November 2025 was marked by a surge of diverse crypto related incidents, involving a variety of different vectors, and amounting to over four times the number of losses compared to October 2025.
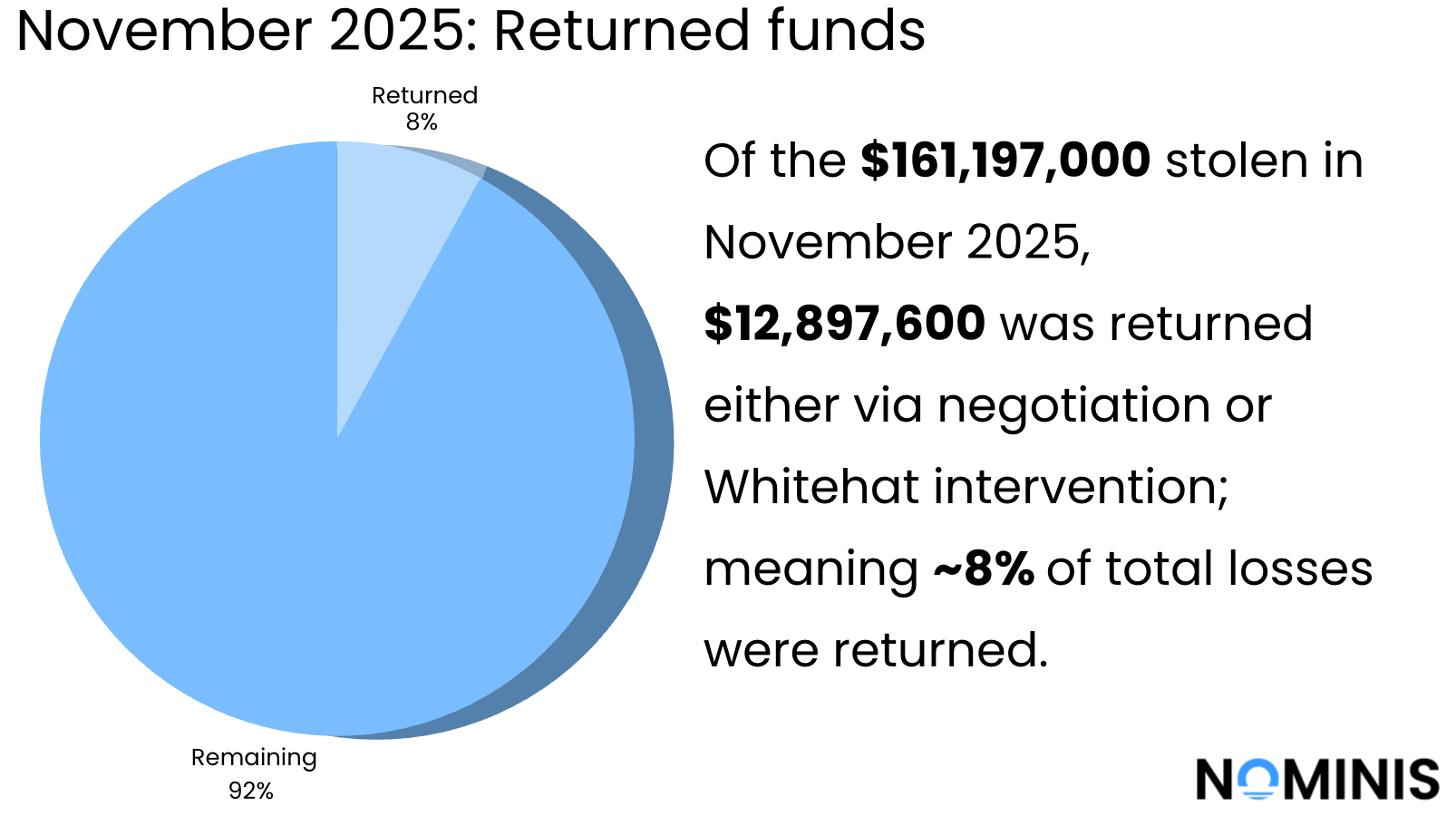
This report provides a consolidated overview of the major crypto security incidents recorded this month, highlighting the total value lost, the most common attack patterns, and the proportion of funds ultimately recovered. Across all cases reviewed from November 2025, attackers stole a total of over $161million dollars, with approximately $12 million dollars returned through rapid response efforts, whitehat hackers, or on-chain freezes.
By examining exploits across protocols, exchanges and emerging projects, this report highlights where vulnerabilities are concentrated, how attacker tactics are evolving, and how the crypto ecosystem must evolve in parallel.
