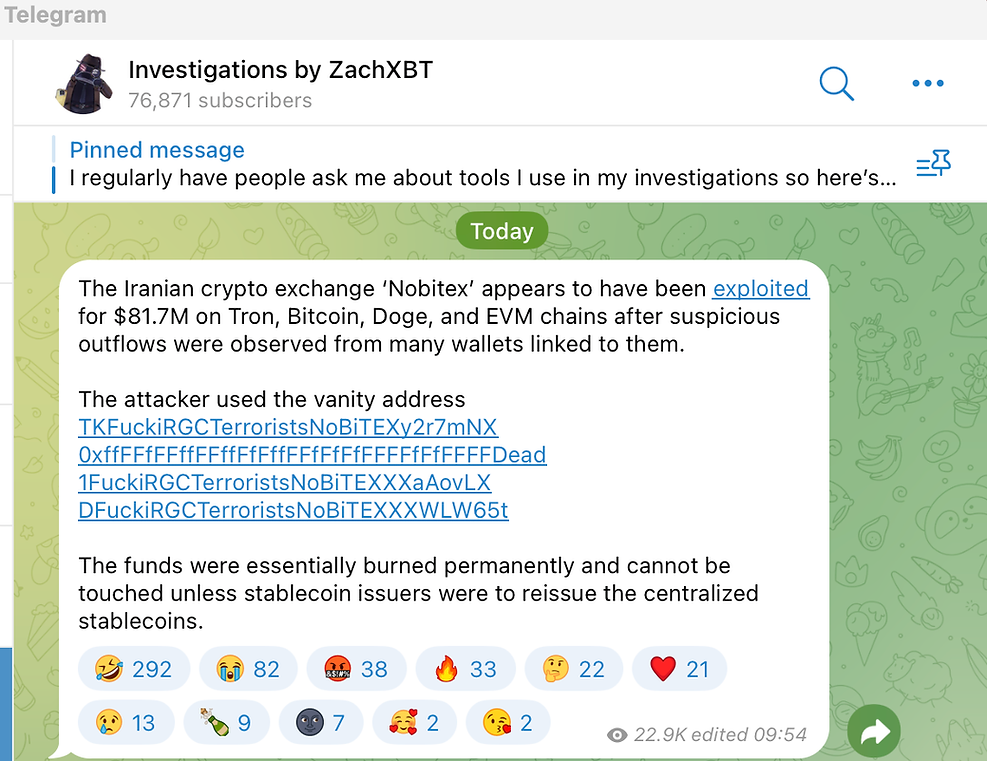
On June 18, Iran’s largest Crypto Exchange, Nobitex, suffered a major cyberattack that has since sent shockwaves through the blockchain ecosystem. The breach, which hacktivist group ‘Predatory Sparrow’ (Gonjeshke Darande) has claimed responsibility for, saw the unauthorized outflow of almost $90 million, mostly in USDT on Tron, from Nobitex’s Hot Wallets. The outflow was recognised by transaction monitoring platform Nominis Vue, and corroborates with the some of the research of hack investigator ZackXBT via Telegram, and brings new wallets to light, discovered exclusively by Nominis Vue.
What happened?
Blockchain analysis indicates that hackers rerouted funds via deposit addresses and key out wallets, then transferred the assets to vanity wallets, including:
- TRON - TKFuckiRGCTerroristsNoBiTEXy2r7mNX - $49M
- ETH - 0xffFFfFFffFFffFfFffFFfFfFfFFFFfFfFFFFDead - $24m
- BTC - 1FuckiRGCTerroristsNoBiTEXXXaAovLX - ~$2m
- DOGE - DFuckiRGCTerroristsNoBiTEXXXWLW65t - $6.6m
And
- TON - UQABFuckIRGCTerroristsNOBITEX1111111111111111_jT - $6m, a wallet exclusively discovered by Nominis Vue.
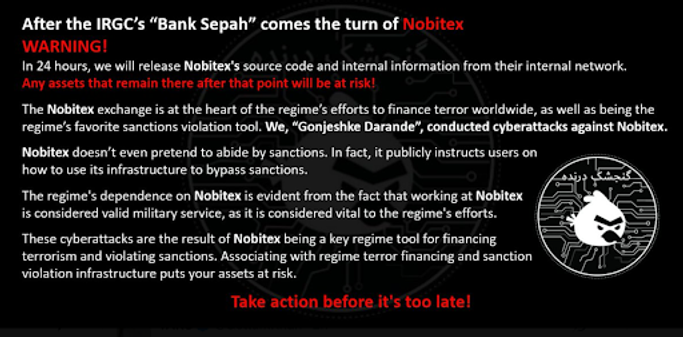
This exploit was not just a typical hack. It appears that this hack had political goals. The attack actually followed an earlier campaign, also claimed by Predatory Sparrow, targeting Bank Sepah, a financial arm of Iran’s Islamic Revolutionary Guard Corps (IRGC). The group has publicly claimed responsibility for both of these incidents declaring that Nobitex is a ‘regime tool’ for sanction evasion and terror financing.
On 18 June, via X, Predatory Arrow issued a 24 hour ultimatum, asking users to withdraw funds or risk further exposure and asset loss. The group claim to have access to Nobitex’s source code and internal communications, and threaten to release them.
The same day, Nobitex shared an official statement on X, confirming the breach and that it has affected ‘a portion of [their] hot wallet and internal communication systems, but emphasized that cold wallet remain secure, that affected funds will be fully reimbursed, and that their services are suspended.
As a result of the events unfolding, Nominis CEO Snir Levi has reported that the Nominis Vue transaction monitoring platform has flagged a 5x spike in withdrawals from Nobitex, in the 48 hours leading up to the strike. Iranian users of Nobitex, who fear collapse or contagion, began moving USDT to private wallets and offshore exchanges, like CoinEx and LBank.
Ironically, despite ongoing US- Iran tensions which are only growing stronger, the U.S. Dollar-backed USDT remains the financial safe haven for users navigating censorship, inflation, and now cyberwarfare, according to Levi.
Concluding thoughts
We know that this was not just a regular crypto exploit. This was a geopolitical cyberstrike, (with apparent anti-terror intentions, according to Predatory Sparrow) aiming at dismantling the infrastructure that sustains sanctioned state actors and finances terror groups on the blockchain.
For crypto exchanges and regulators, it may raise several questions.
How deeply embedded are VASPS in global political finance - and how important is their role in major geopolitical events?
What responsibility do platforms hold, if they knowingly are facilitating sanctioned activity? And what are the responsibilities of well-meaning users of such platforms?
What is the role of hacktivists in apparent prevention of terror financing?
How can transaction monitoring tools, like Nominis Vue, play a role in early detection and exposure of sanctioned activity, and prevention of harm in the offchain world?
At Nominis.io, we believe that on-chain transparency, and corroboration with external off-chain sources, is the latest frontier of intelligence.
While we wait for further developments, we can be relatively certain that what happened to Nobitex may not be the last case of regime-tied platforms falling under digital fire.
While we strive for accuracy in our content, we acknowledge that errors may occur. If you find any mistakes, please reach out to us at contact@nominis.io Your feedback is appreciated!





.png)
