September 2025 proved to be another turbulent month for the crypto industry, marked by a wave of large-scale thefts, sophisticated phishing operations, and recurring infrastructure flaws. 18 major incidents collectively reshaped the risk landscape, from targeting private key compromises to advanced social engineering schemes, leveraging deepfake technology.
What stood out this month was the diversity of both the attack methods and the actors involved. While some exploits used took advantage of technical vulnerabilities in DeFi contracts, others relied on deception and human error. North Korean - linked threat groups continued to demonstrate an evolving toolkit, combining supply chain attacks with deepfake enabled phishing. Meanwhile, the maundering of illicit proceeds through Tornado Cash remained a consistent trend, underscoring the ongoing challenge of tracing funds post-exploit.
This report breaks down the major insights for this month, summarising the scope, scale and methods of the most significant crypto breaches of the month, other key events to contextualise the major attacks, and Nominis exclusive findings.
Major Attacks in September 2025
OlaXBT - 01/09/2025
Type: Multisig Compromise
On the first day of September, OlaXBT, an AI-powered market intelligence and crypto trading platform suffered a security breach, unauthorized withdrawals of approximately 32 million AIO tokens from their multisig wallets were compromised. Upon detection the OlaXBT team activated their emergency response protocols, and in a statement, announced that the vulnerability had been fully resolved. They also suggested the exploit had involved sophisticated techniques to perform the exploit, including evidence for a coordinated attack. The project team expressed that they are working with law enforcement agencies to pursue legal action and recovery efforts.
Impact: $2,000,000.00
Venus - 02/09/2025
Type: Phishing
The following day, a ‘whale’ on the Venus Protocol was tricked via a phishing scheme. They were led, via an invitation on Telegram to join a Zoom meeting, and accidentally approved a transaction giving the attacker borrowing and redeeming rights over their assets, making the attacker a ‘valid delegate’.
The attacker then used flash loans, combined with their own funds, to repay the victim’s existing debt and re-borrow against their collateral, which allowed them to siphon off funds. Rather than immediately withdrawing funds out of the protocol, the stolen assets remained within the Venus system. The Venus team responded quickly, managing to force the liquidation of the attacker’s positions by artificially inflating the BTC price, which made the attacker’s debt exceed their collateral. The Protocol was entirely restored, up and running approximately 55 minutes after the phishing approval took place.
The stolen funds were ultimately recovered, and the hacker lost about $2.7 million in the process. The whale himself, according to a post on X, believes this was the work of Lazarus Group.

Analysis of the attacker’s wallet on the Nominis Vue dashboard.
Impact: $13,000,000.00 (Fully recovered)
Bunni - 02/09/2025
Type: Protocol Logic
On the same day, Bunni, a decentralised exchange, suffered a major security breach when a precision error, or rounding error, in Bunni’s custom liquidity logic, was taken advantage of by attackers. The attacker then used flash loans and a series of 44 carefully sized withdrawals to manipulate the protocol’s pool rebalancing, and was able to withdraw more funds than allowed. Once detected, Bunni immediately paused all smart contract functions across the networks, patched the faulty rounding mechanism, and began working with law enforcement and blockchain security firms to track the stolen assets.
The team also contacted the attacker on-chain, with an offer to allow them to retain 10% of the stolen funds if the remainder is returned.
Impact: $8,400,000
Aqua - 08/09/2025
Type: Rug Pull
According to on-chain researcher and scam reporter ZachXBT on Telegram, the Solana project ‘Aqua’ has ‘likely rug-pulled 21.77K SOL’. Developers appeared to have cut off all communication, disabling replies on their official X account, which features posts hyping the launch of the AQUA token, up until the day of the alleged rugpull.
Screenshot from the official X page of Aqua , from the date of the alleged rugpull and with a post concerning the ‘unexpected’ suspension of the Aqua Medium page. Aqua had previously been widely promoted by cryptocurrency influencers, as well as teams such as Quill Audits, who congratulated them on their successful security audit, at the end of August 2025. Quill Audits then replied to this post, on the day of the exploit, clarifying their role and scope in the auditing process.
The stolen SOL were split into several transfers, routed through intermediary addresses, and then sent to various exchanges.
