October 2025 was marked by a surge of sophisticated and diverse crypto-related security incidents, reflecting both the growing complexity of blockchain ecosystems and the persistence of attackers and threat actors.
Over the course of the month, the Nominis Intelligence Team recorded a series of high-impact exploits, contract vulnerabilities and private key compromises that collectively resulted in tens of millions of dollars of losses across multiple networks.
The month’s data highlighted newly emerging patterns, including attackers exploiting new standards and interoperability mechanisms to bypass traditional security assumptions. Several incidents, such as the EOA delegation exploit, and Squid Router attack, demonstrate how even minor coding oversights could cascade into significant losses.
Beyond individual attacks, October also saw major regulatory and geopolitical developments shaping the crypto security environment, from the US Department of Justice’s $73 million pig-butchering takedown, to the pardoning of Binance founder Changpeng Zhao by the American President. These events underscore how criminal, technical and policy dynamics are converging to define the next phase of digital asset risk.
This report provides an in-depth review of the most significant exploits and incidents observed through October 2025, along with exclusive Nominis Intelligence findings that trace illicit asset flows and emerging nation-state tactics within the global crypto ecosystem.
Major Attacks in October 2025
Externally Owned Account - 03/10/2025
Type: Contract Vulnerability
In early October, an Externally Owned Account (EOA) suffered sizeable losses after delegating control to an insecure contract under the new EIP-7702 standard, which allows EOAs to temporarily behave like smart contracts. The victim’s wallet was delegated to a contract which contained a publicly callable function, pancakeV3SwapCallback() with no access restrictions, which meant anyone could trigger it to transfer funds. An attacker exploited this flaw by directly calling the function and draining the EOA’s balance. This incident highlights a new, very serious risk introduced by the use of the EIP-7702: even EOAs with uncompromised private keys can lose funds in their delegation contracts are poorly coded. As EIP-7702 adoption grows, users and developers ought to treat delegation contracts with exactly the same security rigor as smart contracts, and never delegate to unaudited or unverified code.
Impact: $336,000.00
Abracadabra - 05/10/2025
Type: Contract Vulnerability
Several days later, the DeFi lending protocol Abracadabra Money (creator of the MIM stablecoin) suffered a significant hack when an attacker exploited logic flaws in the protocol’s smart-contracts. The attacker used the protocol’s deprecated ‘cook’ functions in v4 cauldrons on Ethereum to perform multiple operations on one transaction: first borrowing funds, then triggering an error path that reset the protocol’s solvency-check state, as the function defaulted to 0, to bypass borrowing limits. After draining millions of MIM, the attacker laundered the funds via Tornado Cash. The protocol responded by buying back an equal number of MIM on the market, in order to shore up the peg and prevent fluctuation.
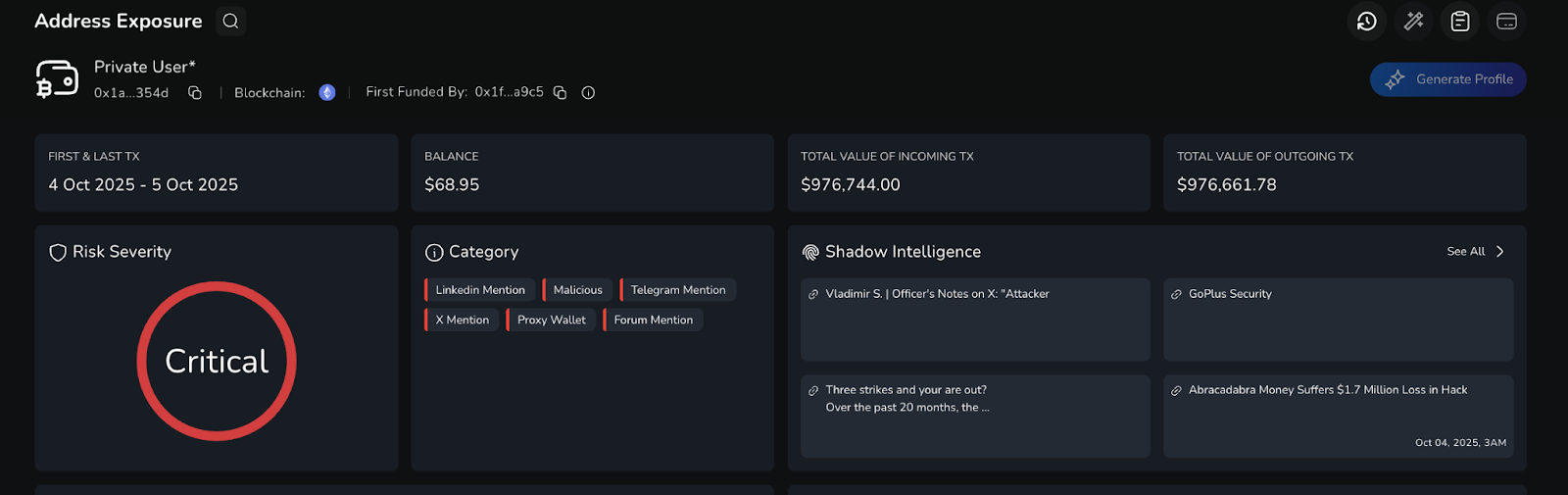