Major Attacks in November 2025
Berachain and Balancer - 03/11/2025
Type: Contract Vulnerability
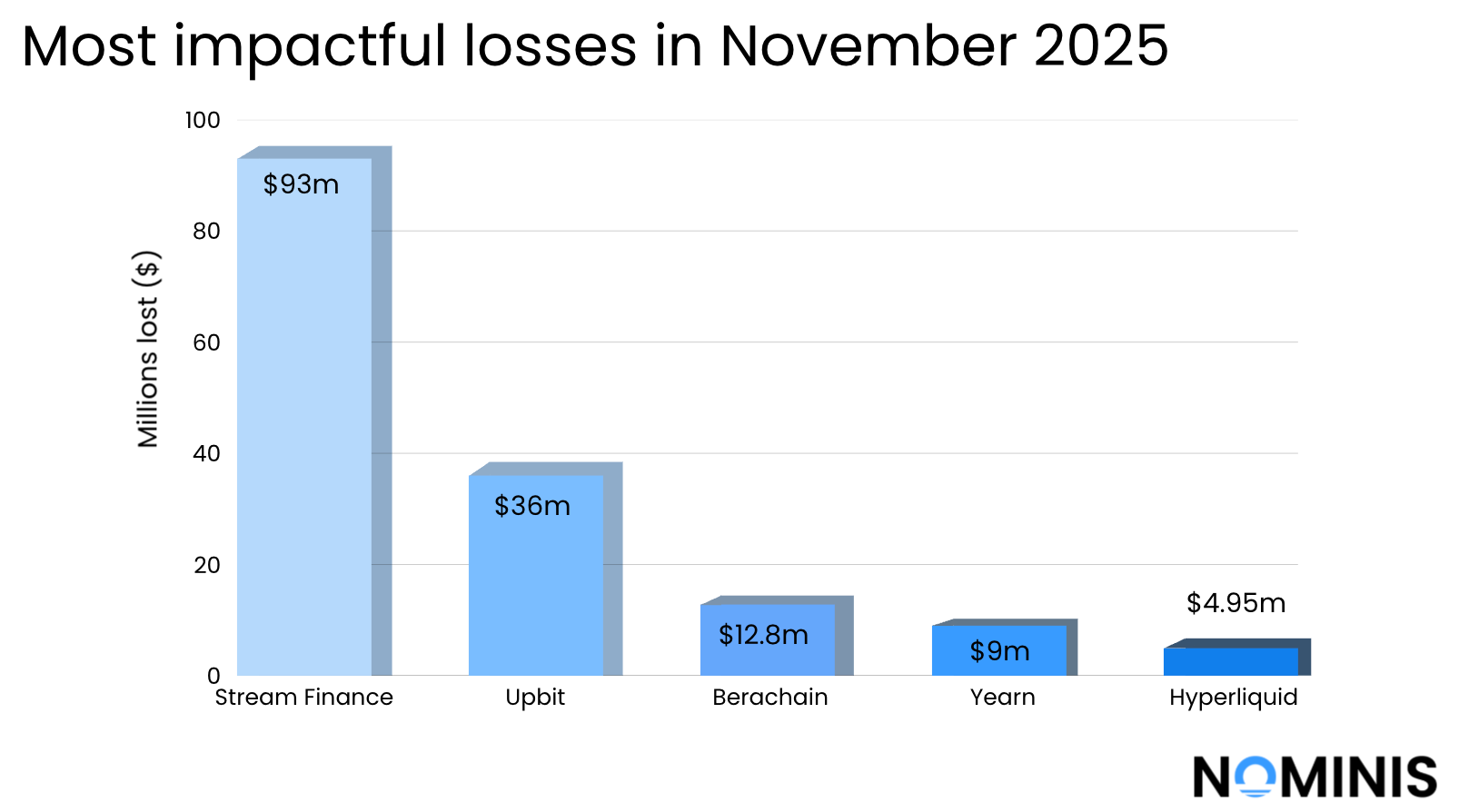
Berachain, a Layer 1 blockchain network built using the Cosmos SDK, was forced to execute an emergency hard fork, after a Balancer-related vulnerability in its BEX exchange led to a $128 million cross-chain exploit, including a significant drainage from its own ENA / HONEY pool. The breach stemmed from a Balancer V2 access-control failure that allowed the attacker to mint fake fees and withdraw real assets, prompting Blockchain to halt the network, patch the flaw, and block the stolen tokens’ movement. A self-described white-hat MEV operator who carried out the BEX portion of the exploit later agreed to return the funds, which Berachain confirmed were fully recovered, allowing the chain to resume operations as infrastructure partners updated their systems.