Impact: $4,650,000.00
SwissBorg - 08/09/2025
Type: Third-party Vulnerability
SwissBorg, a wealth management platform, experienced a sophisticated supply chain attack towards mid-September, when attackers exploited the platform’s relationship with its third-party staking partner, Kiln. The attacker compromised the Kiln API and executed a seemingly benign un-staking transaction that contained hidden malicious instructions, which granted the attacker control over almost 200,000 SOL tokens.
The attack used legitimate looking transactions to conceal authorisation instructions that transferred control of SwissBorg’s staking accounts. The attacker specifically targeted Swissborg’s SOL Earn project, meaning though the attack affected less than 1% of users, it resulted in major financial losses .The platform has committed to compensating affected users from its treasury and shut down Solana staking while the investigation continued. According to some, the Swissborg hack may be known as the ‘Bybit hack v2’, due to the exploitation of third-party infrastructure in both attacks.
Impact: $41,500,000.00
Nemo Protocol - 08/09/2025
Type: Contract Vulnerability
Nemo Protocol, a DeFi yield optimization platform built on the Sui blockchain, was hacked on the same day, with the attack occurring just before some scheduled maintenance on the platform. The Protocol has suggested that a rogue developer secretly deployed unaudited code containing critical vulnerabilities, causing the exploit. The attack exploited two vulnerabilities: a flash loan function incorrectly made public, and a query function that could modify contract state despite being designed as read-only. The deployment of the unaudited code can be traced back to January 2025, when the developer bypassed internal review processes. Despite security warnings in August 2025, the developer allegedly dismissed the severity and failed to implement fixes, ultimately enabling hackers to drain funds that were quickly moved to ETH via Wormhole CCTP, causing Nemo’s total value locked to collapse by $5 million as users withdrew assets.
Impact: $ 2,400,000
Evoq Finance - 09/09/2025
Type: Private Key Compromise
The following day, Evoq Finance, a DeFi protocol on BNB Chain, was exploited through a compromised owner account attack. The attacker gained access to the private key of the protocol’s owner account, and used it to transfer ownership to their own address. Once they controlled the owner privileges, they upgraded the proxy contract to a malicious implementation using the upgradeAndCall function, which allowed them to drain funds from both the protocol’s treasury and user token approvals. The attack was executed in three steps: transferring ownership, upgrading to a malicious contract, and draining assets.
Impact: $450,000.00
EOA Token Theft - 11/09/2025
Type: Smart contract / wallet exploit
In mid September, a significant wallet theft took place on the ETH blockchain when attackers rapidly converted stolen funds into ETH, and laundered the funds through the mixer, Tornado Cash, using sophisticated techniques. The breach was executed via smart contract exploits or flash loan attacks to the attacker’s wallet address, with stolen funds split into multiple smaller transactions across intermediate addresses, to evade detection.
Impact: $3,000,000.00

Analysis of the EOA Token thief’s wallet on the Nominis Vue Dashboard. The wallet currently holds just $0.05, but has had over $4 million dollars worth of transactions moved in and out of the wallet.
Kame Aggregator - 12/09/2025
Type: Contract Vulnerability
The following day, Kame Aggregator, a DeFi aggregator protocol, was exploited for over a million dollars, affecting 830 users, due to a critical design flaw in the swap() function. This allowed arbitrary executor calls without validation. The attacker exploited this by using a malicious Multicall contract as a proxy to steal tokens from users who had granted unlimited approvals to the router, effectively turning the router into a token theft mechanism. According to Kame’s post mortem, following immediate user alerts to revoke permissions, and on-chain negotiations offering a 20% bug bounty, the team successfully recovered almost a million of the stolen dollars from the primary exploiter, plus an additional $21,901 from white hat hackers. The incident was worsened by about 11 copycat exploiters who attacked the same vulnerability. Upon the time of publication, Kame confirmed they had refunded 96% of all affected funds.
Impact: $1,320,000.00 (partially recovered)
Shibarium - 13/09/2025
Type: Access Control
Shibarium, a blockchain bridge, suffered an enormous drain through a sophisticated consensus manipulation attack involving compromised validators. The attack began when Ryoshi Labs’ validator submitted a fraudulent checkpoint that was signed by a majority of validators who controlled about 40% of staked BONE tokens. The bad actors leveraged a flash loan to acquire millions of BONE tokens and compromised validator signing keys, giving them access and control over the protocol. Eventually, by delegating the flash-loaned tokens, they were able to completely hijack Shibarium’s consensus mechanism. Following the attack, the Shiba Inu team froze the tokens linked to the hack, and the attackers appear to have been liquidating their tokens and swapping them.
