North Korean cyber criminals, particularly Lazarus Group and its subunit BlueNoroff, have intensified their efforts to infiltrate the cryptocurrency sector. Employing sophisticated tactics such as deepfake video calls, fake job offers and spear-phishing campaigns via platforms like Telegram, they aim to deceive individuals into downloading malware or granting unauthorised access to their digital assets.
Deepfake Video Calls: A New Weapon in Cybercrime
September 2025 presented a new trend: the use of hacked Telegram accounts and video call invites - to target or ‘spear phish’ particular individuals and the assets in their crypto wallets. This method represents a significant evolution in cyberattack strategies, leveraging AI generated deepfakes to impersonate trusted contracts and build credibility.
Case Study 1: THORChain Co-founder’s Wallet Drained
On 9 September 2025, John-Paul ‘JP’ Thorbjornsen, founder of THORChain, lost $1.3 million in a theft from his personal wallet. The attack took place when a friend’s Telegram account was hacked. After accepting a Zoom call invitation, JP saw a deepfake of his friend, clicked a link during the call, though did not identify any suspicious messages or requests. He believed they gained access to his encrypted iCloud, keychain, or Chrome profile, and drained his previously forgotten MetaMask wallet. In an attempt to recover the lost funds, THORSwap has publicly offered a bounty to the attacker, contacting them on-chain. At the time of publication, funds remain unaccounted for.

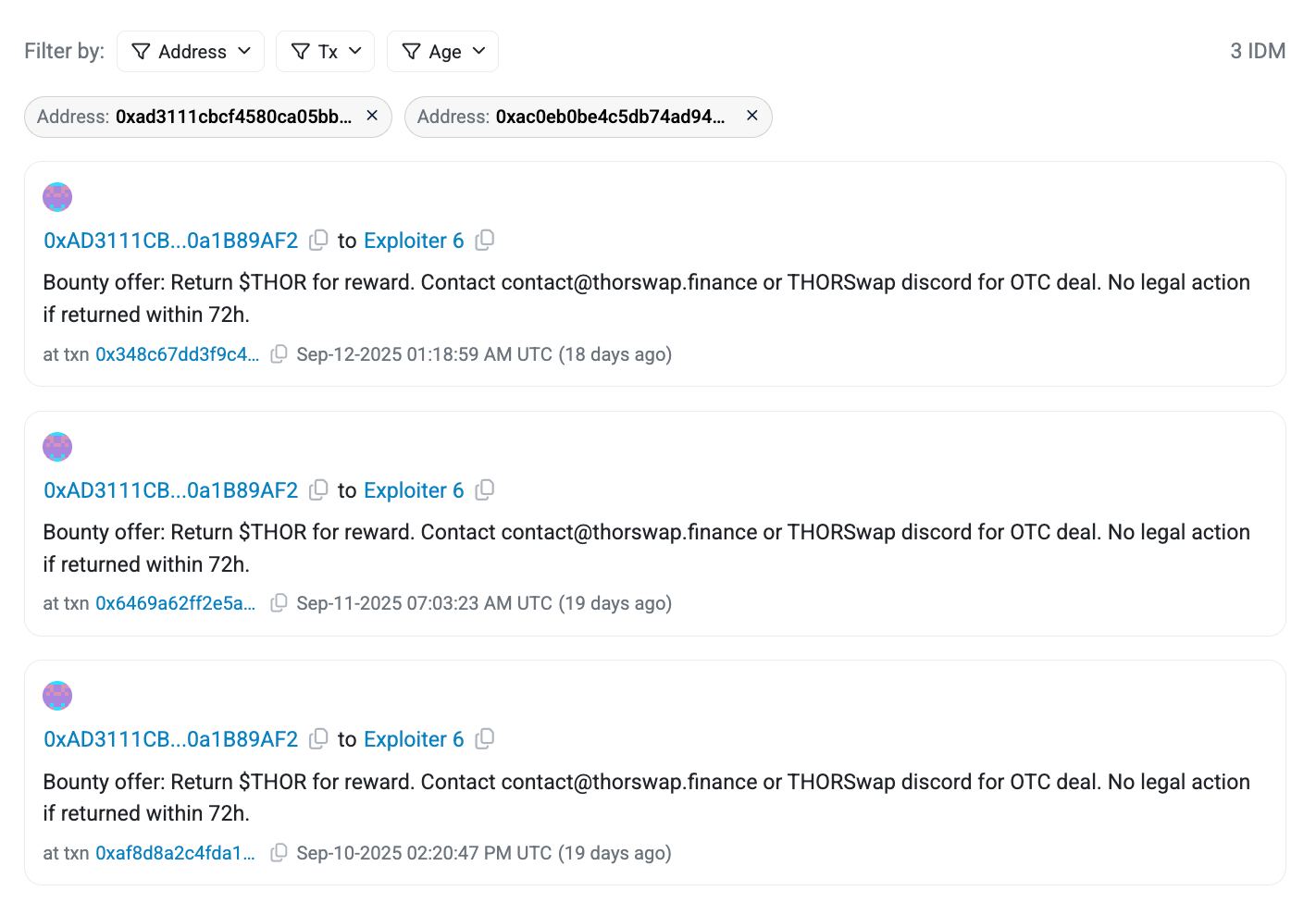
Case Study 2: Venus Protocol Whale Attack
Even earlier in the month, a similar incident occurred. A Venus Protocol whale, @KuanSun1990 (X) fell victim to a phishing attack. The attacker gained access to the user’s account by sending a Telegram link leading to a fake Zoom Meeting. Once the victim joined, malware was installed, granting the attacker borrowing and redeeming rights over approximately $13 million worth of assets. The Venus team recovered all funds after successfully seizing the hacker’s position. In fact, the attacker actually incurred a loss of $2.7 million due to the failed heist. In a post, the whale himself asserted that this behaviour was the work of Lazarus.