Impact: 12,800,000 (returned)
Moonwell - 04/11/2025
Type: Oracle Attack
Early in November, an attacker exploited Moonwell’s lending contract by abusing a faulty oracle price feed for wstETH / wrsETH. The oracle erroneously reported the collateral value as ~$5.8 million. By flash-loaning merely ~0.02 wrsETH and depositing it, the attacker was able to repeatedly borrow over 20 wstETH. Repeating the process across several transactions, the attacker walked away with about 295 ETH in profit before the error was caught.
The below screenshot from the Nominis Vue platform demonstrates some of the stolen funds, ~$896,000, that moved through this wallet, owned by the attacker. This analysis suggests that this particular wallet was involved in siphoning the majority of the stolen million dollars.
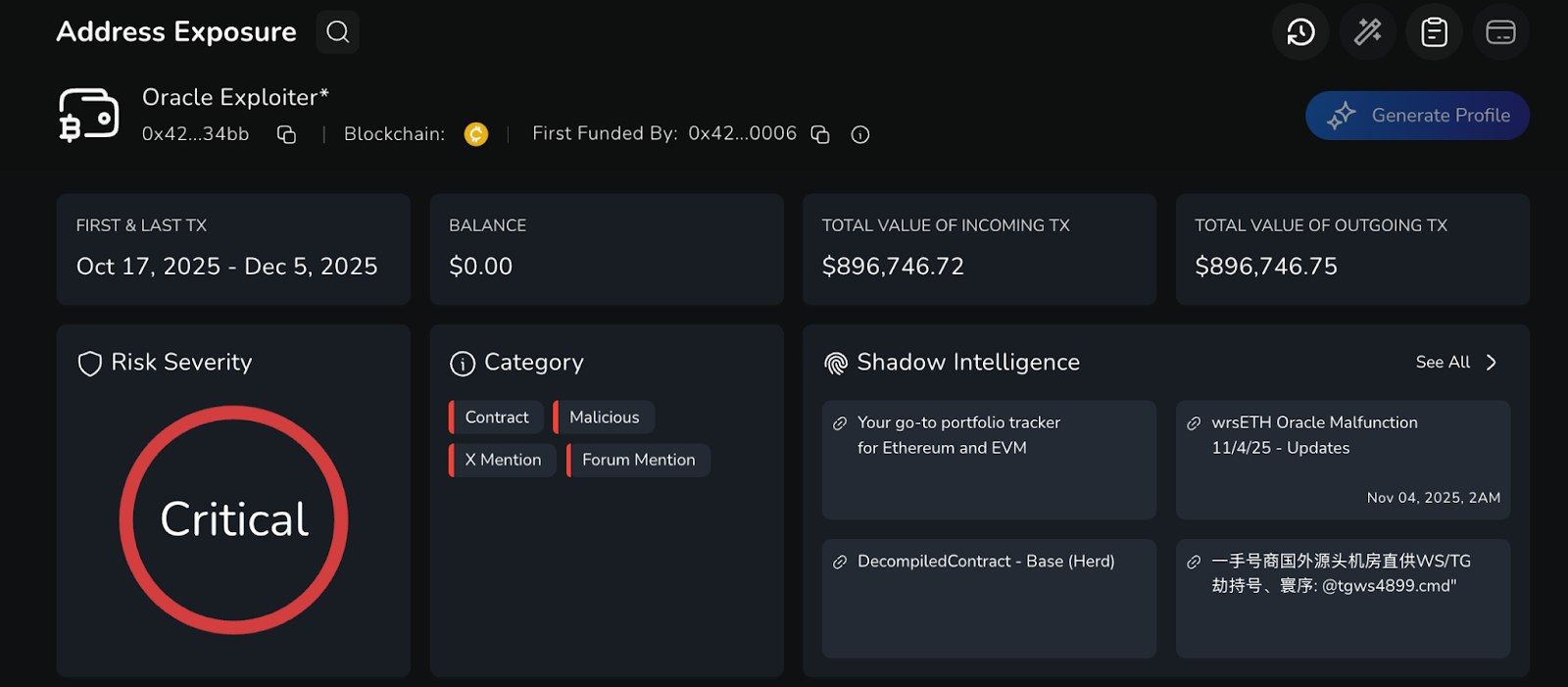
Impact: $1,000,000.00
Stream Finance - 04/11/2025
Type: Fund Mismanagement
On the same day, Stream Finance announced that an external fund manager lost about $93 million of the protocols assets, forcing Stream to halt deposits and withdrawals and triggering a collapse of its synthetic stablecoin, xUSD, which fell over 70%. The root cause was Stream’s opaque structure, relying on an off-chain fund manager and aggressive recursive leverage loops rather than being backed by on-chain reserves. xUSD and its related synthetic assets such as xBTC and XETH are widely used as collateral across DeFI, so this de-pegging caused cascading damage throughout the ecosystem. Once confidence was lost, the system entered a death spiral - illiquid collateral, frozen redemptions, panic selling, and widespread protocol-level losses across the DeFi landscape.