Impact: $4,100,000
Yala - 13/09/2025
Type: Security Vulnerability
The same day, Yala, a Bitcoin-focused DeFi protocol, was exploited for over $7 million when a hacker abused temporary deployment keys during an authorized bridge deployment to set up an unauthorized cross-chain bridge. According to Yala’s post mortem, the attack began on August 4th, when the hacker deployed a malicious OFTU token contract on Polygon, then on August 12th, secretly exploited a temporary local key during Yala’s Solana LayerZero OFT deployment to ultimately create a 40 day dormant backdoor. On the day of the attack, the hacker activated this backdoor and minted 120 million fake OFTU tokens on Polygon, then bridged 30 million to Solana as legitimate $YU tokens, then converted them before finally laundering the stolen through Tornado Cash. The $YU token briefly depegged to $0.20, and while the hacker returned 22.3 million of the over-minted tokens, Yala intended to destroy all illegitimate tokens and restore full liquidity by 23rd September. The protocol compensated all users who could swap $YU for USDC at 1:1 ratio.
Impact: $7,640,000.00
NewGold Protocol - 18/09/2025
Type: Flash Loan Attack
Later in the month, NewGold Protocol, a DeFi project aiming to innovate in gold-backed assets, suffered a major exploit, specifically involving its $NGP token, with the attack wiping out 88% of the token’s market value in a flash loan, price inflation exploit. This hack happened just the day after the official NGP launch on the Binance Smart Chain. The vulnerability stemmed from the protocol’s reliance on DEX pair token reserves for price calculations, creating a price oracle weakness that attackers exploited via flashloans. The attacker bypassed the protocol’s maximum purchase limit and cooldown safety checks by routing tokens through a dead address (one of only 3 whitelisted addresses exempt from restrictions). After manipulating the price oracle, and accumulating NGP tokens through multiple accounts over 6 hours before the main attack, the exploiter sold everything for 1.9 USDT, converted it to ETH, laundered it through the Across Bridge to Ethereum, before depositing funds into Tornado Cash to obscure the trail. On the incident, the NewGold Protocol shared ‘It’s cruel that lots of hackers are out there to exploit any small error’, and asked for ‘anyone who is willing to help’ assist them in finding the hacker.
Impact: $2,000,000.00
UXLINK - 22/09/2025
Type: Compromised Private Key
Several days later, Singapore- based Web3 social platform and infrastructure provider UXLINK, suffered a devastating hack after attackers exploited vulnerabilities in ‘delegateCall’ functions within the platform’s smart contracts. The hackers took control of UXLINK’s multi-signature wallet, removed existing admins’ access, and proceeded to drain stablecoins, wrapped Bitcoin, ETH and existing UXLINK tokens before minting between 1 and 2 billion additional tokens. Using 6 wallets the attacker rapidly converted stolen assets into over 6,000 ETH, and dumped about $800,000 worth of UXLINK, causing the token price to collapse dramatically. UXLINK acknowledged the breach and coordinated with exchanges like Upbit to freeze between $5-7 million in suspicious deposits, though approximately $20-30 million remains under the hackers control. The team pledged to compensate victims through a 1:1 token swap, and destroy the illegally minted supply. In an ironic twist, analysts have suggested that the hacker themself later fell victim to a phishing attack, losing 542 million UXLINK tokens. Later, posts on X confirmed that the exploiter had begun to swap remaining funds and deposited them into Tornado Cash.
Impact: $28,000,000.00 ($17,000,000 through the minting of additional coins)
Seedify - 23/09/2025
Type: Compromised Private Key
Later in September, Seedify, a Web3 Incubator and Launchpad, was hacked by a North Korean state-affiliated group (DPRK), who gained access to one of the developer’s private keys and exploited a previously audited bridge contract to mint unauthorised SFUND tokens on Avalanche. The attackers bridge these fraudulent tokens to Ethereum, Arbitrum and Base, drained available liquidity pools, then moved the maximum amount to BNBChain where they sold them, before the breach was contained. Seedify immediately coordinated with centralized exchanges to halt trading, blacklisted the attacker’s addresses, revoked compromised permissions, and paused all cross-chain bridges confirming that core contracts, user wallets and the underlying protocol remained unaffected. In their statement on X, the company committed to reviewing all infrastructure security with auditors.