Running the attacking address through the Nominis Vue Address Exposure tool, information about the attacker’s activity can be revealed. It appears the vast majority of funds that entered the wallet were swiftly moved elsewhere. Below, a visualisation from the Nominis Vue Transaction Tracker Tool demonstrates flow of such funds to a wallet known to be Tornado Cash, specifically wallet ***f31b, which is sanctioned.
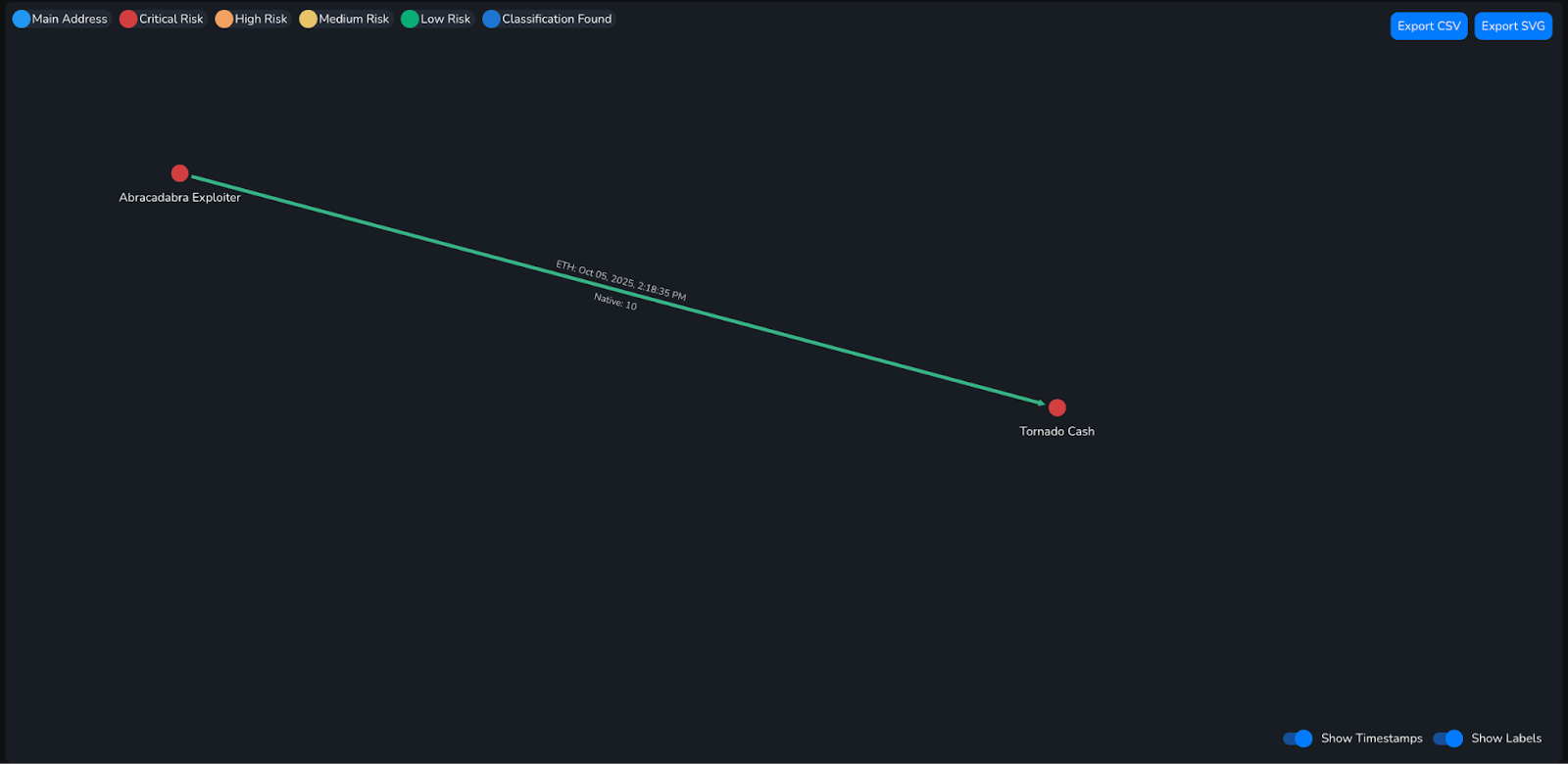
Impact: $1,800,000.00
VeloraDEX's (formerly ParaSwap) - 07/10/2025
Type: Contract Vulnerability
On 7th October, an attacker exploited a known vulnerability in VeloraDEX (formerly known as Paraswap)’s Augustus V6 contract, to steal approximately $20,000 in USDC from a user who had not revoked their token approvals. Despite earlier white hat recovery efforts, mentioned in an X post from March 2024, some wallets, including the victim’s, remained exposed. The attacker used the exploit to drain funds in a single transaction.
Impact: $20,000.00
Squid Router - 07/10/2025
Type: Logic flaw
On the same day, a logic bug in Squid Router’s sponsorOrderUsingPermit2() function, which selected the wrong token, was exploited across five chains: BSC, Ethereum, Arbitrum, Base and Optimism, allowing unauthorized transfers of USDT and USDC, causing over $90k in losses. Though the flaw was a simply one it was highly consequential, as attackers, identified as both MEV bots and wallets funded via Tornado Cash, quickly weaponised the permit path, and drained funds from multiple deployed instances of the contract. Ultimately the simple coding error led to widespread cross-chain impact.
Impact: $90,000.00