Impact: $93,000,000.00
Dimo - 07/11/2025
Type: Private Key Compromise
Several days later, a hacker gained access to a compromised developer key, and used it to withdraw 30 million DIMO tokens, which amounted to about 3% of the total supply, from a Wormhole bridge contract.
The breach affected only the bridge deployer, and did not compromise DIMO’s core network, user assets, or the integrity of the token itself. In response, the team immediately revoked the affected keys, audited all relevant smart contracts to confirm no further vulnerabilities, and began working with ecosystem partners and law enforcement to further investigate the incident.
Impact: $40,000.00
Impermax V3 - 11/11/2025
Type: Protocol Logic
Impermax suffered an exploit in its cbBTC lending vault on Base, that drained about 5.39 cbBTC after an attacker abused a routing error vulnerability in the protocol’s liquidation logic. By repeatedly creating tiny positions in a cbBTC-tBTC pair with almost no liquidity, the attacker was able to push the borrowable contract’s totalBalance toward zero, artificially collapse the exchange rate, and then mint an exponentially growing balance of cbBTC borrowable tokens for themselves. Once the totalBalance hit zero, the contract entered a malicious state, and all the deposits were redirected to the attacker’s address, who then forced the lending vault to deposit funds into this compromised borrowable contract and withdrew the vault’s assets. As a response, the impermax team disabled vault connections, added liquidity to low-balance borrowables, and recommended all users withdraw funds as a precaution.
Impact: $380,000.00
DRLVaultV3 - 11/11/2025
Type: Access Control Issue
An attacker exploited a vulnerability in the DRLVaultV3 contract on Ethereum, where the swap function relied on the Uniswap spot price without any meaningful slippage protection. This allowed a known whitehat hacker, c0ffe.babe.eth to execute the transaction and capture roughly $100,000 in USDC. The incident was related to the protocol’s reliance on an unprotected spot price feed, which made the swap mechanism easy to manipulate. Although the frontrunner successfully executed the exploit, they later reportedly returned a significant portion of the funds, mitigating most of the financial impact.
Impact: $100,000.00 ($97,600 returned)
Hyperliquid - 13/11/2025
Type: Price Manipulation
Hyperliquid, a decentralized exchange, suffered an exploit when its Hyperliquidity Provider (HLP) was manipulated by an attacker, using 19 wallets and $3 million to open 5x leveraged long positions worth $20-30 million on POPCAT. They initially propped up the price with buy walls, and then abruptly removed them, triggering a flash crash that wiped out their collateral. All 19 accounts were liquidated, and with the liquidity drained, HLP absorbed the loss, leaving almost $5 million in bad debt.
Impact: $4,950,000.00
WLFI - 20/11/2025
Type: Phishing Attack & Private Key Leakage
A week later, World Liberty Financial, a DeFi platform / crypto company backed by the Trump family, experienced several wallet compromises before its launch. The compromises took place due to phishing attacks and leaked seed phrases. WLFI made efforts to clarify that neither the platform or contract had any vulnerabilities. To protect users, the team froze affected wallets and implemented new contract logic allowing users to reclaim assets to verified wallets after completing Know HYour Customer. Unverified wallets remain frozen. To mitigate effects, WLFI burned 166.67 million tokens (~$22 million) from a compromised address, and reissued the same amount to a secure wallet. The team emphasized that safety of funds were prioritised over speed, and reallocation will proceed for users who have completed the verification process.
Impact: Unconfirmed
GANA Payment - 20/11/2025
Type: Contract exploit
Later in November, the BSC-based payment project GANA Payment was exploited for over $3 million after an attacker gained control of a privileged contract key. The attacker manipulated the platform's reward-rate parameters, then called the ‘unstake’ function to drain liquidity, effectively minting inflated reward tokens and extracting funds. Once the funds were stolen, the attacker moved the proceeds through bridging and mixing, some mixed on BNB chain, and the remainder bridged to Ethereum. In response to the hack, GANA Payment announced a project reboot, with efforts planned to remap users’ assets and permissions. However, the exploit caused a collapse in confidence with the project’s token lost around 90% of its value.
Impact: $3,100,000.00
DexMaxAI- 20/11/2025
Type: Phishing Attack
On November 20, GoPlus reported that the DMT (DexMaxAI) airdrop posed serious security risks. Users were tricked into authorizing additional tokens, likely via phishing links, during the claim process, which allowed attackers to steal assets from over a thousand wallets, with cross-chain transfers exceeding $130,000. Most of the stolen funds were moved to Ethereum and some were sent to the HitBTC exchange, while a portion remains on-chain. The project’s official website and Twitter are now offline. GoPlus advised all users who claimed the $DMT airdrop to revoke related token approvals, and transfer assets to secure wallets to prevent further losses.