Impact: $1,800,000.00
GriffinAI - 24/09/2025
Type: Compromised Private Key
Towards the end of the month, GriffinAI, a DeFi project with the token GAIN, suffered a devastating exploit when attackers created 5 billion unauthorized tokens, which far exceeded the intended 1 billion token cap. The attackers exploited a misconfigured LayerZero node on Ethereum which allowed them to mint fake tokens without authorization, and bridge them to BSC, where they quickly sold 98% of the tokens through PancakeSwap and Private deals. The attackers then laundered the proceeds through Tornado Cash and deBridge to Ethereum and Arbitrum. The exploit caused GAIN’s price to crash 87%, while the circulating supply exploded from 235 million, to 5.235 billion tokens, heavily diluting existing holders. Major exchanges including Binance Alpha and KuCoin immediately suspended GAIN trading to prevent further damage, while updates about the attack from the GriffinAI X account suggested the breach may have been due to a compromised private key.
Impact: $36,000,000.00
HyperVault - 26/09/2025
Type: Rugpull
Following alerts of suspicious activity on X, an alleged rugpull has taken place involving the DeFi platform HyperVault, with over $3.5 million in abnormal outflows detected. The funds were bridged from Hyperliquid to Ethereum, swapped into ETH, and then deposited into Tornado Cash. Adding to the suspicious, HyperVault’s X account has been deleted, and its official website is inaccessible. Collectively, this suspicious behaviour suggests a classic rug pull scenario, where project operators withdraw user funds and disappear, leaving investors with significant losses.
X account of Hypervault, which no longer exists.
Impact: $3,600,000
HyperDrive - 27/09/2025
Type: Smart Contract Vulnerability
The following day, a separate project that also runs on Hyperliquid, HyperDrive, suffered an exploit after detecting suspicious activity in its Primary and Treasury USDT0 markets. According to an in-depth explainer shared on X, the team immediately paused all markets and launched an investigation with auditors. A security patch was developed, reviewed, and deployed within hours. The team also confirmed that the impacted transactions were ‘limited to the Primary and Treasury markets’ only, and that the malicious activity was traced to an ‘exploit affecting users’ collateralized positions.’ Finally, they confirmed that the affected users had been compensated for, and a postmortem would be released in future.
Impact: $782,000
dTRINITY - 28/09/2025
Type: Contract Vulnerability
The final significant hack of the month saw attackers exploit dLEND’s swap adapter to misus prior token approvals and siphon collateral. dLEND is a decentralised lending protocol which is part of the dTRINITY ecosystem. Losses were limited to three internal team wallets, which user funds remained safe and the vulnerable feature was quickly disabled.
Impact: $56,000
Significant Events in September
NPM Supply Chain Attack
On September 9th, attackers phished the owner of the popular NPM ‘qix’ account, then uploaded backdoored packages. The malware swapped out wallet addresses for attacker-controlled ones and even intercepted Ethereum and Solana transactions. More information about the attack is available in a dedicated article here.
North Korean Telegram Scam
The same day, THORChain co-founder John-Paul ‘JP’ Thorbjornsen suffered a $1.2-1.35 million hack after falling victim to a sophisticated social engineering hack. The attackers used a hacked Telegram Account and a convincing deepfake video call, which encouraged him to run malicious code. From there, the attackers obtained his private keys. This case mirrors the events of Whale on Venus mentioned earlier in this report, demonstrating a potential new hacking method used by North Korean malicious actors.
$3 million DeFi Exploit
A DeFi protocol was drained of about $3 million in USDC through a smart contract exploit, likely involving flash loans. The attackers quickly converted the funds to ETH and obscured the trail through Tornado Cash.
$6 million Whale Phishing Theft
A crypto whale lost over $6 million in staked ETH and wrapped BTC after signing a malicious ‘permit’ signature. The approval let attackers use transferFrom to drain tokens without any visible gas transaction, making the phishing highly deceptive.
Discord Server hacks
KiloEx, a DEX specialising in perpetual futures trading for crypto assets, suffered a hijacking by scammers after their Discord invite link expired. The hackers stole assets from those who clicked the link and interacted with phishing signatures. The malicious link remained accessible through data aggregator and analysis platform Coingecko, and through previous KiloEx posts on X. The same took place to Verisense Network , who also had their expired vanity URL claimed.