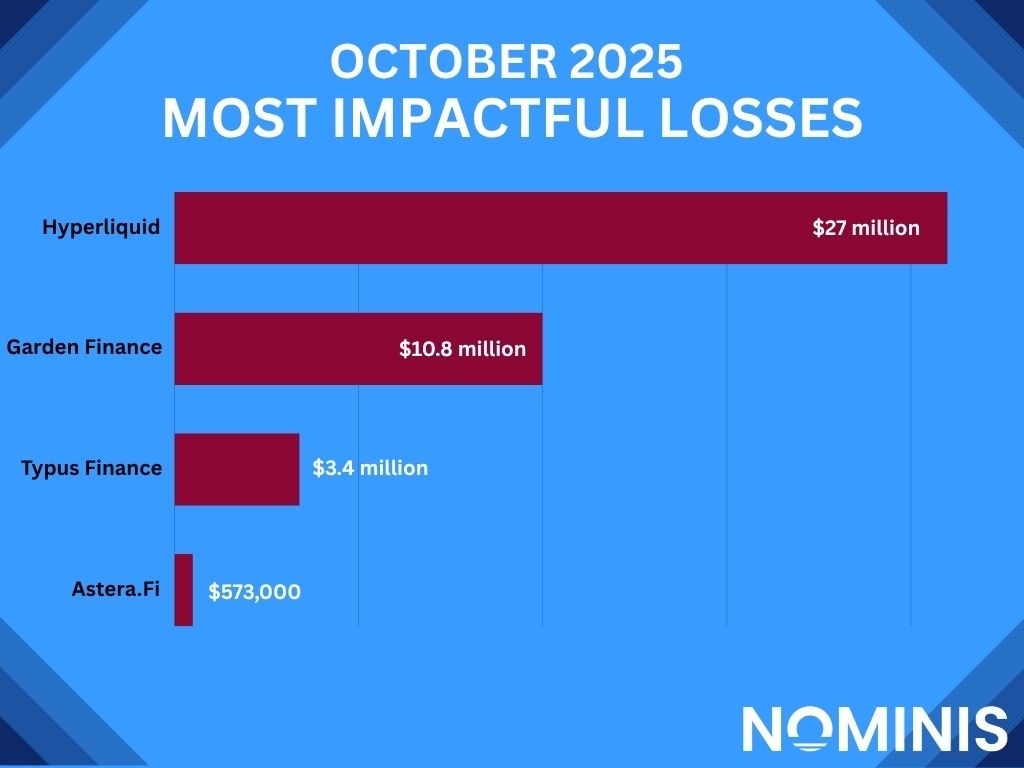
Astera.fi - 09/10/2025
Type: Protocol Logic
AstraFi suffered an exploit caused by an oracle malfunction that mistakenly valued USDT at $154 instead of its real price - $1. Taking advantage of this error, the attacker used 10 ETH from Tornado Cash, bridged it to the Linea network, deposited 6,000 USDT (which the faulty oracle valued at $900,000), and then borrowed roughly $573,000 against it before the mistake was caught. Once the attack was detected, AstraFi paused its Core and Mini Pools, suspended deposits and withdrawals, and warned users not to trade while they worked with security partners to trace and recover the stolen funds.
Impact: $573,000.00
Hyperliquid - 10/10/2025
Type: Private Key Leakage
The following day, a hacker stole over $20 million worth of crypto from a Hyperliquid user, after their private key was leaked. The attacker had full control over the wallet, moving the stolen fund, including $17 million worth of DAI stablecoin, to Ethereum. It appears that due to the hack, Hyperliquid’s token has reduced 22% over the last month, and 15% in the week of the attack. This hack proved to be one of the largest attacks of October.
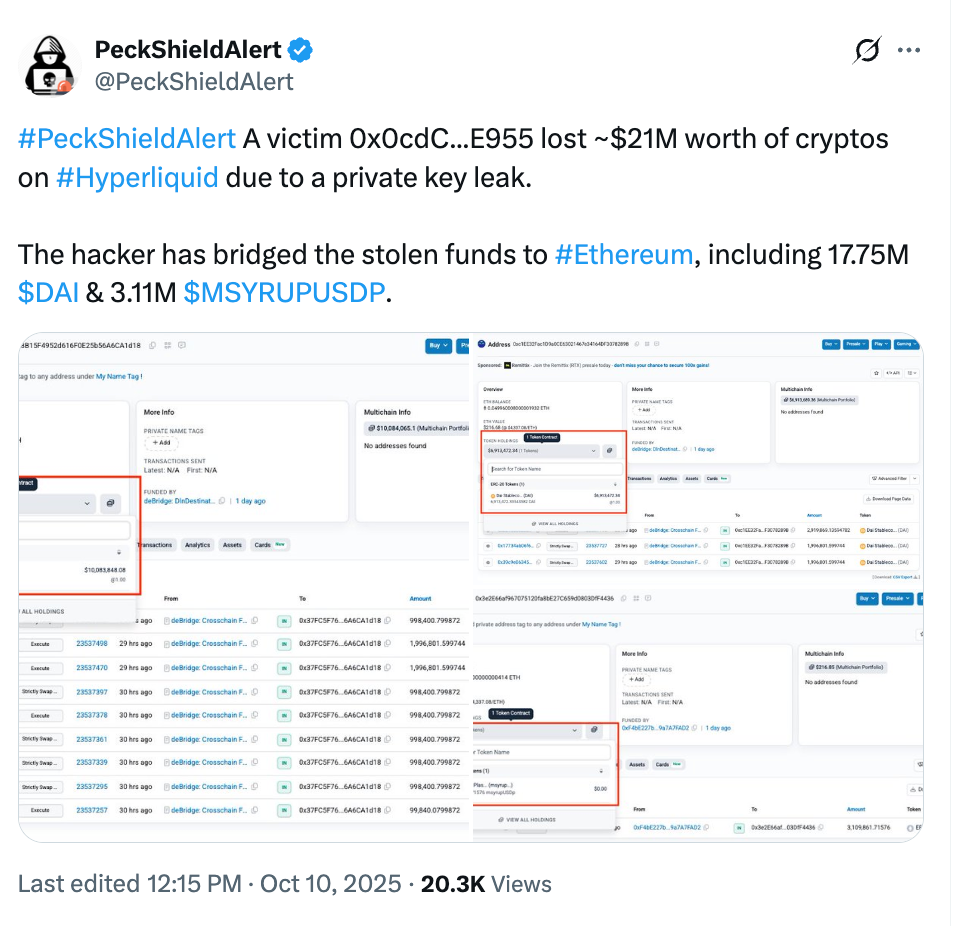
Impact: $21,000,000.00
OracleBNB - 10/10/2025
Type: Rugpull
On the same day, OracleBNB, a blockchain-based oracle solution, appeared to have committed a rugpull after a ‘short but intense spike in trading activity’, when the token’s price surged by over 1,200% to then crash by more than 95%. Following this spike, all social media accounts appear to have been deleted, suggesting an exit scam by the project creators.