Impact: $130,000.00
Port3 Network - 23/11/2025
Type: Cross-Chain Bridge Vulnerability
Port3 network, a blockchain-native data infrastructure protocol, experienced a major exploit after an attacker abused a flaw in its cross-chain bridge, the BridgeIn mechanism, the mint roughly a billion unauthorized PORT3 tokens. Immediately after mining, the attacker dumped about 162.75 million tokens for roughly 199.5 BNB, causing a massive sell-off and triggered an approximately 80% crash in PORT3’s price.
In response, Port3 pulled all on-chain liquidity, halted trading, and later migrated to a new token contract on BNB Chain to restore integrity. The attacker reportedly burned the remaining ~837.25 million minted tokens instead of dumping them, which, along with the dump and liquidity removal, prevented further damage. The exploit caused severe market disruption, wiping out most of PORT3’s market value in a matter of minutes and triggering a crisis in confidence and liquidity.
Impact: $166,000.00
Agentic FoF - 23/11/2025
Type: Security Breach
On the same day, asisOS reported that its Agentic FoF vault was compromised in a security breach, resulting in an estimated loss of over half a million dollars. In response, the team froze all vaults, and suspected withdrawals specifically for the Agentic FoF while an internal investigation was conducted. In relation to the announcement of the compromise, BasisOS shared that an internal member of their team had acted maliciously and stolen the funds.
Impact: $531,000.00
Upbit - 27/11/2025
Type: Infrastructure (Security mismanagement)
Upbit, South Korea’s largest crypto exchange, suffered a major breach towards the end of November when a Solana-network hot wallet was compromised and roughly $36 million in assets were stolen. The incident apparently stemmed from a critical flaw in Upbit’s digital-signature infrastructure which may have allowed attackers to derive private keys directly from transaction data and take full control of the wallet.
