and network connections, these jurisdictions cannot effectively distinguish legitimate cryptocurrency activity from terror-linked operations camouflaged within high transaction volumes.
Transaction Velocity and Network Behavior
The movement of over 20,000 transactions within a single day demonstrates both the scale of ongoing terrorist financing activity and the rapidity with which value can be dispersed across jurisdictional boundaries. This velocity has direct implications for interdiction efforts. Cryptocurrency transactions achieve settlement finality within minutes or hours, meaning that by the time conventional analytical processes identify suspicious activity, assets may have already moved beyond reach.
The distributed nature of transaction destinations accentuates this challenge. Rather than concentrating flows through a small number of choke points, terrorist networks disperse transactions across dozens of exchanges operating in multiple jurisdictions. This distribution strategy reduces individual transaction visibility while overwhelming the analytical capacity of any single jurisdiction's financial intelligence unit.
Real-time Know Your Transaction systems offer the only viable response to this velocity challenge. Unlike retrospective analysis that examines historical transaction patterns, KYT systems monitor transactions as they occur, applying behavioral analytics, network analysis, and risk scoring algorithms that can identify suspicious activity within the narrow window before settlement finality.
The Compliance and Enforcement Gap
The Distinction Between Know Your Customer and Know Your Transaction
The critical gap lies in the distinction between knowing your customer and knowing your transactions. Traditional KYC protocols, while essential, provide only a static snapshot of account holder identity at the moment of onboarding. They cannot detect when legitimate account holders engage in suspicious activity, when accounts are compromised, or when transaction patterns deviate from expected behavioral norms. For cryptocurrency exchanges processing thousands or millions of transactions daily, this static approach creates vast blind spots that terrorist networks exploit systematically.
Compliance systems in low-risk jurisdictions are frequently designed for regulatory satisfaction rather than threat detection. Transaction monitoring systems flag predefined suspicious patterns, but these systems often operate on assumptions more appropriate to traditional banking contexts than to cryptocurrency environments, where transaction velocity, pseudonymity, and cross-border fluidity create fundamentally different risk profiles.
Reactive Enforcement
Law enforcement agencies must allocate finite investigative resources across an expanding universe of potential threats. Rational resource allocation directs attention toward jurisdictions already labeled as high-risk. This creates a self-reinforcing cycle where high-risk jurisdictions receive intensive scrutiny while low-risk environments benefit from assumptions of relative safety.
The reactive nature of enforcement further compounds this challenge. Investigations typically commence after suspicious activity reports are filed or patterns are identified through retrospective analysis. By the time these processes unfold, cryptocurrency transactions have long since settled and assets have moved beyond reach.
For low-risk jurisdictions, the reactive approach creates reputational hazards. Once terrorist networks establish operational patterns using specific exchanges, those patterns become entrenched. The jurisdiction becomes known within illicit finance communities as permissive or exploitable. Retroactive discovery of systematic exploitation generates negative publicity and potential reclassification as higher-risk despite formal compliance frameworks being in place.
Know Your Transaction systems enable the transition from reactive to proactive enforcement. By continuously analyzing transaction patterns, network connections, and behavioral anomalies, KYT capabilities identify emerging threats before they fully materialise.
Operational Camouflage and Strategic Adaptation
Legitimacy Through Association
One of the most insidious aspects of this exploitation pattern is how terrorist networks leverage the reputational credibility of trusted financial ecosystems as operational camouflage. When illicit funds move through exchanges in Singapore, the United Kingdom, or the United States, they benefit from the legitimacy associated with those jurisdictions. Counterparties and compliance systems apply less scrutiny to transactions originating from these environments, assuming that robust regulatory oversight has already occurred.
By routing initial conversions through low-risk exchanges, terrorist networks can generate transaction histories that appear unremarkable to downstream compliance reviews. The cryptocurrency may be converted to stablecoins, transferred to additional wallets, traded across multiple asset pairs, and eventually withdrawn to traditional banking systems, all while maintaining the appearance of legitimate cryptocurrency trading activity.
This is precisely where comprehensive Know Your Transaction monitoring becomes essential. KYT systems analyze not just individual transactions in isolation, but transaction sequences, network patterns, and behavioral anomalies that suggest coordinated illicit activity. By examining factors such as transaction timing, counterparty relationships, fund concentration patterns, and deviation from expected behavioral norms, KYT capabilities can identify suspicious activity that appears benign when examined transaction by transaction.
