Recent intelligence has uncovered a significant threat to global cybersecurity infrastructure: the exposure of Medialand, a bulletproof hosting provider long suspected of enabling a wide range of illicit activities. This revelation, believed to be linked to the same actors behind the February 2025 leak of over 1,000,000 internal messages from the Black Basta ransomware group, underscores a disturbing trend: the deep and strategic integration of cryptocurrency into cybercriminal ecosystems.

Cryptocurrency: The Preferred Rail for Cybercrime
Medialand's infrastructure played a crucial role in supporting cybercriminals by providing safe harbor for operations including ransomware deployment, phishing kit hosting, command-and-control servers, data leak platforms, and code-signing systems. What’s most alarming is the financial backbone behind these services: leaked internal documents show that most payments were facilitated through cryptocurrencies, reinforcing digital assets as the go-to medium for anonymized, high-risk transactions.
A detailed analysis by Analyst 1 revealed multiple categories of crypto transactions: ransom payments, salary distributions, commission-based payouts, and working addresses used to pay external service providers unrelated to Black Basta’s operations. Additional findings included crypto-to-cash conversions and laundering requests exchanged between threat actors—demonstrating how financial obfuscation is embedded in their operational playbook.
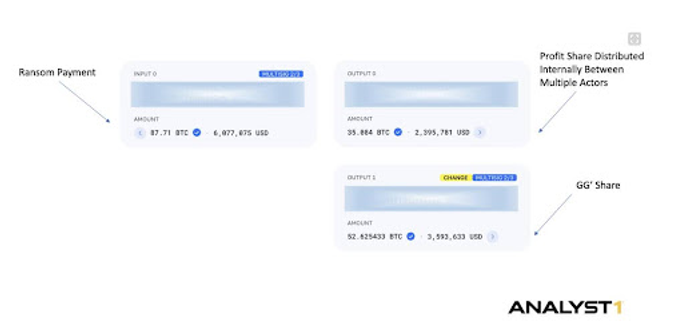
Leaked Messages: A Window into the Human Side of Cybercrime
The trove of leaked Black Basta messages, now integrated into a custom GPT bot, provides investigators and researchers with a rare opportunity to explo
re not only the group's crypto activity, but also their internal communications, attack strategies, ethical conflicts, and even embarrassing missteps.