The stolen funds included SOL, USDC, BONK and other Solana-based tokens. Once abnormal withdrawals were detected, Upbit halted all deposits and withdrawals, transferring remaining funds to cold storage, and froze assets where possible.
Investigators suspect that the attack was carried out by a sophisticated group, with the North Korea-linked Lazarus Group considered a likely culprit. Upbit has pledged to fully reimburse users from its own reserves, meaning customers will not bear any losses, while the exchange absorbs the financial impact.
Impact: $36,000,000.00
Below are examples of two of Lazarus Groups’ attacking wallets, who siphoned some of the stolen funds from Upbit. Nominis’ risk screening platform demonstrates that in both wallets, some funds remain, though millions of dollars have moved through each of them.
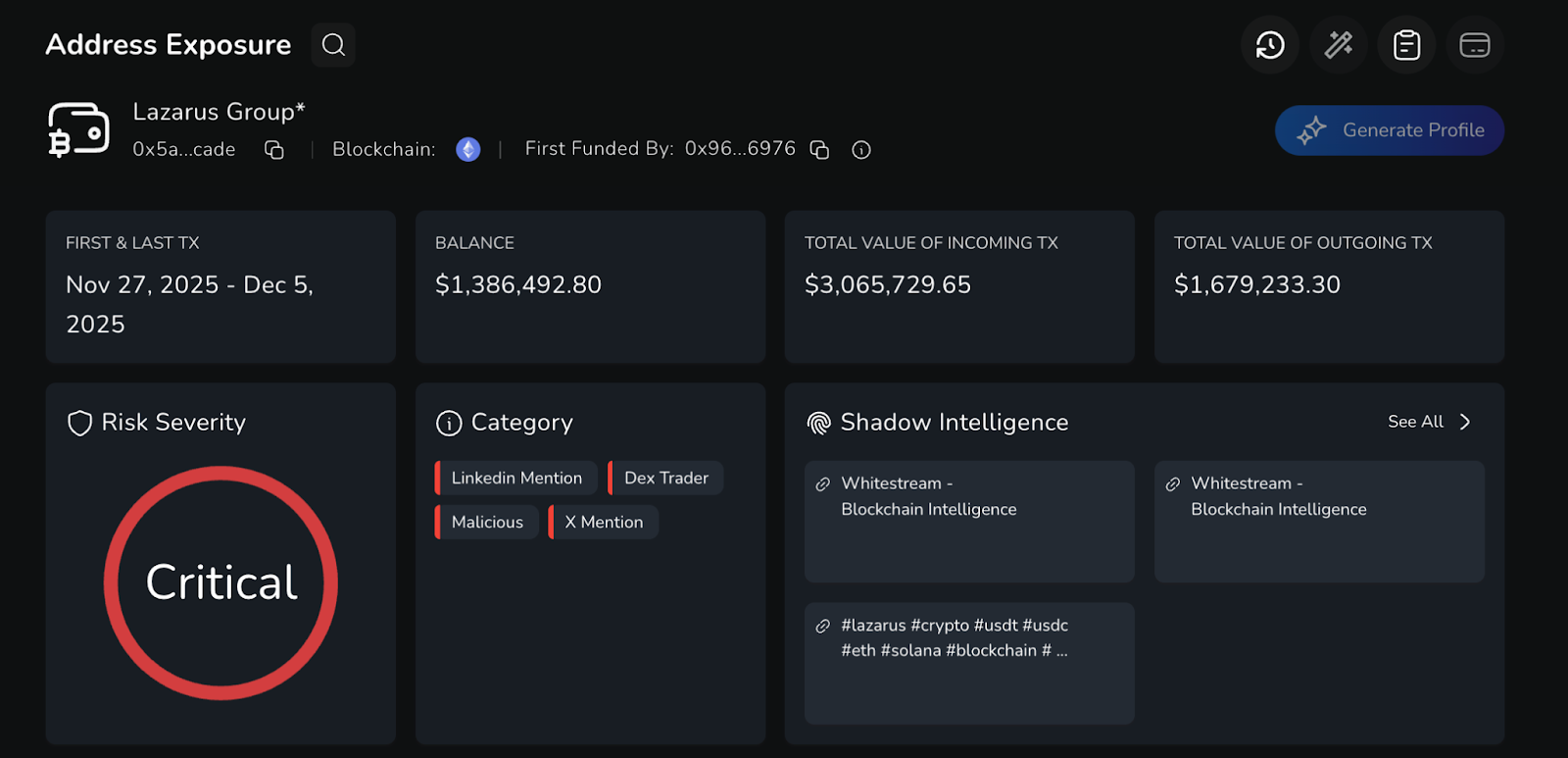
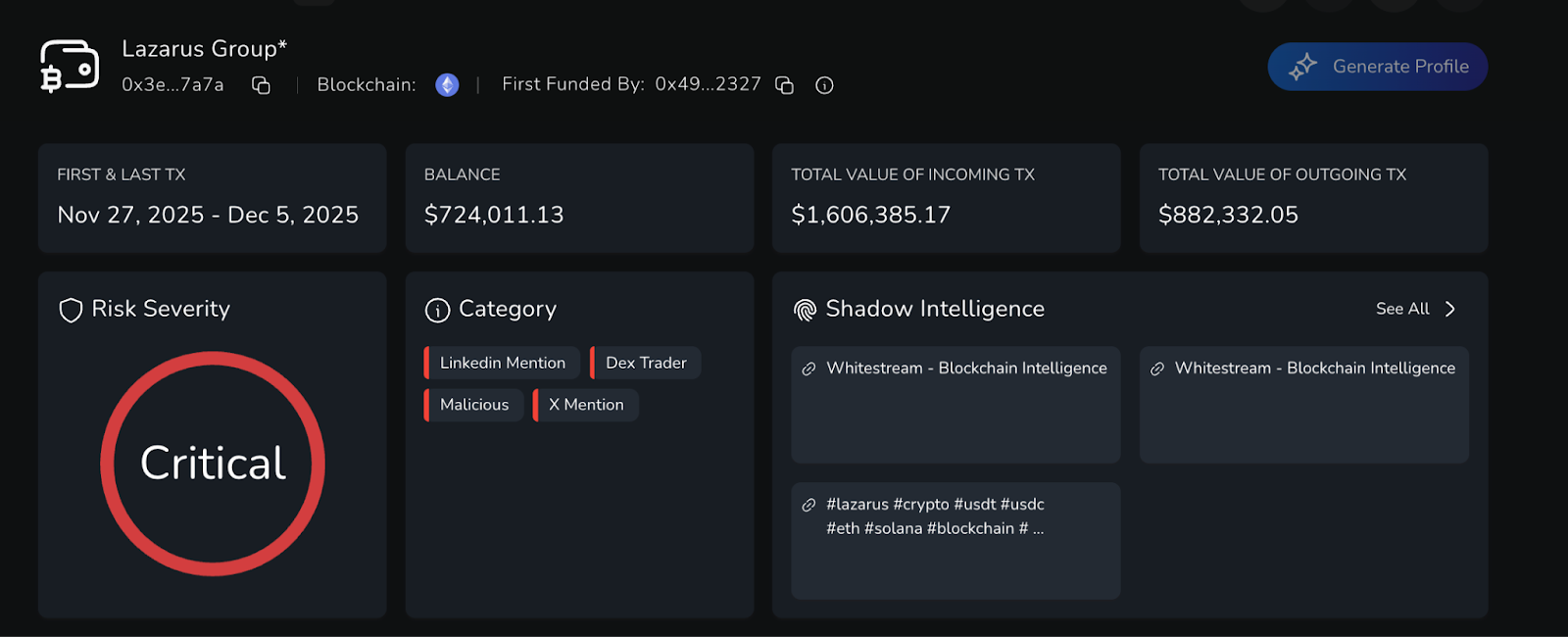
Yearn Finance - 30/11/2025
Type: Protocol Logic
Towards the end of November, Yearn was hit with a severe exploit, targeting a legacy ‘yETH’ pool. The attacker exploited a flaw in the pool’s contract logic to mint an unlimited amount of fake tokens, then exchanged them for real assets. Just under half of the stolen funds weer immediately funneled through a mixing service to obfuscate the flow of funds, while the remainder stayed in attacker controlled wallets or liquid-staking derivative positions. Yearn emphasized that the exploit was confined to the legacy yETH contract, and its main V2/V3 vaults were unaffected. Autonomous exploit code was deployed and then self-desctructed to obscure traces of the attack.
