(Re-uploaded April 2025)
February 2025 witnessed a surge in crypto related attacks, ranging from rug pulls and social engineering to contract vulnerabilities and private key compromises. The month highlights the growing complexity and diversity of attack vectors within the crypto ecosystem, with notable incidents including the infamous Bybit attack, and the Infini attack taking place shortly after.
This report provides an overview of the key incidents, shedding light on the methodology used by attackers and the major financial losses incurred as a result of regulatory compliance failure.
Major attacks:
GANG token - 02.02.2025
Investors were left shocked when an apparent rugpull or honeypot exit scam seemed to have been executed by the creator of the GANG token. Once trading started, the creator, MrPunkDotEth, who retained about 95% of the supply, quickly dumped their holdings which crashed the price and left investors holding worthless assets. Multiple wallets were used to cash out, making it more difficult to trace movement of assets, and the funds were converted through Binance, which further obscured the trail.
Impact: $10 million
IonicMoney - on the Mode Network - 05.02.2025
Ionic Money - formerly Midas - suffered an exploit on the Mode network, executed via social engineering. Attackers deployed a fake Lombard Bitcoin Token, and then manipulated the approval mechanism so they could withdraw assets.
The attack saw the loss of approximately $8.6 million, with attackers transferring assets to Ethereum and mixing it through Tornado Cash, preventing authorities from tracing the funds.
Impact: ~$8.6 million
ADACash - 07.02.2025
A flash loan was detected on an unverified contract, resulting in sizable losses. The attacker exploited an unprotected function - depositBNB()- and was able to exchange 226 BNB for ADACash, making a profit via sandwich trading where they took advantage of pending transactions in the mempool, waiting to be added to the blockchain.
Impact: $108,000
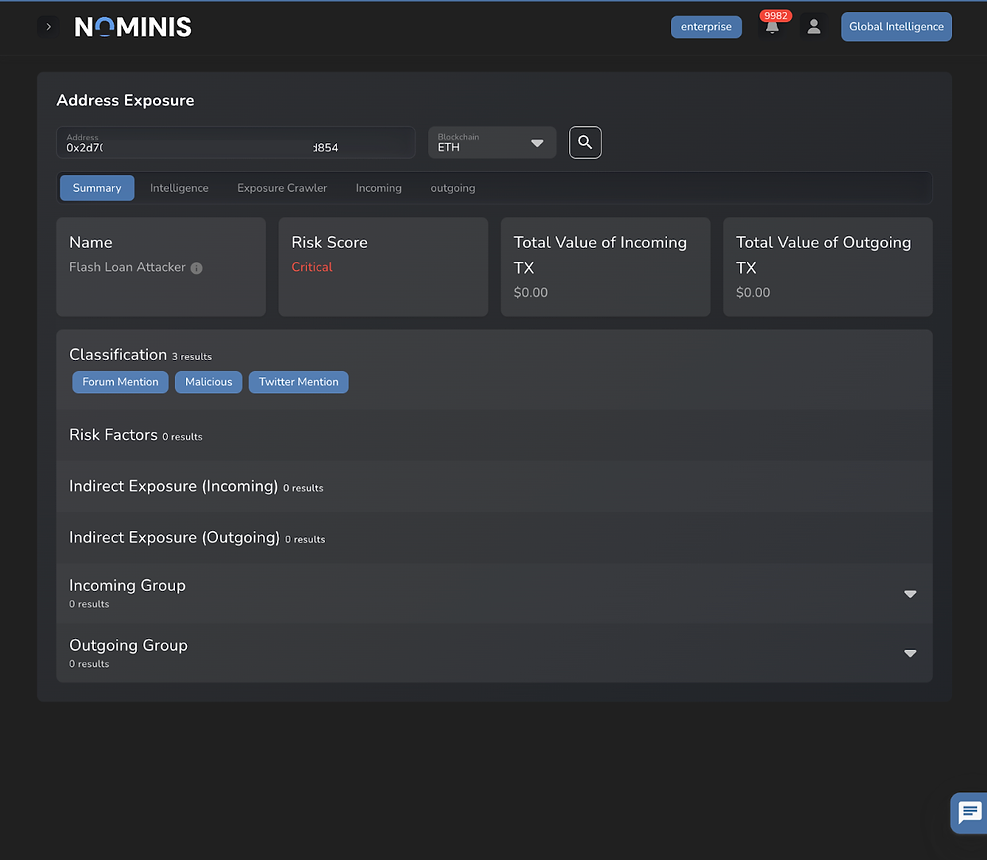
Investigation from wallet screening tool Nominis Vue, demonstrates the critical risk score assigned to the wallet associated with the flash loan attack, but demonstrates a cessation in transfer activity to and from the wallet.
