Executive Summary
Last night, multiple Jewish institutions in the United States received anonymous bomb threat emails demanding payment in Bitcoin. A threat sent to a synagogue closely mirrors a well-documented pattern of bogus bomb threats that appears to first start in 2018. These campaigns are characterized by near-identical wording, recycled intimidation tactics, and critically, the reuse of Bitcoin wallets that have previously appeared in hoax threat emails.
Based on the reuse of a known address and the highly consistent formatting of the message, this incident may represent a copycat attack, rather than a credible operational plot.
This article examines the incident, links it to historical bomb-threat campaigns documented as far back as 2018, analyses the on-chain signals associated with the Bitcoin wallet used in the email, and explains why crypto risk screening and shadow intelligence can play an essential role in rapid, evidence based threat assessment.
This is a developing story. NOMINIS will continue to monitor the situation and update the article as additional verified information becomes available.
Incident Overview: Synagogue receives Bomb Threat Email
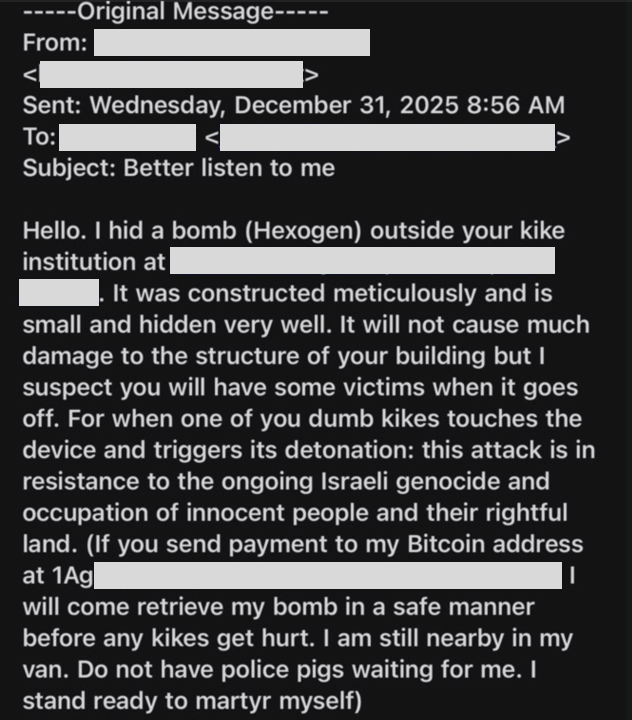
On December 31, 2025, a synagogue received an anonymous email threatening an explosive device allegedly placed outside the synagogue. The message contained explicit hate speech, referenced a specific physical address, and demanded payment in Bitcoin to prevent detonation. The sender claimed the device was small, concealed, and designed to cause casualties rather than structural damage. Law enforcement responded by assessing the threat and prioritizing public safety, and no device was ultimately found.
While the language of the email was deliberately alarming, its structure and phrasing are strikingly familiar to investigators who have reviewed earlier waves of bomb‑threat hoaxes sent to schools, hospitals, and religious institutions across the United States.
Bitcoin Wallet Reuse and Historical Linkage
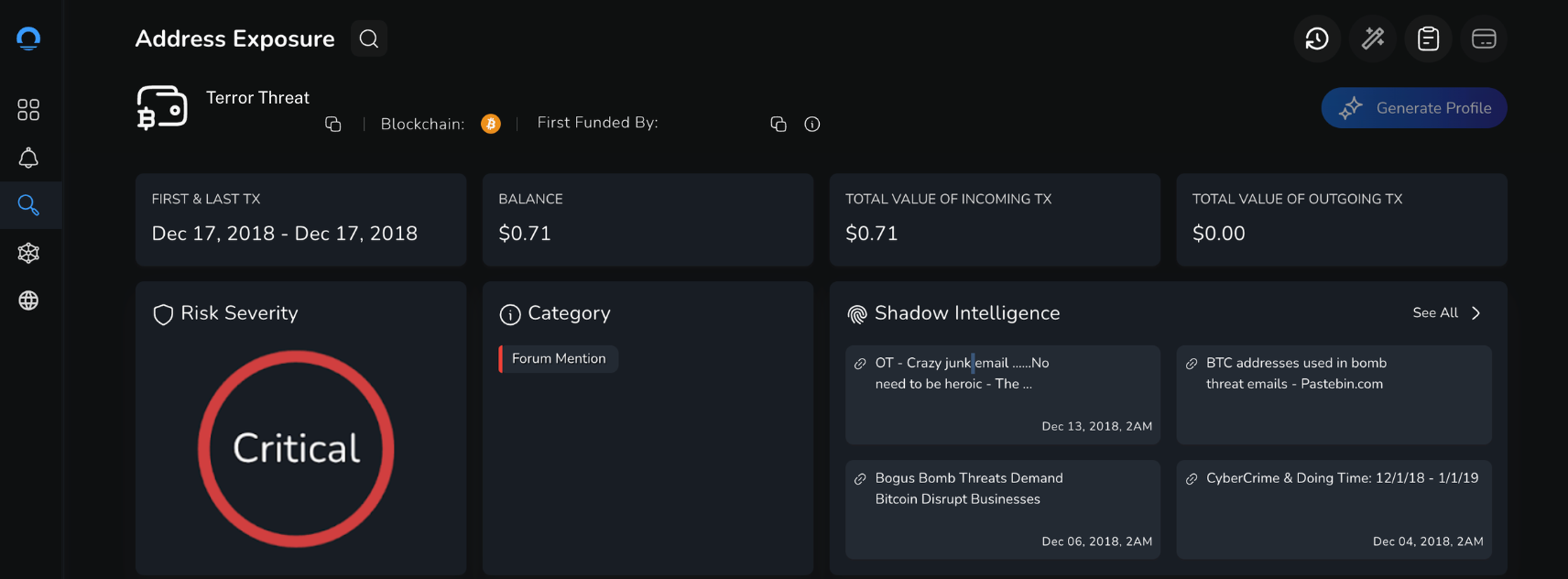
The email demanded payment to the Bitcoin address 1Ag… This wallet is not new. It appears in a historical list of Bitcoin addresses associated with bomb threat emails compiled in 2018, during a period when hundreds of nearly identical threats were distributed nationwide.