Impact: $9,000,000.00
Significant events in November 2025:
Polymarket scam steals over $500k
Over half a million dollars have been stolen through a sophisticated scam spreading in the comments section of Polymarket, where attackers pose as legitimate users promoting ‘Polymarket private markets’ with supposedly better odds. Scammers buy both YES and NO shares to appear in the ‘holders’ filter, then post an obfuscated link to a fake polymarket branded site. Victims were prompted to log in and verify activity, which tricks them into copying a malicious terminal command. The command would silently download and execute a hidden script that steals system data, logs activity and sends it back to the attackers, allowing them to drain wallets and accounts.
Community members are calling for stronger comment moderation or downvoting to prevent these scams, as Polymarket’s current warning system has proven insufficient.
New Lawsuit accuses Binance of enabling Terror Financing
November 2025 saw the families of victims of the October 7th Hamas attack file a billion dollar lawsuit accusing Binance and its founder Changpeng Zhao, of enabling crypto transfers for Hamas and other terror groups. The suit alleges that Binance operated a ‘haven for illicit finance’, deliberately weakening compliance controls, ignoring red flags, and allowing terror-linked wallets to transact freely, even after regulators penalised the exchange for money-laundering failures.
According to the lawsuit, tens of millions of dollars continued to flow through Binance to Hamas both before and after the October 7th attack. While Binance denies knowingly facilitating terrorism, the case marks one of the most significant attempts yet to hold a global crypto exchange legally responsible for alleged terror financing.
Nominis Unique Findings
At Nominis, our intelligence capabilities give us a front row view into the real nature of illicit crypto activity, often challenging mainstream assumptions. Last month, our research team published a widely shared investigation, ‘Crypto Terror Financing: Misconceptions vs Reality’, which debunks the commonly held belief that terror financing through crypto is exaggerated. Our analysis demonstrates that terror groups largely utilise digital assets, more significantly believed than other leading blockchain firms. This report reinforced the importance of data driven analysis, in shaping industry perception of the role of crypto in terror financing.
Beyond thorough written analysis, the Nominis Intelligence Unit continued to uncover high-impact risk across the ecosystem daily. In November alone, our systems detected over $500 million in illicit crypto flows, spanning ransomware, darknet market activity, sanctions exposure, and high risk laundering patterns.
The Unit also identified and mapped over 40 illicit OTC brokers operating across the Middle East, many with direct financial exposure to designated terrorist organisations, and $70 million in suspicious flows.
These findings highlight Nominis’ efforts to provide unparalleled visibility into hidden risks, empower compliance teams with intelligence, and prevent high-risk funds from using legitimate platforms as conduits.
Concluding Insights:
November 2025 was one of the most damaging months for the crypto ecosystem in recent memory, with a combined total of approximately $161 million in confirmed stolen or compromised assets across exchanges, DeFi protocols, cross-chain bridges, and token infrastructures.
