As Web3 ecosystems continue to expand globally, they are also growing as prime targets for covert operations - particularly from North Korean operatives posing as remote developers. Recent investigations have uncovered a disturbing trend: state-backed North Korean IT and Web3 workers infiltrating crypto companies by faking their identities, passing interviews with falsified credentials, siphoning earnings back to the regime as well as critical information about Western Web3 projects.

North Korea has already been known for sizeable attacks, such as the $1.4 billion Bybit attack in February 2025, but now the focus is shifting - rather than these enormous attacks earning headlines in the news, Web3 industry actors are recognising the inside jobs performed by individual actors on behalf of the DPRK.

The FBI’s press release announcing the Bybit hack as the responsibility of North Korea - Source
In 2024, a detailed report from a reliable source revealed that major blockchain projects such as Injective, Fantom, Sushi and Yearn Finance, unknowingly have employed individuals connected to the North Korean Government. In some of these cases, the employees were granted deep access to codebases, admin keys, and smart contract systems.
The implications of these internal threats go far beyond payroll fraud or identity theft. Many of these positions have privileged roles such as admin keys or upgrade rights, that can be used to abuse smart contracts if placed in the wrong hands. A malicious developer does not need to exploit the contract from the outside, since they are part of the inside. With these permissions they could potentially introduce backdoors, exploit governance mechanisms, or even rug-pull projects silently, draining the liquidity pool.
These incidents underscore a critical gap in Web3 security: the lack of Know Your Employee (KYE) protocols. While KYT (Know your Transaction) and KYC (Know your Customer) are now more commonly known in the compliance world, most decentralized teams still hire globally, with minimal due diligence and verification. The trust-first culture of open-source and remote collaboration, enhanced by the ‘digital nomad’ culture, was once a strength, but could now be an intense vulnerability.
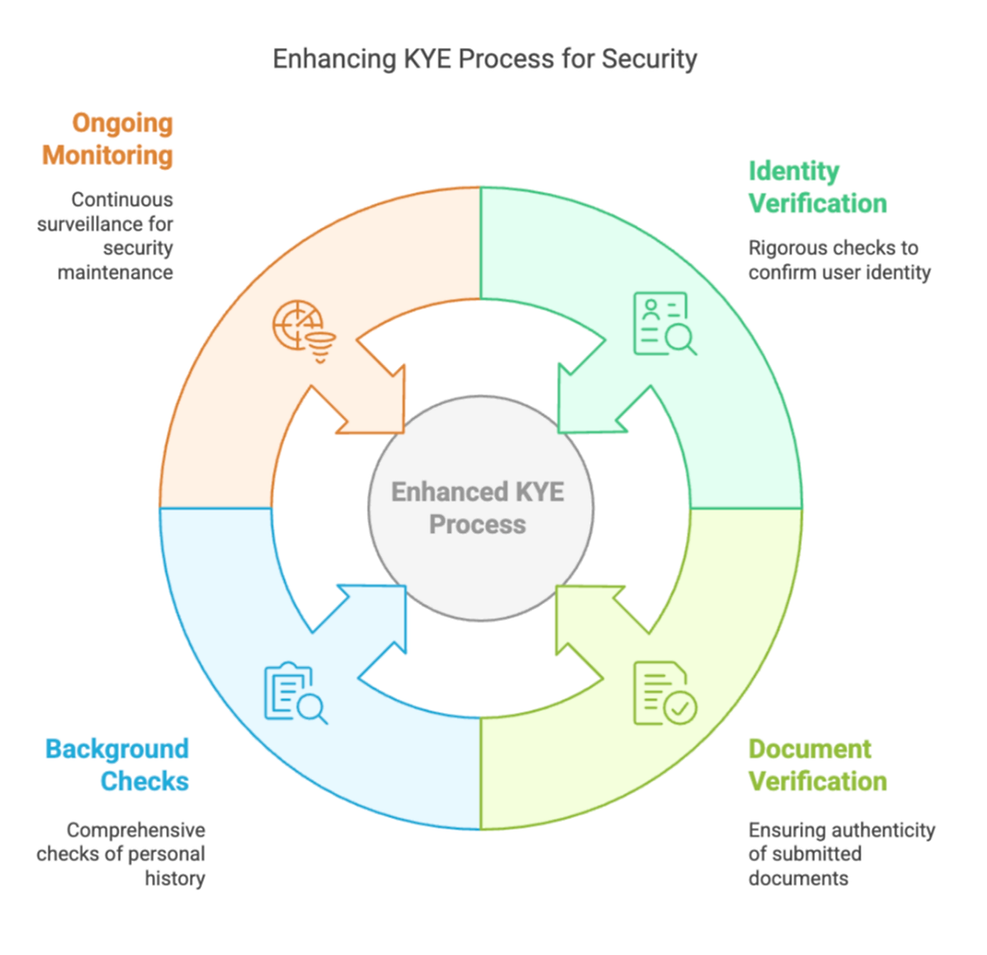
Ideal KYE Processes for crypto projects (please note: this list is not comprehensive!)
- Rigorous identity and location verification (not limited to exclusively LinkedIn or GitHub checks)
- Verification of documents, ensuring they are genuine
- Background checks from reliable sources including criminal history, employment history and educational history
- Ongoing monitoring and re-verification, to ensure that KYE is a constantly monitored framework rather than a one-time check at the beginning of a contract
Both the FBI and the US Treasury, as well as other governmental institutions across the globe have issued warnings urging companies to adopt stronger vetting procedures when onboarding new employees. Compliance in this case is no longer about following regulations - it is about preventing your involvement in terror financing and funding a sanctioned regime.
In Web3, while trust is good, verification is even better. Just as KYT monitoring at Nominis (Know Your Transaction) helps detect suspicious activity on-chain, off-chain and in the deep and dark web, suitable and rigorous KYE assists in preventing this activity from being enabled in the first place.
FAQs:
What is KYE and how is it different from KYC or KYT?
KYT (Know your Transaction) and KYC (Know Your Customer) focus on customer identity and transaction identification for compliance and Anti-Money Laundering purposes. KYE refers to the process of verifying the identity, background and legitimacy of employees - especially those who upon employment will have privileged access to smart contracts, such as developers or admins. Generally, KYE focuses inwardly, to protect companies from insider threats, fraud or infiltration.
How are North Korean Operatives infiltrating Web3 projects?
They often pose as remote developers using fake identities, stolen or fabricated documents, and polished GitHub/ LinkedIn profiles. They secure roles at startups or DAOs, and then channel salaries or access back to the North Korean regime.
While we strive for accuracy in our content, we acknowledge that errors may occur. If you find any mistakes, please reach out to us at contact@nominis.io Your feedback is appreciated!





.jpg)
.jpg)