Proactive Risk Detection: Beyond On-Chain Analysis
Effective cybersecurity demands a proactive approach that extends beyond traditional on-chain tracing. The Medialand case illustrates the importance of combining blockchain analysis with off-chain intelligence—such as chat logs, metadata, and behavioral indicators—to construct a complete threat profile.
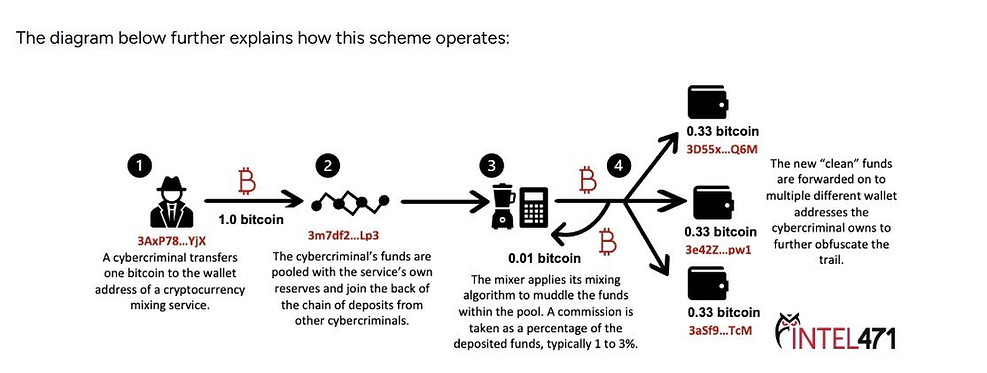
From the leaked conversations, Analyst 1 further noted that not all high-revenue companies are viewed as profitable targets. Instead, attackers prioritize entities with a higher likelihood of compliance. The U.S. and Germany were explicitly flagged as regions most likely to pay ransoms, making them primary targets. Conversely, countries identified as "friendly" (Rus: дружественные страны), such as China, are often excluded due to geopolitical considerations—highlighting the calculated nature of threat actor targeting strategies.
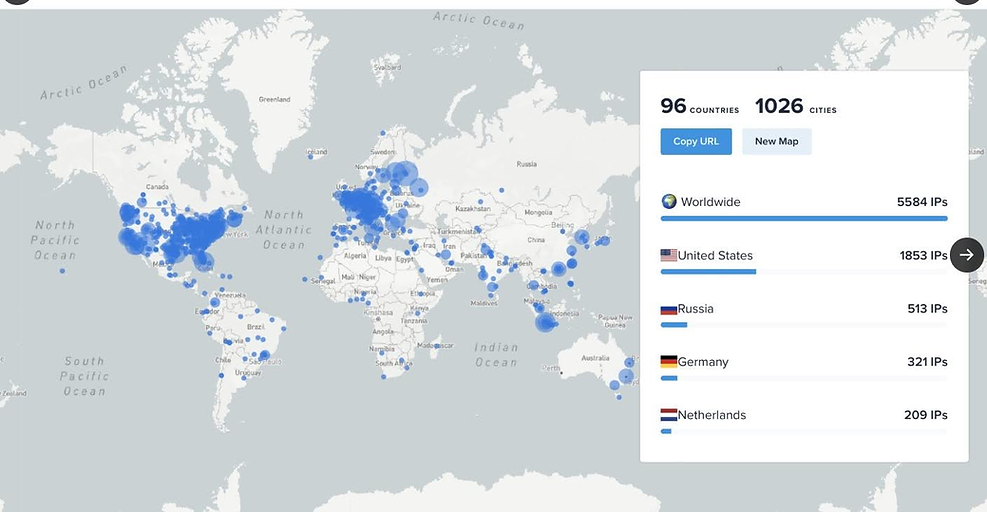
Geolocation Intelligence: IP Mapping and Regional Threat Focus
In addition to financial data, a comprehensive IP address map was compiled from the chat logs, visually highlighting global activity concentrations. This geographic insight, layered with behavioural and transaction data, allows investigators to pinpoint operational hotspots and enhance attribution efforts.
The Urgent Need for Transaction Monitoring
The Medialand exposure is a clear call to action: robust transaction monitoring tools—especially Know Your Transaction (KYT) systems—based on “on -chain and off -chain” data are no longer optional. With access to wallet addresses, payment records, and potential identifiers, cybersecurity teams can now correlate Indicators of Compromise (IoCs) with blockchain intelligence to map out illicit financial flows in real time.
Without proactive KYT implementation, early signs of suspicious activity—such as wallet obfuscation, unusual movement patterns, or links to threat actors—can go unnoticed. This is particularly critical for crypto exchanges, wallet providers, OTC desks, and compliance teams facing increasing regulatory scrutiny.
Final Thoughts
The Medialand case is a stark reminder that as crypto adoption accelerates, so too does its exploitation. To keep pace with evolving threats, the crypto industry must embrace advanced blockchain intelligence and real-time KYT systems.
In the digital asset world, transparency doesn’t happen by default—it must be built, enforced, and constantly refined through the right tools and continuous vigilance.
FAQs:
1. What is a bulletproof hosting provider?
Bulletproof hosting providers offer web hosting services that turn a blind eye to, or actively protect, malicious content and criminal activity. Unlike traditional hosts, they often ignore takedown requests and shield their clients from law enforcement, making them a favourite among cybercriminals.
2. Why do cybercriminals prefer cryptocurrency?
Cryptocurrencies like Bitcoin or Monero offer pseudonymity, allowing users to send and receive funds without directly revealing their identities. This makes it harder for authorities to trace transactions, especially when layered through mixers or privacy coins—making them ideal for high-risk, illegal activities.
3. Can KYT tools track where crypto transactions are happening geographically?
At Nominis, KYT doesn’t stop at tracking wallet behavior—it also incorporates geolocation insights by analyzing off-chain data like IP logs, hosting providers, and network patterns. This allows us to flag high-risk regions, monitor jurisdiction-specific threats, and understand the geographic distribution of illicit activity. It’s how we go beyond the blockchain to deliver actionable, context-rich intelligence.
While we strive for accuracy in our content, we acknowledge that errors may occur. If you find any mistakes, please reach out to us at contact@nominis.io Your feedback is appreciated!






.png)