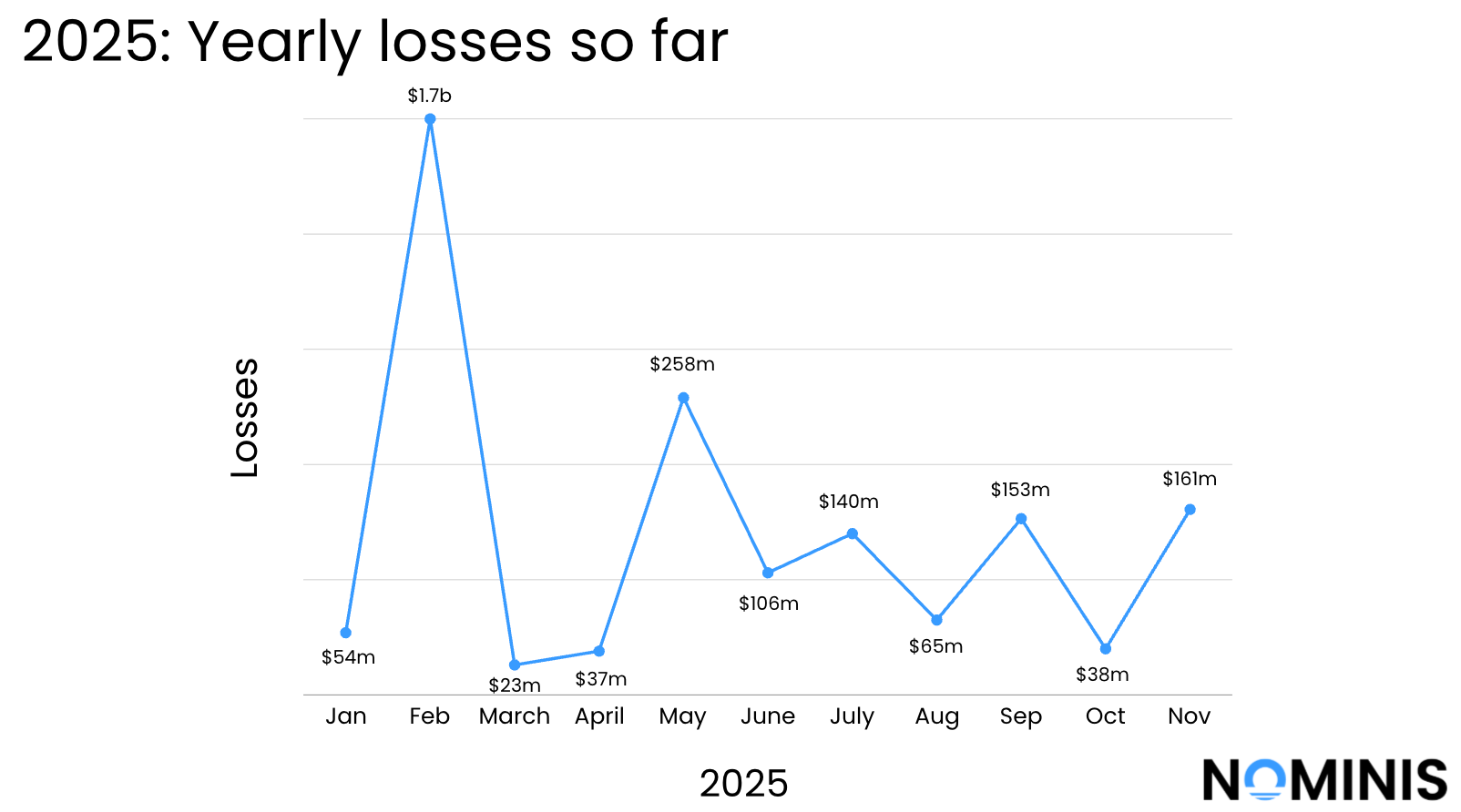
The incidents spanned nearly every attack vector in the industry, but the most frequent patterns were the logic flaws and contract exploits, which together accounted for the majority of losses. Oracle manipulation, bridge vulnerabilities, key compromises, fund mismanagement and large-scale phishing campaigns added to the month’s volatility, demonstrating how both technical and operational weaknesses continue to create systemic risk.
As usual, recovery rates remained low. Only a couple of cases saw meaningful return of funds, notably the Berachain/ Balancer exploit, where $12.8 million was recovered in full, and the DLRVaultV3 incident, where over ninety-seven thousand of the one hundred thousand dollars were returned. Outside of these outliers, the overwhelming majority of stolen assets were rapidly laundered, bridged, mixed or otherwise dispersed across chains, underscoring how difficult post-incident remediation has become.
November’s events also highlighted broader challenges facing the industry:
- Centralised infrastructure failures, as seen with Upbit’s attack
- Misrepresentation and opaque fund management, as seen with Stream Finance’s loss
- And the increasing intersection of crypto with geopolitical risk, demonstrated by the involved of North Korean backed hacking group Lazarus Group’s involvement in the Upbit attack
Nominis internal intelligence findings continue to demonstrate how much illicit activity remains under-detected by the industry at large. In November alone, Nominis systems identified more than $500 million in illicit crypto flows, and uncovered over 40 illicit OTC brokers across the Middle East, tied to designated terror organisations. Together with our publications, we continue to challenge a prevailing under-estimation of terrorist exploitation of crypto and digital assets.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.






.png)