Impact: $48,000
Typus Finance - 15/10/2025
Type: Contract Vulnerability
In mid October, Typus Finance suffered a major oracle exploit that drained a significant amount from its TLP contract, including SUI, USDC, xBTC and suiETH. The attacker took advantage of a missing authorization check in the update_v2 function of the oracle module, which allowed anyone to alter oracle prices and manipulate asset values. Although the compromised oracle had existed since November 2024, it was seemingly not included in the project’s May 2025 audit, and the monitoring system failed to flag the attack in real time. According to their post-mortem, Typus paused all contracts 15 minutes after detecting the issue, reported the incident to the Sui Foundation and law enforcement, and confirmed that user wallets, SAFU funds, and DeFI Options Vaults were unaffected thanks to separate oracle verification systems. The team is now acting to trace stolen funds ,redeploy secure contracts and create an asset recovery plan.
Impact: $3,440,000.00
Sharwa Finance - 20/10/2025
Type: Price manipulation
Towards the end of October, Sharwa suffered two consecutive exploits totaling almost $150,000, causing a flaw in its swap function, which according to their post-mortem, lacked both slippage protection and post-swap validation. The attacker manipulated the WBTC price using flash loans after depositing USDC as collateral and exploiting the system’s failure to verify account health after swaps. This allowed them to crash WBTC prices on Uniswap, close their positions at an artificial low, and profit from the price difference. The absence of Chainlink oracle checks further eased the manipulation, according to Sharwa itself.80% of the stolen funds in the first attack have been recovered, approximately $40,000, however the second attacker remains unknown.
Impact: $62,000.00 ($40,000 recovered)
DoodiPals - 20/10/2025
Type: Private Key Leakage
On the same day, the SOL-based project DoodiPals suffered a major security incident in which its private keys were compromised by a hacker. The attacker utilised this breach to liquidate tokens across multiple wallets, extracting 917 SOL. Upon recognising the attack, DoodiPals posted a warning on their X account to update users, and have pledged to conduct a full security audit and offer a 1:1 compensation for holders of the DOODI token, who were affected by the hack.
Impact: $171,000.00
402bridge.fun - 28/10/2025
Type: Private Key Leakage
402bridge.fun, a newly launched cross-chain bridge, suffered a major security incident just days after its domain was registered. According to initial reports, the platform’s smart contract ownership was suddenly transferred to attackers, who then exploited the contract’s permissions to drain users’ funds, most of which were USDC, from wallets that had granted token allowances to the bridge. The project’s website went offline shortly after the exploit, fuelling speculation about whether this was a deliberate rugpull, or a result of poor key management.
Impact: $17,000
Garden Finance - 30/10/2025
Type: Private Key Compromise
At the end of October, Garden Finance, a trustless bridge for BTC, as well as assets on the Ethereum, Arbitrum and Base blockchains among others, suffered a huge exploit. Malicious actors appeared to have executed administrative functions that would only be possible in the position of a key-holder, suggesting a private key compromise took place. The exploit came after prominent blockchain investigators such as ZachXBT accused Garden Finance of involvement in bridging the stolen funds taken during the Bybit hack and other exploits.. According to ZachXBT, an address associated with Garden Finance reached out to the exploiter on chain, offering a 10% bounty.