BankXio - 07.02.2025
BankX appeared to have suffered an attack on BSC, ETH and Optimism via a reentrancy attack. The exploit targeted the swapXSDforETH() function within the Router contract. The function was unprotected, allowing it to be manipulated, specifically to not update pool states accurately before executing the burn operation. The attacker was able to burn XSD tokens to make a profit, receiving ETH from the pool in return.
Impact: $43,000
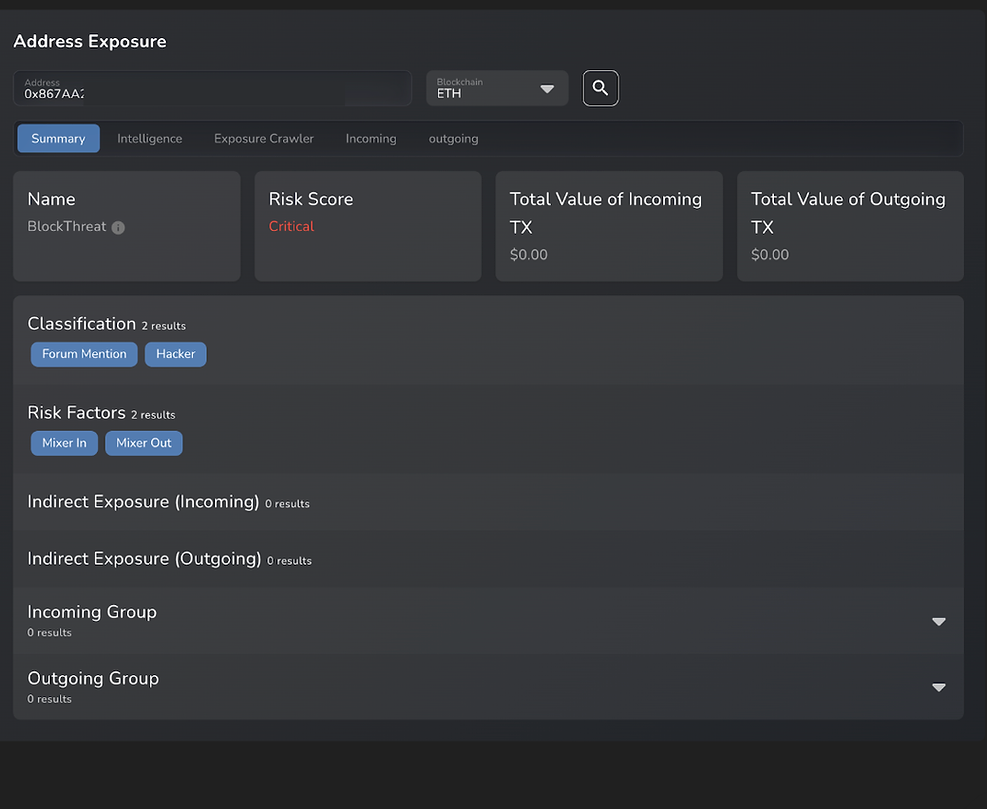
@CashverseLLC - 08.02.2025
According to the SlowMist security team on X, Cashverse suffered an attack on BSC due to a contract vulnerability, resulting in losses of $107,900. Though little other information is available, insights from Nominis Vue together with information from SlowMist suggest a relationship between the malicious addresses involved in the Cashverse attack and the ADAcash attack mentioned earlier.
Impact: $107,900.00
Peapods Finance - 08.02.2025
Peapods Finance suffered an attack due to a contract vulnerability - a ‘slippage frontrun in its reward contract’s depositFromPairedLpToken function’ allowed a malicious actor to manipulate the rewards calculated. The attacker exploited the _slippageOverride parameter to manipulate the price and extract value from the contract, making the contract accept unfavourable trade conditions. Given the trade was manipulated, and then the transaction was back-run, another methodology to perform a sandwich attack, the attacker profited from the difference.
