On November 4 2025, the U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) announced sanctions against eight individuals, and two entities, facilitating illicit financial networks linked to North Korea’s state sponsored cyber operations. The designations target DPRK financial representatives as well as an IT services company, that helped disguise revenue flows generated by overseas North Korean IT workers, and actors committing social engineering and ransomware attacks.
These actions are part of a broader strategy to disrupt how the North Korean government finances its nuclear weapons and ballistic missile programs. As noted in the Treasury statement, DPRK-affiliated cybercriminals have stolen over $3 billion in cryptocurrency over the past three years. Almost half of this total was stolen in a single but significant attack in February 2025, the Bybit Hack. Hacking entities associated with the State frequently use sophisticated laundering channels to move funds into the global financial system.
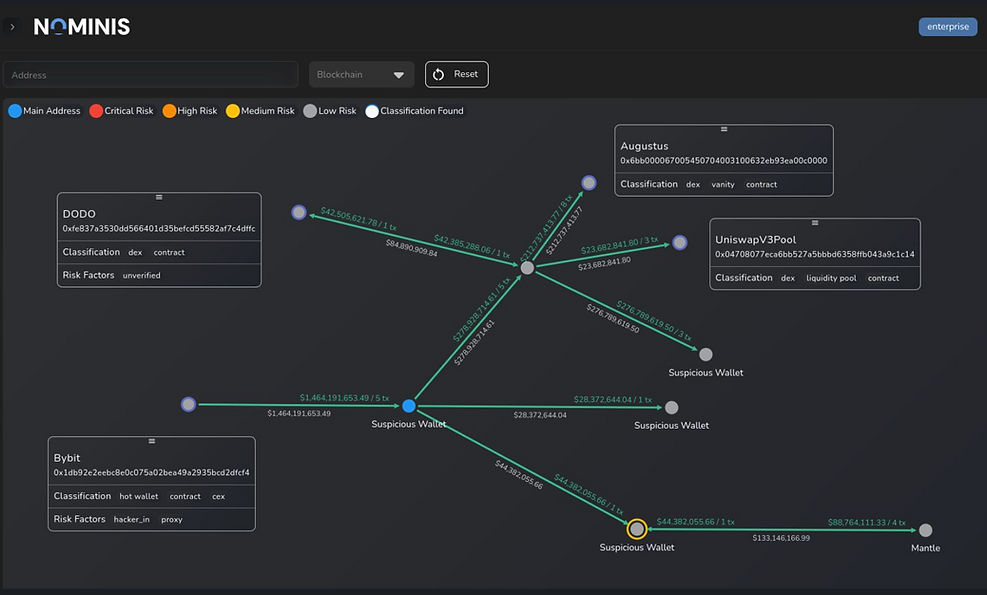
How Transaction Monitoring led to Sanctions
The seizure and attribution of DPRK-linked Cryptocurrency and fiat transactions highlight the growing role of transaction monitoring, blockchain analytics, and compliance reporting in countering state-sponsored cryptocrime.
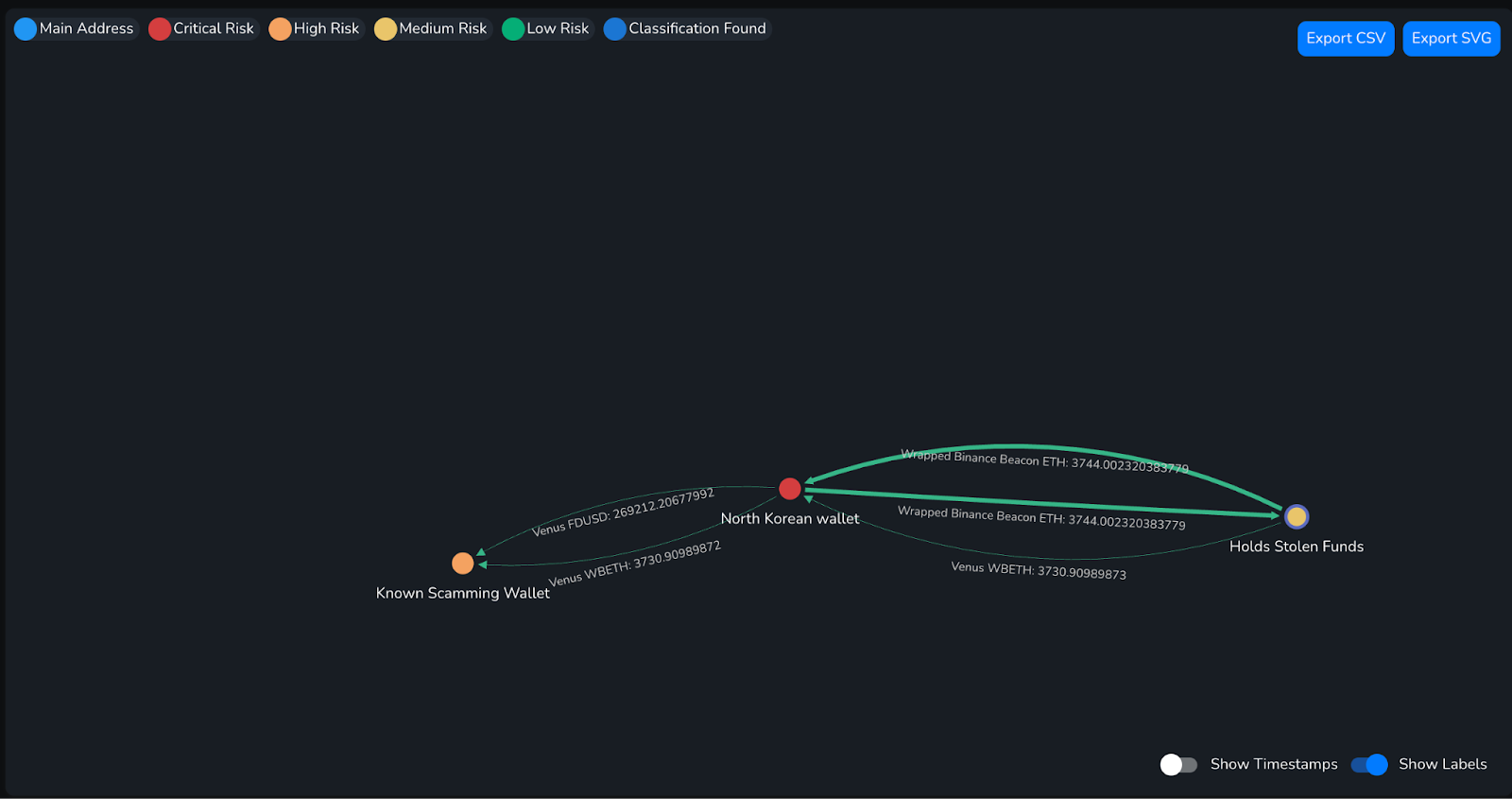
Financial institutions and blockchain analytics firms, certain tools have proved more important than ever:
- Behavioural pattern detecting to flag clusters of small, cross-border transfers.
- Wallet tracing and address clustering to identify DPRK-linked movements, and laundering chains.
These monitoring systems have enabled investigators to link crypto flows from ransomware payments and IT contractor earnings back to DPRK-controlled financial entities, such as First Credit Bank, Koryo Commercial Bank, and the Foreign Trade Bank, as well as IT company Korea Mangyongdae Computer Technology Company (KMCTC).
Based in North Korea, the company operates IT worker delegations across China. Workers have used Chinese nationals as banking proxies, in order to obfuscate the origin of funds generated by the DPRK IT workers’ illicit revenue generation schemes, which include social engineering crypto scams and large scale hacks on crypto entities.
Nominis Insights actively warned against shifts
Throughout 2025, we have regularly published insights on the notable shifts we have recognised in North Korean proliferation financing tactics.