Impact: $10,800,000
Significant events in October:
DOJ Crackdown on $73 million Pig Butchering Scam
In October 2025, the US Department of Justice announced their seizure of over $73 million in cryptocurrency, linked to a large-scale ‘pig butchering’ romance scam, allegedly tied to Chinese businessman Chen Zhi. The scheme involved luring victims through online relationships and convincing them to invest in fake crypto trading platforms, only to have their funds stolen. Investigators traced the stolen assets through complex laundering routes involving multiple exchanges and mixers before freezing the wallets. The DOJ described the case as one of the largest coordinated crypto scam takedowns to date, underscoring the growing international collaboration against social-engineering-based financial fraud.
Gate.io Security Incident - Phishing via a Third Party Plug-In
In mid-October, Gate.io disclosed a security breach caused by a malicious third-party plugin that compromised some user interactions on its interface. While no user assets stored within Gate’s exchanges infrastructure were affected, the vulnerability allowed attackers to redirect unsuspecting users to a phishing page mimicking Gate.io’s login portal. The exchange swiftly took its website offline, audited all integrations, and confirmed that core trading systems and wallets remained secure. Gate.io’s team has since reinforced plugin validation and launched a user awareness campaign, emphasizing the risks of interacting with unofficial browser extensions or modified front-end scripts.
Bunni Shutdown following September 2025 Exploit
Bunni has announced that it is ceasing operations, following its devastating $8.4 million exploit in September 2025. The exploit exposed a critical rounding-error vulnerability in its smart contracts. The team states that relaunching the protocol would require six- to seven- figure costs for audits, security monitoring and redevelopment; resources that the project no longer has. Bunni has said they will wind down operations, meaning users can still withdraw assets but no further development or roadmap progress will be pursued. The team will distribute remaining treasury assets to token holders (excluding core team members) and has open-sourced their v2 smart contract code under an MIT license, so that others may build on their innovations.
Paxos accidentally mints $300 trillion PYUSD, due to technical error
Paxos, which issues Paypal stablecoin PYUSD, mistakenly minted about $300 trillion worth of PYUSD tokens, due to an internal transfer process error. Paxos has confirmed that rather than a hack, this accidental error was due to a ‘fat-finger’ mistake. The newly minted tokens were rapidly destroyed once detected, however the error was publicly visible on the Ethereum blockchain via explorer data. Paxos stated that no user funds were at risk, and that it was not a security breach.
President Trump Pardons Founder of Binance, Zhao
On 23rd October, Changpeng Zhao, founder of Binance, received a presidential pardon from Donald Trump, wiping his 2023 criminal conviction for failures in anti-money laundering controls and a subsequent four-month prison sentence.
The White House signalled that the pardon marked the end of what is termed the ‘war on cryptocurrency’ under the prior administration and suggested that Zhao’s conviction represented over-enforcement, rather than fraud with tangible victims. However, the decision has sparked controversy, with critics pointing to Binance’s prior $4.3 billion settlement for regulatory violations and questioning whether the pardon blurs the lines between government clemency, and private crypto interests. The DOJ’’s case against Binance accused the company of failing to report over 100,000 suspicious transactions to law enforcement, including crypto movements involving Terrorist groups Hamas and IS.
Nominis Intelligence Team: Exclusive Findings
In October 2025 the Nominis Intelligence Team identified and flagged $1.5 billion of illicit crypto assets from a range of sources, including sanctioned wallets, and complex international criminal operations. These findings have been integrated into our continuously expanding intelligence database, strengthening the analytical capabilities of both Nominis Vue, and CryptoSanctions.net. This ensures our platforms deliver the most informed risk scoring, and comprehensive transaction-mapping, to support proactive compliance and threat detection.
This brings the total amount of illicit assets detected by the Intelligence team to $27 billion since January 2025.
This month also saw Nominis’ release of the landmark report, covering Iran’s shadow banking network. The report, available here, revealed the Iranian Regime’s development of a sophisticated parallel financial system that blends traditional trade-based laundering with cryptocurrency rails, to circumvent sanctions. The analysis shows that Iranian networks use front companies, shell banks in permissive jurisdictions, and stablecoin transfers, to move proceeds from oil and export revenue, into the global financial system, with estimated crypto flows reaching into the hundreds of millions of dollars.