Adaptive Network Behavior
The transaction distribution patterns suggest highly adaptive behavior by terrorist networks. Rather than concentrating funds in single jurisdictions, the observed transactions dispersed across numerous destinations spanning multiple continents and regulatory regimes. This distribution strategy reduces single-point-of-failure risk while complicating investigative coordination.
The diversity of destination jurisdictions suggests continuous reconnaissance and testing of compliance effectiveness. Terrorist networks appear to systematically probe different exchanges and jurisdictions, identifying those with weaker transaction monitoring or slower enforcement responses. This reconnaissance enables dynamic adaptation, with transaction flows shifting toward the path of least resistance.
The adaptive nature of these networks means that static compliance measures inevitably fall behind evolving tactics. Know Your Transaction systems address this adaptive challenge through continuous learning and behavioral analysis. Rather than relying on fixed rules that adversaries can study and circumvent, effective KYT platforms employ machine learning algorithms that identify anomalous patterns, adapt to emerging typologies, and incorporate new threat intelligence as it becomes available.
For low-risk jurisdictions, this adaptive capability is essential. As terrorist networks continuously probe for vulnerabilities and shift transaction flows toward less protected infrastructure, jurisdictions without advanced monitoring capabilities become systematically targeted. The 91% concentration of transactions in low-risk jurisdictions demonstrates this targeting in action.
The Imperative for Know Your Transaction Implementation
Why Low-Risk Jurisdictions Are Primary Targets
The empirical evidence demonstrates unambiguously that low-risk jurisdictions have become the primary target for terrorist financing operations using cryptocurrency. This finding carries an urgent imperative: jurisdictional credibility and formal regulatory frameworks no longer provide sufficient defense against exploitation. The very characteristics that make these jurisdictions attractive for legitimate financial activity also make them attractive for illicit operations seeking to camouflage within high transaction volumes and benefit from reputational legitimacy.
Know Your Transaction monitoring represents the essential defensive capability that can prevent low-risk jurisdictions from becoming permanent infrastructure for terrorist financing. Unlike static Know Your Customer protocols that verify identity at onboarding but provide no ongoing visibility into transaction behavior, KYT systems continuously analyze transaction patterns, network connections, and behavioral anomalies that indicate potential illicit activity.
The Technical and Economic Case for KYT
Effective KYT implementation in low-risk jurisdictions would fundamentally alter the risk calculus that currently favors terrorist network exploitation of these environments. Rather than offering reduced scrutiny and extended operational windows, exchanges in low-risk jurisdictions would provide real-time behavioral monitoring, immediate suspicious activity detection, and rapid interdiction capabilities.
The technical capabilities for comprehensive KYT monitoring exist and are actively deployed by leading exchanges globally. Blockchain analysis platforms provide real-time transaction tracing, network analysis, risk scoring, and automated alert generation. These systems integrate with global threat intelligence databases, incorporate machine learning algorithms that adapt to emerging typologies, and generate actionable intelligence for compliance teams and law enforcement agencies.
The economic case for KYT implementation is equally compelling. While systems require investment in technology and personnel training, these expenses pale in comparison to the reputational damage, regulatory penalties, and enforcement actions that follow retrospective discovery of systematic terrorist financing facilitation. Exchanges that implement robust KYT capabilities avoid becoming focal points for law enforcement investigation and maintain access to banking partnerships that attract legitimate institutional customers.
Policy and Regulatory Framework
From a policy perspective, regulatory authorities in low-risk jurisdictions should recognise KYT implementation as essential infrastructure for maintaining their jurisdictional risk classification. As the empirical evidence demonstrates systematic targeting of low-risk environments by terrorist networks, continued absence of transaction-level monitoring capabilities represents a material vulnerability that may ultimately warrant jurisdictional reclassification or enhanced international scrutiny.
Mandatory KYT requirements for cryptocurrency exchanges would create several beneficial effects. First, they would establish minimum monitoring standards applicable to all market participants, preventing regulatory arbitrage. Second, they would signal to international partners that the jurisdiction takes cryptocurrency-related terrorist financing threats seriously. Third, they would provide clear compliance expectations for exchanges, reducing uncertainty and enabling long-term planning.
The alternative to proactive KYT implementation is continued exploitation, eventual discovery, and reactive enforcement that damages both individual institutions and broader jurisdictional reputation. The pattern documented in this report represents ongoing systematic exploitation, not isolated incidents. Every day that low-risk jurisdictions operate without comprehensive transaction monitoring represents another day of potential terrorist financing facilitation.
