Overview
The Lazarus Group is one of the most dangerous and prolific state-sponsored cybercrime organisations in the world. Thought to operate under North Korea’s Reconnaissance General Bureau (RGB), the Regime’s intelligence agency, Lazarus Group has been implicated in some of the most disruptive and profitable cyberattacks in modern history.
While they first gained notoriety for politically motivated incidents like the 2014 Sony Pictures hack (likely in response to the release of the anti-North Korea movie, ‘The Interview’) the group has increasingly shifted focus to one goal: theft of funds, specifically cryptocurrency.
Most recently, the group has entered the headlines as the British Treasury Sanctions Office has accused them of the Lykke security breach, in which the UK exchange lost nearly $23 million in June 2024.
According to allied intelligence assessments, the group commonly labelled as Lazarus is believed to be made of up to roughly 7,000 cyber operatives. Their reputation rests on both their technical skill and relentless discipline. Reports suggest a 15-hour work-day, 6 days a week, making them one of the most tireless Advanced Persistent Threat (APT) organisations ever identified. Activity typically begins at midnight UTC, with a pause in the afternoon. Saturdays are treated as work days, and operations sometimes extend into late nights or Sundays, when financial stakes are high or targets are vulnerable, for example on international holidays.

A wanted poster for a North Korean citizen who is thought to be a member of The Lazarus Group.
Analysts believe that Lazarus’ operations are a major source of funding for North Korea’s sanctioned nuclear weapons program, placing their crypto thefts at the intersections of cybercrime, geopolitics and global security.
Country of Origin
Lazarus is widely accepted to be based in North Korea and to operate under government direction. Unlike most cybercrime syndicates which are financially motivated but independent, Lazarus is likely a state actor. Their stolen funds are believed to bypass international sanctions and directly support North Korean military projects.
This state-backing makes them particularly resilient and persistent as they are shielded from traditional law enforcement consequences and motivated by strategic, not just financial, objectives.
Lazarus Group’s largest Crypto Heists
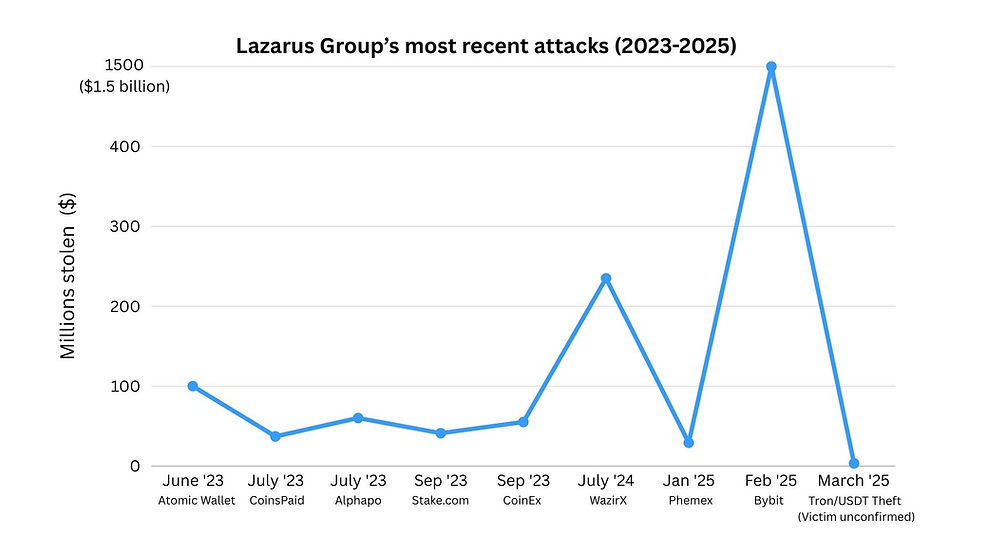
Bybit Hack (2025) - $1.5 billion
In February 2025, Lazarus Group executed their largest known heist to date, targeting Bybit, a major cryptocurrency exchange. The attackers compromised a multisignature wallet used for cold storage. Reports suggest they relied on sophisticated phishing tactics to trick authorised signers into approving a malicious transaction that appeared legitimate. In a single stroke, Lazarus drained over 401,000 ETH valued at roughly $1.5 billion, the largest theft in cryptocurrency history. This incident underscored how even advanced custody solutions, like multisig wallets, can be compromised when human elements are exploited.