Another Nominis publication this month analysed the sophisticated campaign by North Korean-linked threat groups, including Lazarus Group and BlueNoroff, that target high-net-worth individuals in the crypto space using deep-fake video calls and Telegram-based scams. The group first gained attention in the Nominis September 2025 Report, when their behaviors last month reflected a strategic shift; rather than attacking institutional exchanges, these groups are focusing on individuals with fewer enterprise-grade safeguards.
Insights for October 2025
By the end of October 2025, the crypto ecosystem had recorded over $38 million in confirmed losses from at least 11 major incidents, marking a decrease in the total financial damage compared to September, but a clear rise in technical diversity and attack surface expansion.
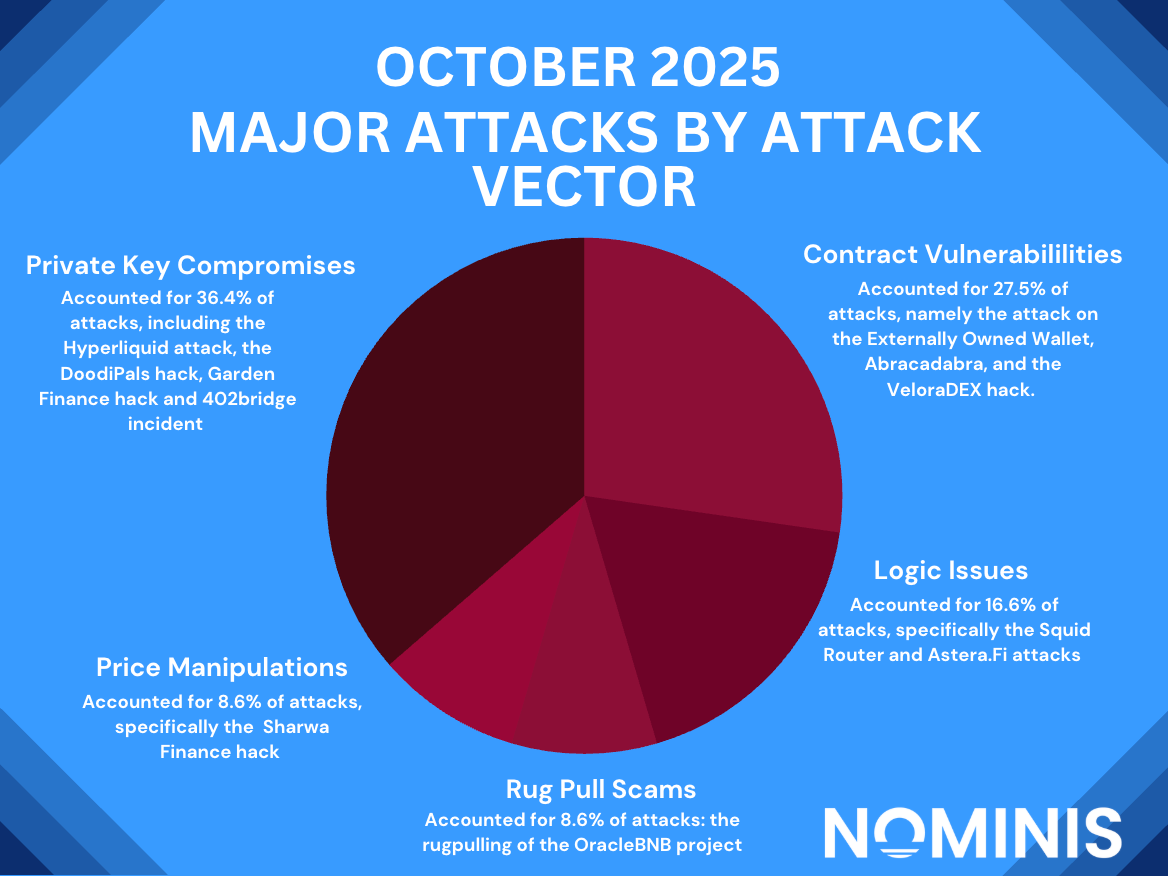
The most prominent attack vector this month was contract and protocol vulnerabilities, responsible for nearly half of all incidents, including the exploits that affected Abracadabra, Typus Finance, and AsteraFi. These cases revealed systematic weaknesses in smart contract logic, oracle design, and permission controls, issues that remain the most frequent and costly drivers of on-chain loss.