Impact: $3,500
Open Ocean Exchange - 11.02.2025
Open Ocean shared on X their efforts to halt an attack on their Limit Order contract on Base. They paused the contract which was newly released, preventing further malicious actions, but saw that $22,000 worth of funds had been affected. Impacted users received notifications and assistance, meanwhile, the Open Ocean updated the vulnerable implementation contract with a more secure one.
Impact : $22,000
Four.MeMe - 11.02.2025
On 11 February Four Meme, who serves as a hub for creating and promoting meme coins on the BNB chain, experienced a malicious attack, and reported it on X. The hub experienced a DEX Pool Pre-initialization Attack, with hackers targeting the growing liquidity in meme tokens. The hacker pre-created and initialized the DEX trading pair on PancakeSwap with an extremely high price. The hub migrated this memecoin to the DEX, calling the function that creates and initializes a Pool if the pair does not already exist. However, given the attacker had already created the pair, the hub unknowingly added liquidity at the manipulated price. Then the attacker swapped memecoins for a large amount of WBNB, draining the liquidity pool and gaining a profit.
Impact: $183,000

kLend - 12.02.2025
KLend has suffered a $9.5M exploit on the Starknet network. Stolen funds were bridged to Ethereum and laundered via Railgun. The attacker manipulated the Lender in a number of steps, namely depositing 1 Wei of wstETH, the smallest possible amount, setting a baseline value of the accumulator. The attacker used flashloans to donate large amounts of wstETH to the contract, artificially inflating the lending accumulator from 1.0 to the extreme value of 4069 trillion. The protocol assumed massive revenue had been generated. Then the attacker repeatedly deposited and withdrew small amounts, triggering rounding errors. The attacker ultimately withdrew more than what was recorded, draining the contract, as the raw balance wasn't burning fully due to the rounding down error.
zkLend officially admitted that it had been hacked, saying that the hacker could keep 10% of the funds as a white hat bounty and send the remaining 90% (3,300 ETH) back. The withdrawal function on the zklend protocol has been suspended.
Impact: $9,500,000
Libra Memecoin - 16.02.2025
$LIBRA, a meme token made popular and endorsed by Argentinian President Javier Milei, has been rugpulled in an attack causing significant financial losses for investors. Marketed as a potential catalyst for Argentina’s economic growth, Libra’s capitalization soared to about $4.5 billion at its peak. However, it is suggested that 82% of the token’s supply was held by a single cluster. After reaching its peak, LIBRA’s market value plummeted by over 94% within hours, with some analysis suggesting that insiders, part of the ‘single cluster’ withdrew substantial liquidity totaling about $107 million. As a result, analysts have labelled the case as a rug pull given the classic characteristics, and the situation has created huge political repercussions for President Milei, with opposition suggested misconduct related to his promotion of the token.
Impact: $286,000,000.00
Cardex - 18.02.2025
Cardex, an ‘onchain fantasy game’, experienced a hack associated with a compromised session key. Cardex allows users to create ‘session keys’ which let them buy, sell and transfer shares. The same session key was used for all users and accidentally exposed the key in their website’s code. The hacker found an active session, and used the leaked key to buy shares using a victim’s wallet, transfer the shares to themselves and sell the shares to steal the victim’s ETH. Approximately 9,000 wallets suffered from the hack, however Cardex has worked to recover losses.
Impact: $400,000
StepHeroNFTs - 21.02.2025
The StepHeroNFT project on BSC, which has been lying dormant, was exploited leading to a loss of $90k. The attacker used a reentrancy bug in the claimReferral() function, which allowed them to withdraw funds before the referral balance was updated. Repeatedly triggering the function allowed the attacker to drain the contract’s funds in a single transaction before changes to the contract could be updated.