Ronin Bridge (Axie Infinity) - $625 million
The March 2022 Ronin Bridge attack highlighted the Group’s focus on DeFi infrastructure. The bridge, which allowed users to transfer funds between Ethereum and Axie Infinity’s custom sidechain, relied on a set of validator nodes to approve transactions. Lazarus compromised 5 of the 9 validators, reportedly through a mix of spear phishing and malware placed on employee systems. Once they controlled a majority, they were able to authorize two massive withdrawals, for 173,000 ETH and 25.5 million USDC. The $625 million dollar theft remained one of the most devastating thefts in DeFI history.
Poly Network (2021) - $600 Million
In August 2021, Lazarus exploited a vulnerability in Poly Network’s smart contract code, which governed cross-chain transactions. The attackers manipulated contract logic to reroute assets to their own wallets, ultimately extracting around $600 million across multiple chains. While a large portion of the funds were later returned, following community pressure and negotiations, the scale of the attack showcased Lazarus’ technical sophistication in exploiting flaws deep in DeFi protocols.
Coincheck (2018) - $530 Million
Coincheck, one of Japan’s largest exchanges, fell victim to Lazarus in January 2018 when hackers targeted the exchange’s hot wallet infrastructure. The attackers managed to siphon off 523 million NEM tokens, valued at around $530 million at a time. Later investigations suggested phishing campaigns against employees and poor wallet security contributed to the breach. Coincheck reimbursed affected users, but the case remains a landmark example of Lazarus exploiting operational weaknesses in centralised exchanges.
KuCoin (2020) - $275 Million
In September 2020, KuCoin announced a security breach that saw hackers drain approximately $275 million in assets from hot wallets. Forensic analysis pointed to Lazarus, who had used phishing-like methods to access private keys. While KuCoin later managed to recover a significant portion of the funds, the attack highlighted the Group’s ability to pivot between DeFI and centralized exchanges, adapting their methods to any weakness identified.
WazirX (2024) - $235 million
In July 2024, Lazarus Group breached WazirX, a leading Indian exchange, and stole a sizeable amount. Analysts believe this was the result of phishing or compromised APIs tied to the exchange’s multisignature wallets.
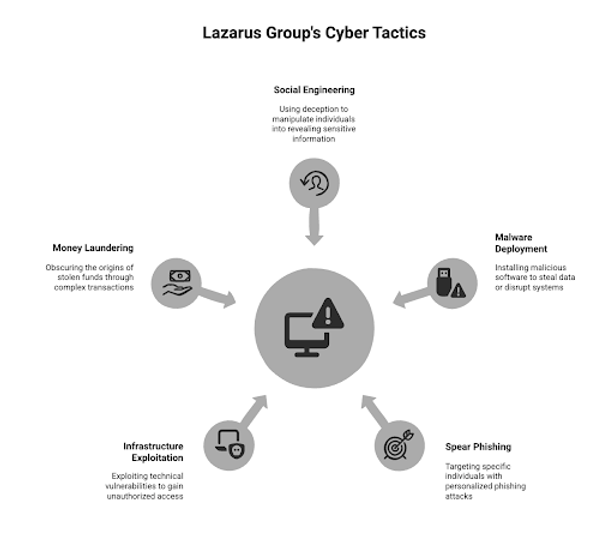
Lazarus Group’s Tactics
Social Engineering
Lazarus group frequently uses fake job offers to compromise targets. In one high-profile campaign, they posed as recruiters from major tech companies on LinkedIn and lured victims into downloading malware-laced files. The tactic was later tied to the 2023 Alphapo hack, where over $60 million was stolen after insiders unknowingly granted access through compromised devices.