Specifically, we warned that North Korean operators had begun:
- Targeting high-net-worth individuals directly, given their reduced level of protections compared to enterprises
- Performing covert operations, including infiltrating crypto companies with fake identities
- Using AI to impersonate professionals and deceive victims into downloading malware
- Conducting Telegram-based scams to establish trust, and extract funds.
These techniques allowed DPRK IT workers to secure contracts under fabricated identities and to collaborate with unsuspecting foreign developers to launder earnings. This tactic was directly referenced in OFAC’s designation of Korea Mangyongdae Computer Technology Company (KMCTC) and its China-based worker delegations.
Nominis also repeatedly warned that DPRK’s cyber operations are not merely financially motivated, but strategically aligned with proliferation financing, the funding of missile development, nuclear research, and military procurement. As a hostile state with intentions to develop Weapons of Mass Destruction, the importance of DoJ’s sanctions cannot be overstated, and confirms the continuity of this threat.
It also validates the early detection work we performed, and the contributions of our shared research, data and software for continuous monitoring.
Concluding thoughts:
The sanctions reinforce several critical realities:
- Cybercrime and IT freelancing now form core revenue engines for North Korean state financing
Blockchain-based laundering has become highly structured and globalised - Private-sector detection and transaction monitoring are now indispensable in national security enforcement
Looking ahead, as DPRK tactics evolve, monitoring efforts must increasingly focus on:
Continuous monitoring - a holistic, 24/7 approach to ensure comprehensive analysis
IT freelancers - with inconsistent identity documents, or VPN masking
Crypto Transactions - with rapid chain-hopping, involvement with mixers, and high-value transfers from DeFi platforms
Banking Proxies - China- and Russia- based intermediaries handling structured transfers or currency exchange services
Financial institutions, crypto exchanges, and fintechs must maintain continuous monitoring, and information sharing between private and public sectors will naturally remain central to preventing the financing of future weapons development.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.



.png)