Impact: $90,000.00
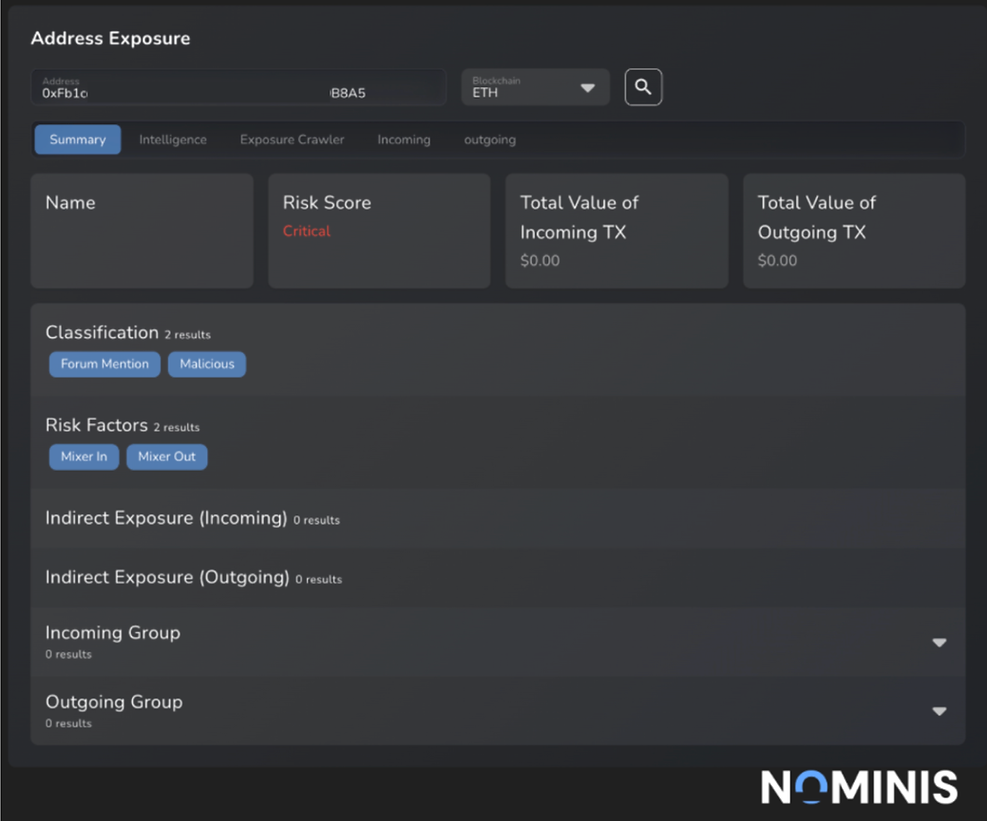
Bybit - 21.02.2025
Bybit, a major cryptocurrency exchange, experienced a significant security breach, leading to the theft of around $1.46 billion in Ethereum (ETH). The attackers exploited a vulnerability in the multisignature (multisig) cold wallet using a complex phishing and smart contract manipulation. Attackers gained control of a cold wallet while assets from the wallet were being transferred to a warm wallet. Intelligence suspects the involvement of notorious North Korean hacking entity, Lazarus Group.
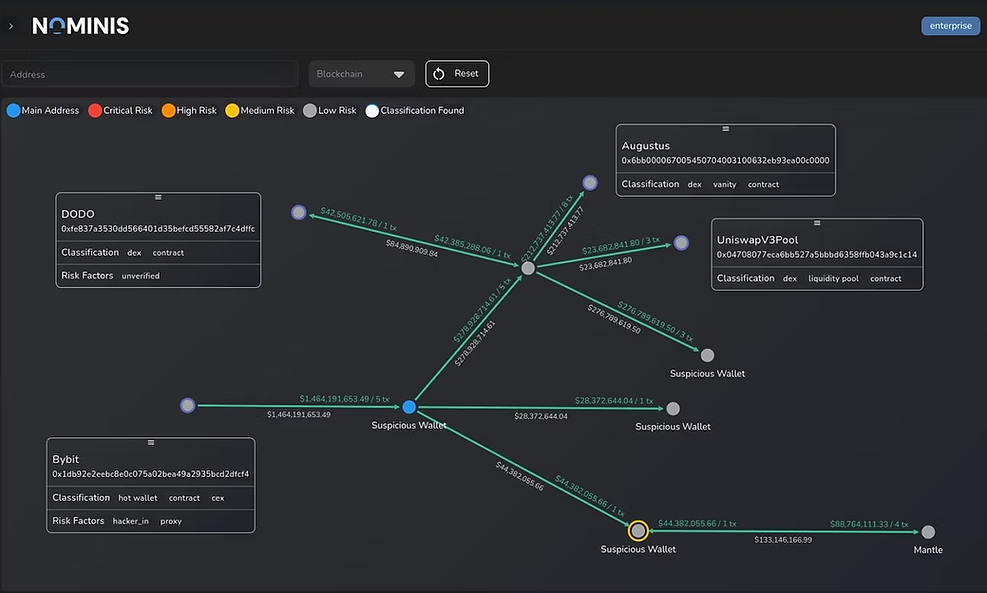
Exclusive findings from the Nominis Vue platform, demonstrating the interaction between Bybit and several suspicious wallets.