In addition to historical reporting, the same wallet has been referenced repeatedly in public abuse-reporting databases. As of this writing, the address has been mentioned nine times on Chainabuse, with reports describing its use in bomb threats and extortion-style emails. The repeated appearance of the same wallet across independent reports strengthens the linkage between the email and earlier threat campaigns.
Wallet reuse across multiple years and multiple reported incidents is a significant analytical signal. In past investigations, this behavior has been consistently associated with hoax or intimidation campaigns rather than credible attack planning. When this address was screened through NOMINIS’ crypto risk monitoring tools, it surfaced historical references and shadow intelligence linking it to prior bomb-threat narratives, reinforcing the assessment that the email received by the synagogue email aligns with an established pattern rather than a novel threat.
Email Formatting and the Copycat Threat Model
Beyond the wallet itself, the formatting and tone of the email strongly resemble examples documented in earlier bogus bomb‑threat campaigns. The message follows the same structure that researchers and journalists described in 2018: a threatening introduction, claims of technical sophistication, assertions that the device is already in place, ideological or political justification, and a demand for Bitcoin as the sole means of resolution.
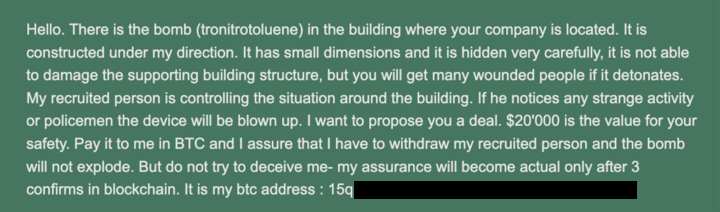
Notably, this structure closely matches examples published in detailed analyses of bogus bomb threats that demanded Bitcoin during earlier waves. The repetition of both wording and layout suggests that the sender may have copied or adapted an existing template rather than crafting an original message. Taken together with the reuse of a historically flagged Bitcoin address, these similarities point toward a copycat campaign leveraging fear and publicity rather than an imminent physical attack. Interestingly, the previous bomb threats did not target Jewish institutions, but rather, companies and businesses.
Expansion to other US Synagogues
Roughly seventeen hours after the Temple Chai incident became known, reports emerged describing a similar anonymous email sent to a second synagogue prompting a significant police presence. According to Reddit Users, authorities indicated that the message had been distributed to multiple Jewish institutions and was not initially considered credible, though security was increased as a precaution.
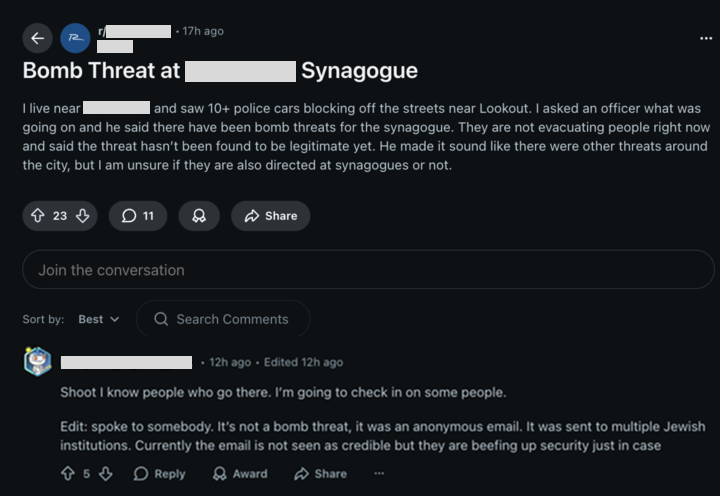
This pattern of mass distribution is consistent with previous hoax campaigns, in which identical or near‑identical emails were sent to numerous targets in order to amplify fear, disrupt daily life, and attract attention without requiring further action by the sender.
The Role of Crypto Compliance and Shadow Intelligence
This incident highlights the importance of combining on‑chain analytics with historical and off‑chain intelligence. Address screening, linkage analysis, and access to archived threat reports allow security teams and investigators to distinguish between genuine risk and recycled intimidation campaigns. Automated crypto compliance tools play a critical role in surfacing these connections quickly, particularly when time‑sensitive decisions must be made.
Conclusion
The bomb threat sent to the synagogue appears to be part of a long‑running pattern of Bitcoin‑based hoax threats targeting public and religious institutions in the United States. The reuse of a Bitcoin wallet previously associated with bomb‑threat emails, combined with the near‑identical formatting and language documented in earlier cases, strongly suggests a copycat attack rather than a credible explosive threat.
For institutions facing similar incidents, rapid crypto wallet screening and access to historical shadow intelligence are essential tools for separating real danger from recycled terror tactics. As this case demonstrates, blockchain transparency can be a defensive advantage when paired with the right investigative context.
NOMINIS continues to monitor and analyze the misuse of cryptocurrency in intimidation campaigns, extremist narratives, and public safety threats.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.





.png)