Malware deployment
The group has developed sophisticated malware families designed to harvest private keys and login credentials. The Atomic Wallet hack in June 2023, where over $100 million was stolen from 5,500 users, was attributed to Lazarus by deploying custom key-stealing malware that bypassed traditional antivirus detection.
Spear Phishing
Phishing remained one of Lazarus Group’s most effective tools. The Ronin Bridge attack illustrated this clearly: employees were tricked into downloading compromised software, allowing the attackers to infiltrate validator systems and later drain hundreds of millions.
Infrastructure Exploitation
When technical weaknesses exist, Lazarus exploits them. The Poly Network hack showcased how they directly manipulated cross-chain contract logic to redirect funds - demonstrating that they are just as comfortable auditing and exploiting code as they are manipulating humans.
Money Laundering
One funds are stolen, Lazarus Group employs a complex laundering process. This often involves mixing services like Tornado Cash, as well as chains of cross-chain swaps to obscure transaction trails. After the Ronin hack, for example, the group laundered funds through multiple services, forcing regulators and blockchain investigators to issue red-flag alerts to exchanges worldwide.
Why this matters for Compliance
For compliance professionals, Lazarus Group represents one of the clearest cases where financial crime and geopolitical risk collide. Their stolen funds are directly linked to sanctioned programs, meaning that any institution that interacts with wallets tied to Lazarus risks serious sanctions violations. Moreover, the scale of their operations demonstrates that no exchange or DeFi protocol is too big or too secure to be targeted.
On a positive note, regulators are increasingly aggressive in issuing wallet sanctions and advisory tied to Lazarus Group. For crypto exchanges, fintechs and Web3 projects, this highlights the urgent need for real-time transaction monitoring, sanctions screening, and threat intelligence integration. Without these, businesses risk not only financial loss but also regulator and reputational fallout.
Our takeaway
The Lazarus Group is not just another hacking syndicate. It is a state-back actor, working on behalf of a hostile nation, whose activities impact global financial stability. Their heists reveal how fragile parts of the crypto ecosystem remain, and their tactics evolve with every new target. In the recent case of the Lykke breach, which took place June 2024, we saw that it is not only important to predict and understand their evolving tactics, but also catch their behaviours in a timely manner. For the industry, the lesson is clear: robust monitoring tools, continuous intelligence gathering, and strict compliance protocols such as Nominis Vue are the only effective defenses against a group that blends the resources of a nation-state with the agility of cybercriminals.
Lazarus Group: FAQs
Who is Lazarus Group?
Lazarus Group is a state-sponsored hacking collective widely believed to be operating under the direction of North Korea’s government. Active since at least 2009, the group has carried out cyber operations ranging from disruptive attacks, like the 2014 Sony Pictures breach, to some of the largest cryptocurrency thefts in history. Lazarus Group is known best for their sophisticated use of phishing campaigns, malware, and DeFi exploits to steal billions of dollars, which analysts believe helps fund North Korea’s weapons programs.
Which countries or organisations have accused Lazarus Group of cyberattacks?
Multiple governments and international organisations have publicly attributed attacks to Lazarus Group. The United States, United Kingdom, Japan, and South Korea have all issued statements linking Lazarus Group to cyber espionage and large-scale financial thefts.
Why is Lazarus Group considered a national security threat?
This means that each successful hack strengthens North Korea’s ability to bypass international sanctions. Beyond the financial risk, Lazarus Group is also believed to conduct espionage operations, targeting critical infrastructure, government networks, and defence contractors. For this reason, organisations like the CIA in the US classify Lazarus Group as a major national security threat.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.





.png)