These incidents highlight a disturbing trend: North Korean hackers are increasingly targeting individuals within the cryptocurrency sector, leveraging advanced technologies and social engineering tactics. The use of deepfakes represent the significant growth and evolution of their tactics, tailored to target both large exchanges like Bybit, and individual whales and project founders. These pose new challenges for cybersecurity professionals and cryptocurrency users alike.

Why have North Korea shifted their Target?
Unlike institutional exchanges or custodians with advanced cybersecurity infrastructure, high-assets individuals often lack enterprise-grade protections. They may rely on personal devices, simple password storage, or browser based wallets. This makes them the ideal target.
North Korean-linked groups understand this vulnerability. This approach is personal, persistent and patient. These schemes may not aim to only steal money, but also aim to harvest information about wallet structures, browser extensions, and personal security habits that can be later exploited.
Diversion of Stolen Cryptocurrency to fund Proliferation Efforts
The funds illicitly obtained through these cyberattacks are not merely financial gains for the perpetrators, but are suspected to be strategically diverted to support North Korea’s proliferation activities. In February 2025, we released a report discussing the way stolen cryptocurrency is laundering through various mechanisms including mixers, and then used to finance the development of weapons of mass destruction (WMDs), such as ballistic missiles, and nuclear programs.
In 2025 alone, North Korean hackers are estimated to have stolen over $2 billion in cryptocurrency, surpassing the $6 billion mark in cumulative thefts to date. These funds are funnelled into the regime’s military programs, including the development of intercontinental ballistic missiles (ICBMs) and nuclear weapons, thereby circumventing international sanctions and contributing to regional instability. Cyber activities contribute significantly to North Korea’s foreign currency earnings, highlighting the critical role in cybercrime in sustaining the regime’s military ambitions.