Impact: $1,400,000,000.00
Infini - 24.02.2025
Infini, a Hong Kong-based stablecoin neobank, suffered a huge attack following a smart contract exploit. The attacker abused compromised administrative privileges on a smart contract linked to Infini and retained admin privileges. By manipulating the contract’s settings, they were able to drain assets in USDC, which were then sent to an address funded by Tornado Cash. Tornado Cash the cash would obscure the origin and movement of funds. The attacker then swapped the stolen USDC into ETH.
Impact: $50,000,000
Suji Yan - 27.02.2025
Yan, founder of Mask Network, lost approximately $4 million in a crypto hack. Suspicious outflows were recognised leaving Yan’s account, which included ETH, WETH, ezETH, pufET, MASK and USDT. The stolen funds were converted to Ethereum and split across different wallets to obscure the transaction trail. Yan suspected that the attack occurred while he left his phone unattended.
Impact: $4,000,000.00
Final remarks:
Major cases this month by type:
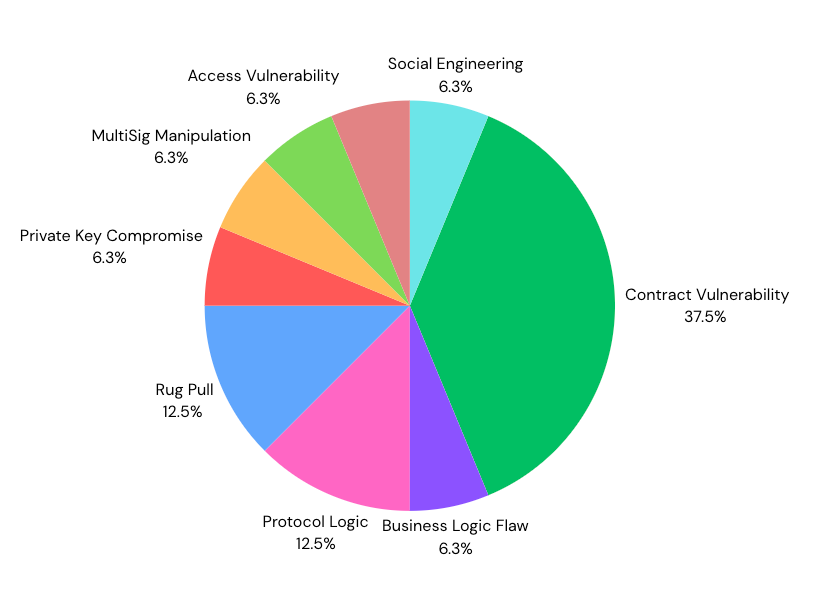
The attacks throughout February 2025 reveal a diverse range of exploit methods, with rug pulls, flash loans and contract vulnerabilities particularly prevalent. The major attacks in February amount to $1,750,457,408.80, dwarfing January’s total losses of $54,253,400.00. While January experienced 13 attacks, February saw 15 major attacks with three particular incidents causing the incredibly high Feburay losses. The Bybit and Infini attacks alongside the $LIBRA memecoin rug pull totalled $1,736,000,000.00 alone.
The sheer number of attacks as a result of contract vulnerabilities highlight the importance of smart contract audient performance, to prevent such manipulation of functions within contracts. Whitehat bounty programs, where projects encourage whitehat hackers to try to hack the system to find vulnerabilities can also be an effective way to prevent smart contract hacks upon public launch. These methodologies feature in frameworks that are used to recommend strategies for exchanges, coins or other crypto projects to remain compliant with regulatory requirements, and to prevent hacks such as these.
The attack on Bybit, assumed to have been performed by North Korea’s Lazarus Group, underscores the vulnerability of even major platforms, and the major importance of closing security vulnerabilities and approaching movement of assets with caution.
Meanwhile, the case of Suji Yan, demonstrates the potential targeting of individuals in powerful positions, given his role as CEO of Mask Network.
The frequency, variety and scale of these attacks emphasize the urgent need for improved security protocols, continuous monitoring tools like Nominis Vue, and enhanced incident response strategies to mitigate future threats in the crypto space.
While we strive for accuracy in our content, we acknowledge that errors may occur. If you find any mistakes, please reach out to us at contact@nominis.io Your feedback is appreciated!






.png)