Nominis Intelligence Team: Exclusive findings
In September alone, the Nominis Intelligence Team saw the unveiling, and flagging, of approximately $4 billion worth of illicit crypto assets from a variety of sources, from sanctioned entities to large scale laundering networks. This progresses our tireless efforts to provide clients with proactive, actionable intelligence, enabling them to detect, assess and mitigate high-risk crypto activity before it impacts their operations or reputation.
Additionally, Nominis reached an important milestone: our database has now exceeded one billion clustered blockchain addresses. Clustering allows us to group individual wallets into identifiable entities, such as exchanges, illicit groups, or laundering operations.
For our clients, we will be able to provide:
- faster, more accurate detection of high-risk activity, and
- Richer investigative context when analysing transactions.
With broader coverage, Nominis now identifies suspicious interactions even earlier, with a reduction in false positives, providing a more reliable risk scoring for your Know Your Transaction workflows.
At the investigative level, larger clusters allow us to trace complex laundering paths, and connect on-chain behaviour with off chain intelligence.
Insights for September 2025
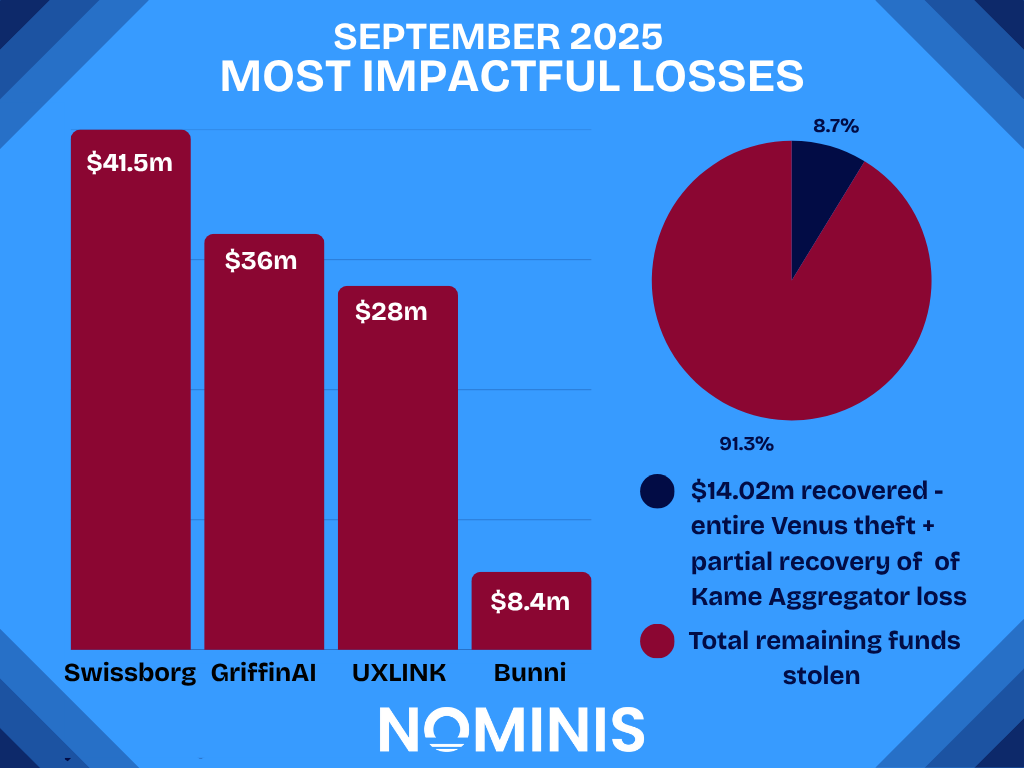
By the end of September 2025, the crypto ecosystem had recorded over $160 million in confirmed losses from 18 major incidents, underscoring persistent weaknesses across multiple attack vectors.