Following the historic Bybit attack in February 2025, The FBI determined that specific North Korean cyber operations such as the ‘TraderTraitor’ operation as responsibility for the $1.5 billion theft in virtual assets. These stolen assets were rapidly converted into bitcoin and other virtual currencies, and dispersed across multiple blockchain addresses, making tracing and recovery incredibly complex. They are ultimately laundered and converted into fiat currency, facilitating the funding of North Korea’s proliferation programs.
Implications for the Crypto Industry
The rise of deepfake assisted scams underscores a critical need for both individuals and institutions to rethink digital trust. Cybersecurity has evolved past passwords or firewalls. It now hinges on verifying human authenticity in a world where state actors can mimic video and voice very convincingly.
Crypto professionals, especially founders, developers and investors should:
- Treat unexpected video calls and meeting links as potential phishing attempts
- Use dedicated air-gapped devices for managing private keys
- Adopt Know Your Transaction (KYT) and wallet screening solutions to detect risky interactions.
The next frontier of crypto security will depend of collaboration between intelligence platforms, blockchain analytics providers, and global regulators, to close pathways that enable these types of attacks.
The role of Nominis in Combating Crypto-Enabled Threats
As state-sponsored attacks grow more sophisticated, transaction intelligence and monitoring platforms like Nominis.io play a critical role in identifying and mitigating these threats.
Nominis Vue continuously tracks and analyses on-chain activity linked to high-risk wallets, clusters and typologies, including those associated with DPRK-linked laundering networks. Through real-time monitoring and attribution, Nominis helps exchanges, custodians and compliance teams to:
- Detect connections to sanctions or high-risk wallets before funds are accepted
- Identify behavioral
- red flags that suggest spear phishing or wallet compromise
- Provide digestible intelligence reports that translate complex blockchain data into actionable insights
Automated detection and advanced entity clustering allows Nominis users to maintain compliance, protect their users, and proactively block funds linked to state-backed threat actors, closing the gap between financial crime and national security.
Conclusion
The use cases of September 2025 serve as a stark reminder of how quickly cybercrime tactics and targets change, and how deeply intertwined crypto theft remains with state-level proliferation financing.
As North Korean hackers deploy deepfakes, Telegram social engineering and advanced laundering techniques, the crypto industry must respond with intelligence driven monitoring, proactive compliance, and heightened vigilance.
Through platforms like Nominis.io, exchanges, institutions and high-asset individuals can not only protect themselves from direct losses but also play a vital role in preventing stolen digital assets from fueling real-world threats.
FAQs:
Q: How are North Korean hackers using Telegram to steal cryptocurrency?
North korean hackers such as Lazarus Group and BlueNoroff are increasingly using Telegram to launch targeted spear-phishing attacks. They compromise or impersonate trusted contacts, send video call invitations and share malicious meeting links. Once victims join these fake calls, malware in installed, or credentials are stolen, as in the cases seen over the last month, giving attackers control over wallets and crypto assets.
Q: What are deepfake video call scams?
Deepfake video call scams involve using AI generated video and voice to impersonate a known person, like a colleague, founder or investor, during a live call. North Korean cyber groups have recently adopted this method to make phishing attempts far more convincing.
Q: Why are high-asset individuals being target instead of crypto institutions like exchanges?
Large exchanges and custodians now operate with advanced security and compliance systems. In contrast, high-asset individuals, including project founders, DeFi whales and investors, often rely on personal devices or browser based wallets. This makes them easier targets for tailored social engineering attacks.
Q: How can individuals protect themselves from Telegram and deepfake scams?
To protect against these threats, individuals should:
- verify all video calls invitations, and double-check sender identities and their contact information.
- Avoid clicking links shared via Telegram or other chat platforms
- Store crypto assets on air-gapped or hardware wallets
- Use multifactor authentication and avoid syncing sensitive data to cloud accounts
- Rely on transaction intelligence tools that monitor for high-risk wallet interactions.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.



%20.jpg)