Private key compromises also continued to feature prominently, observed in incidents such as Hyperliquid, DoodiPals, 402bridge.fun and Garden Finance. Together, these attacks accounted for the majority of funds stolen in October, exceeding $32 million in cumulative losses. Once again, human and operational failures around key custody and safety proved to be a weak link.
The most prominent attack vector this month was contract and protocol vulnerabilities, responsible for nearly half of all incidents, including the exploits that affected Abracadabra, Typus Finance, and AsteraFi. These cases revealed systematic weaknesses in smart contract logic, oracle design, and permission controls, issues that remain the most frequent and costly drivers of on-chain loss.
Private key compromises also continued to feature prominently, observed in incidents such as Hyperliquid, DoodiPals, 402bridge.fun and Garden Finance. Together, these attacks accounted for the majority of funds stolen in October, exceeding $32 million in cumulative losses. Once again, human and operational failures around key custody and safety proved to be a weak link.
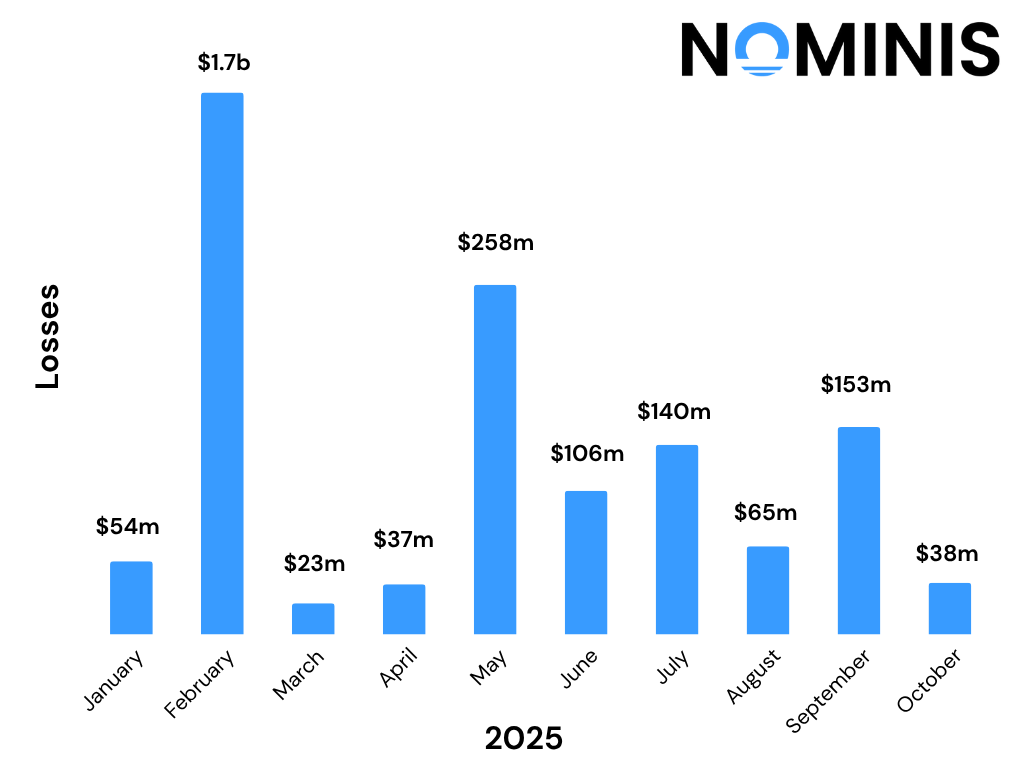
Compared to other monthly losses since January 2025, October’s losses are somewhat discrete. A full comparison of losses through 2025 due to hacks, scams and crypto crime will be released in December 2025, in our Yearly Report.
Overall, October’s incidents illustrate a maturing but increasingly fragile ecosystem: one where improving auditing and user awareness coexist alongside new technical risks, emerging standards and the persistent reality that operational missteps, rather than protocol flaws alone, continue to drive the majority of losses.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.






.png)