In August 2025, the revived Wall Street name Salomon Brothers sent shockwaves through the crypto world after announcing it had completed the process of notifying so-called “abandoned” Bitcoin wallets. The investment bank says it is targeting dormant addresses holding billions in BTC, sparking fierce legal and ethical debates about property rights in a decentralized financial system.
What Are Abandoned Wallets?
Cryptocurrency wallets differ fundamentally from bank accounts. Ownership is tied solely to cryptographic keys, no bank records, no customer files. If a private key is lost, forgotten, or if the owner dies without passing on access, the funds remain forever out of reach.
- 3.7-4 million BTC (nearly 20% of supply) is “lost” in inaccessible wallets.
- At today’s market values, this represents over $250 billion in stranded digital wealth.
- Wallets can become abandoned for reasons ranging from misplaced passwords and discarded hard drives to death without inheritance planning.
These wallets often sit untouched for years, raising the question: are they truly abandoned , or simply dormant?
Salomon Brothers’ initiative underscores the growing collision between traditional finance norms and the decentralized ethos of crypto. Billions in dormant assets remain locked on blockchains, but unlocking them without undermining trust requires new tools and frameworks.
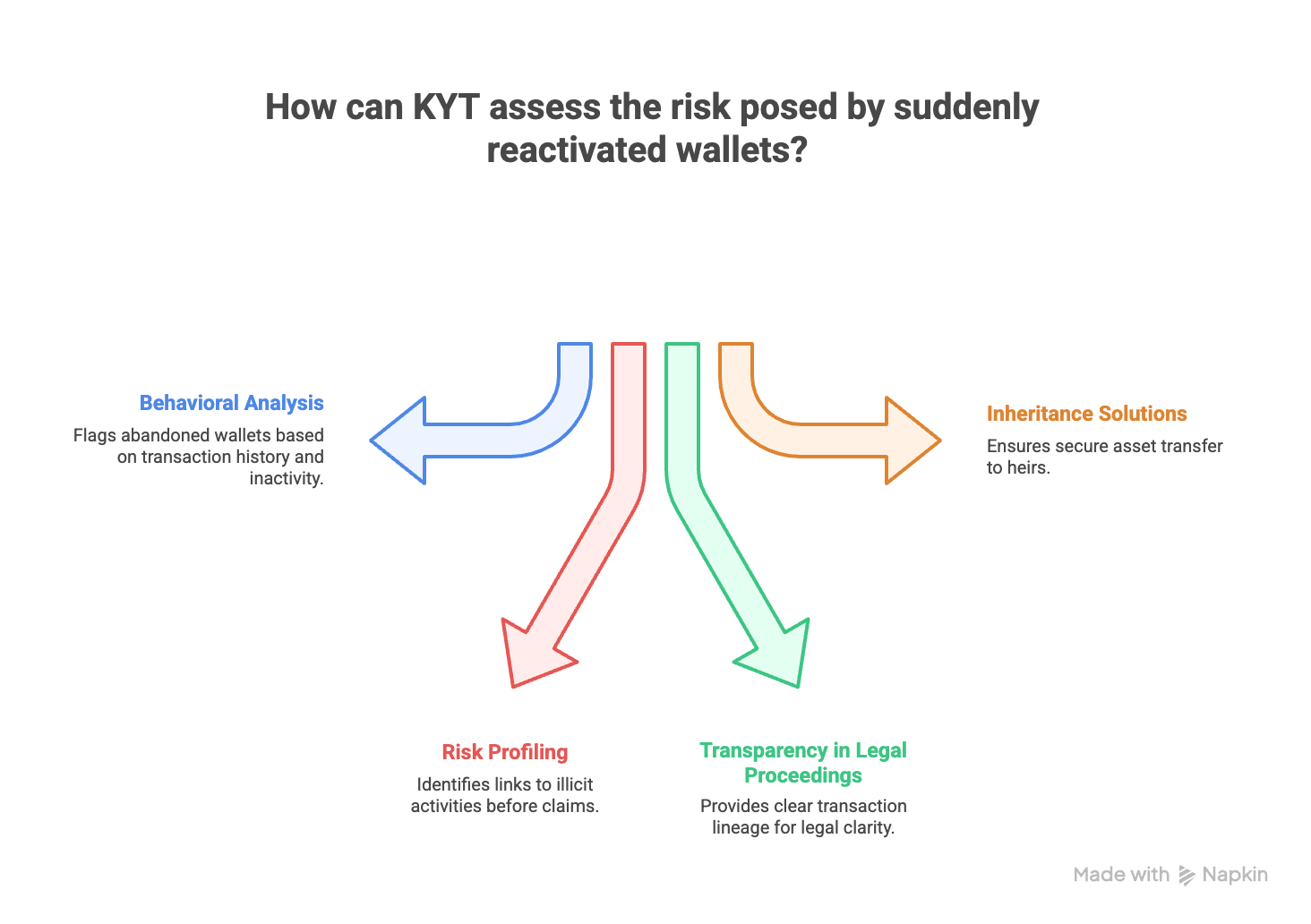
While many abandoned wallets may simply represent lost keys or forgotten accounts, regulators cannot ignore the risk of sudden reactivation. Dormant wallets linked to darknet markets, hacks, or sanctioned entities have resurfaced before, most famously when coins tied to the Silk Road case and the Mt. Gox collapse suddenly moved years later, triggering global compliance alerts. Such awakenings can provide fresh liquidity for money laundering, terror financing, or sanctions evasion. By continuously monitoring these addresses, KYT tools help detect when long-silent wallets “wake up,” assign risk scores, and flag suspicious movements early, a preventive approach that strengthens both compliance frameworks and security.
The role of KYT
KYT could serve as the bridge, offering transparency, risk assessment, evidence that balances innovation with compliance, and bringing clarity to this grey area:
Behavioral Analysis: KYT tools can analyze transaction history, inactivity periods, and spending patterns to flag wallets likely to be abandoned vs. merely dormant.
Risk Profiling: KYT checks can determine whether a dormant wallet has links to sanctioned entities, darknet marketplaces, or terrorist financing before any claim is attempted.
Transparency in Legal Proceedings: By providing regulators and courts with clear transaction lineage, KYT can demonstrate whether a wallet is “clean” or carries exposure to illicit funds.
Inheritance & Custody Solutions: Integrating KYT into digital inheritance frameworks could ensure assets are securely transferred to rightful heirs rather than seized prematurely.
In short, KYT can’t recover lost private keys , but it can provide the data intelligence layer that regulators, institutions, and courts need to separate legitimate abandoned assets from dangerous or contested ones.
Final Thoughts
The question of abandoned crypto wallets is no longer hypothetical. With legacy institutions like Salomon Brothers stepping into the debate, the industry must decide: Should billions in dormant BTC remain forever untouched, or should frameworks emerge to reclaim and repurpose them? Or, alternatively, should we take a more preventive approach, recognizing the risk that long-silent wallets could suddenly awaken and be used for illicit activities, from money laundering to terror financing?
FAQs
1. Why is it difficult to prove a wallet is truly abandoned?
Blockchain only shows activity, not intent. A wallet may remain inactive for years and then suddenly transact. This uncertainty makes it hard to confirm whether coins are permanently lost or simply dormant.
2. Can abandoned wallets ever be recovered without the private key?
No. Without the private key or seed phrase, funds in a wallet cannot be accessed. Some recovery services attempt to crack forgotten passwords, but success is rare.
3. How can heirs legally inherit cryptocurrency?
Heirs need access to the private keys or recovery phrases. Increasingly, estate planning tools and custody services integrate KYT and compliance checks to ensure a smooth and legal transfer of digital assets.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.





.png)