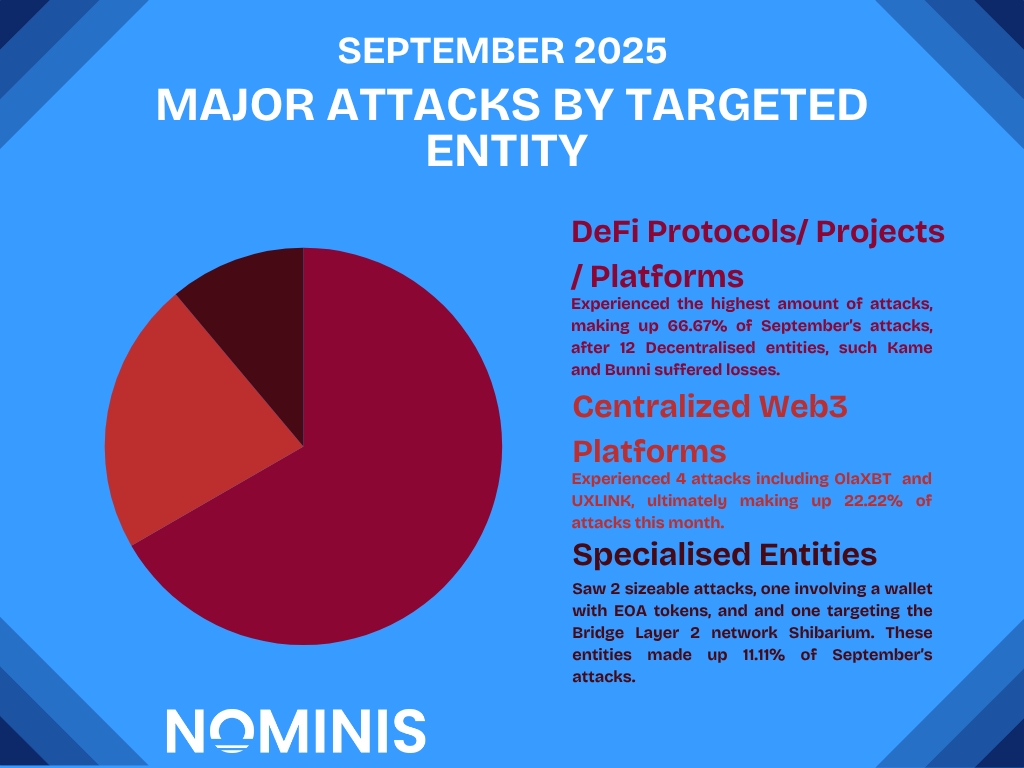
The most common method was the compromise of private keys, responsible for five high-profile cases including UXLINK, GriffinAI, and Seedify, which resulted in a total of $65.8 million in losses.
Contract and protocol vulnerabilities also featured prominently, with the Bunni and Hyperdrive exploits amounting to a total of $9.182 million in losses.
The single largest loss stemmed from a third-party supply chain breach, when Swissborg suffered a $41.5 million theft.
September’s attacks revealed some alarming trends. The prevalence of unauthorized token minting became apparent, seen in four attacks, where projects like UXLINK, GriffinAI, Seedift and Yala saw billions of tokens minted well beyond supply caps.
Another emerging pattern points to growing North Korean involvement, with confirmed or suspected ties in several cases. Seedify and the THORChain founder hack, where attackers reportedly used deepfake video calls to phish project leaders, demonstrates a new method undertaken by the DPRK to steal funds.
In terms of money laundering and trail obfuscation, Tornado Cash remains the dominant tool, used by the malicious actors in at least six of the major attacks in September, to confuse the trace of funds.
Recovery of stolen assets remains rare. While the victim of the Venus attack managed a full $13 million dollar clawback, the Kame case retrieved just over $1 million of the stolen assets.
Meanwhile, the use of bounty offers as a recovery tactic was mixed. Out of the month’s largest exploits, only a few teams offered attackers a share of the stolen funds in exchange for their return. Bunni reached out on-chain, offering a 10% bounty offer, while Kame Aggregator proposed a 20% return-for-safety agreement, which led to the partial recovery. In contrast, other incidents such as Swissborg’s major $40+million breach made no public bounty offers, instead focusing on law enforcement coordination, exchange freezes, and victim compensation. The only incident that retrieved the stolen funds in full, the Venus recovery, was done via the protocol’s emergency governance powers to seize the hacker’s position. This pattern suggests that while bounty-based negotiations are becoming an established option, they are still far from standard practice.
Overall, September’s events reflect the evolving sophistication of threat actors, recurring structural weaknesses, and the growing convergence of social engineering with on-chain exploits.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.






.png)