Recommendations
Mandatory KYT Implementation
Regulatory authorities in low-risk jurisdictions must mandate comprehensive Know Your Transaction monitoring for all cryptocurrency exchanges as a core condition for licensing. KYT mandates should specify minimum functional capabilities including real-time transaction monitoring, behavioral analytics, network analysis, integration with global threat intelligence databases, automated risk scoring, and suspicious activity alert generation.
Phased implementation schedules should prioritise high-volume exchanges while providing extended timelines for smaller operators. Compliance verification should include regular audits of KYT system performance, review of suspicious activity report quality, and assessment of integration with financial intelligence unit reporting mechanisms.
Enhanced Grey List Monitoring
Targeted enhancement of monitoring capabilities for exchanges operating in FATF Grey List jurisdictions represents a high-leverage intervention opportunity. International development programs should prioritise cryptocurrency investigative capacity building in Grey List jurisdictions, providing training in blockchain forensics and terrorist financing typology recognition. Enhanced due diligence requirements for correspondent banking relationships with institutions in Grey List jurisdictions could incentivise compliance improvements while limiting terrorist financing facilitation.
International Standards and Coordination
International standard-setting bodies should develop specific guidance addressing cryptocurrency transaction monitoring in low-risk jurisdictions. Technical standards should address KYT system functionality, performance benchmarks, threat intelligence integration requirements, and suspicious activity reporting protocols specific to cryptocurrency contexts. Cross-border coordination mechanisms should be enhanced to enable rapid information sharing about emerging terrorist financing typologies and suspicious wallet addresses.
Conclusion
The empirical analysis presented in this report demonstrates conclusively that terrorist organizations and hostile state networks are systematically exploiting cryptocurrency exchanges in low-risk and increased-risk jurisdictions, with approximately 94% of identified terror-linked transactions targeting these environments. This pattern reflects sophisticated strategic calculation that prioritises jurisdictional credibility and reduced enforcement scrutiny over regulatory permissiveness.
The concentration of terrorist financing activity in jurisdictions perceived as safe creates a fundamental challenge for the global counter-terrorism finance architecture. Current frameworks that prioritise enforcement resources toward high-risk jurisdictions while assuming relative safety in compliant environments have created exploitable blind spots that adversarial networks recognise and systematically target.
Most critically, low-risk jurisdictions must recognise that their hard-earned credibility and formal regulatory frameworks no longer provide sufficient defense against sophisticated terrorist financing operations. The 84% concentration of terror-linked transactions in these environments represents deliberate targeting by adversarial networks that understand and exploit gaps in transaction-level monitoring.
Know Your Transaction monitoring represents the essential capability that can transform low-risk jurisdictions from exploited conduits into effective barriers against terrorist financing. By implementing comprehensive, real-time behavioral monitoring that looks beyond customer identity to analyze transaction patterns, network connections, and behavioral anomalies, exchanges in low-risk jurisdictions can detect and interdict illicit activity before it achieves operational objectives.
The imperative for KYT implementation extends beyond regulatory compliance to encompass reputational preservation, competitive differentiation, and genuine contribution to global counter-terrorism efforts. Exchanges that proactively adopt advanced monitoring capabilities demonstrate operational competence and authentic commitment to preventing terrorist financing facilitation. Jurisdictions that mandate KYT as a condition of exchange licensure signal to international partners that their low-risk classification reflects genuine capabilities rather than merely formal frameworks.
The alternative is continued exploitation, eventual discovery, and reactive enforcement that damages both individual institutions and broader jurisdictional reputation. The findings underscore that the most consequential terrorist financing risks no longer emerge exclusively from sanctioned or high-risk jurisdictions. Instead, they manifest at the intersection between hostile actors and financial ecosystems broadly perceived as compliant or trustworthy.
For low-risk jurisdictions, the path forward is clear: implement comprehensive Know Your Transaction monitoring as essential infrastructure for maintaining jurisdictional credibility, preventing systematic exploitation, and genuinely contributing to global counter-terrorism financing effectiveness.
The technology exists, the threat is documented, and the imperative is urgent. Only through action that matches the sophistication of adversarial networks can low-risk jurisdictions ensure their financial infrastructure serves legitimate economic activity rather than becoming the preferred conduit for global terrorist operations.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.






