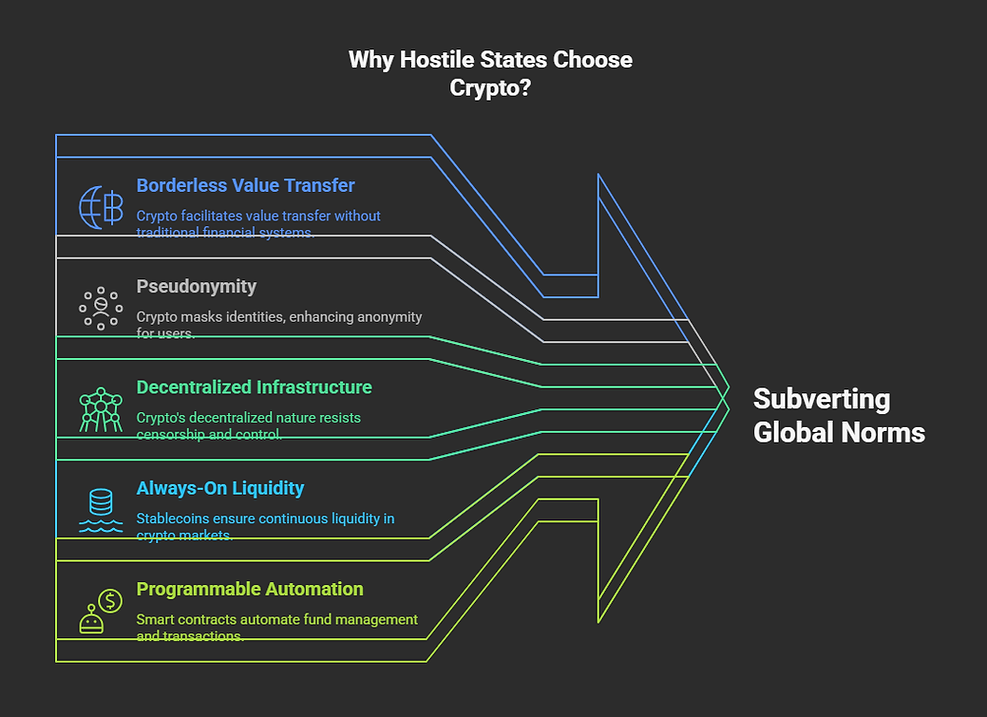
As the financial and cyber frontiers blur, hostile state actors like Russia, Iran, and China are increasingly exploiting cryptocurrency not just as a medium of exchange, but as a tool of influence, espionage and sanctions resistance. What was once the realm of early adopters and technologists is now a battleground for statecraft in the age of decentralization.
From teenage spies paid in Bitcoin to proxy militias bankrolled via stablecoins, crypto has emerged as the preferred financial instrument of states operating beyond the boundaries of international compliance.
Russia: From Hackers to Teenage Operatives
In a 2024 case that shocked European intelligence circles, Canadian teenager Laken Pavan was arrested after being recruited by what investigators identified as Russian intelligence-linked operatives. His mission: conduct surveillance across European sites. His payment: approximately $500 in Bitcoin.

This micro-transaction unraveled a macro-network. The funds came from a wallet linked to over $600 million in activity, suggesting a vast, state-directed crypto infrastructure supporting espionage, cyber operations, and recruitment. Rather than relying on traditional spycraft, Russian operatives are now using decentralized micro-payments to activate individuals across borders,often without ever meeting them in person.
Iran: Recruiting Israelis via Crypto Payments
Iranian intelligence has intensified its use of cryptocurrency to recruit Israeli citizens for covert activities. In 2024, seven Israelis, including minors , were arrested for photographing military and infrastructure sites in exchange for crypto payments, reportedly amounting to hundreds of thousands of dollars . These individuals were approached via messaging apps and promised anonymity through digital assets.
The trend extended beyond youth. In March 2025, a 65-year-old Israeli man was indicted for carrying out surveillance assignments for Iranian handlers, including photographing the Haifa port and nearby military facilities, with payments made in cryptocurrency.
By late 2024, Israel’s internal security agency Shin Bet uncovered a broader spy network of nearly 30 Israelis, many recruited through Telegram and dating platforms. Initial assignments included vandalism, escalating to sensitive intelligence collection. All payments were conducted in crypto to obscure the financial trail.

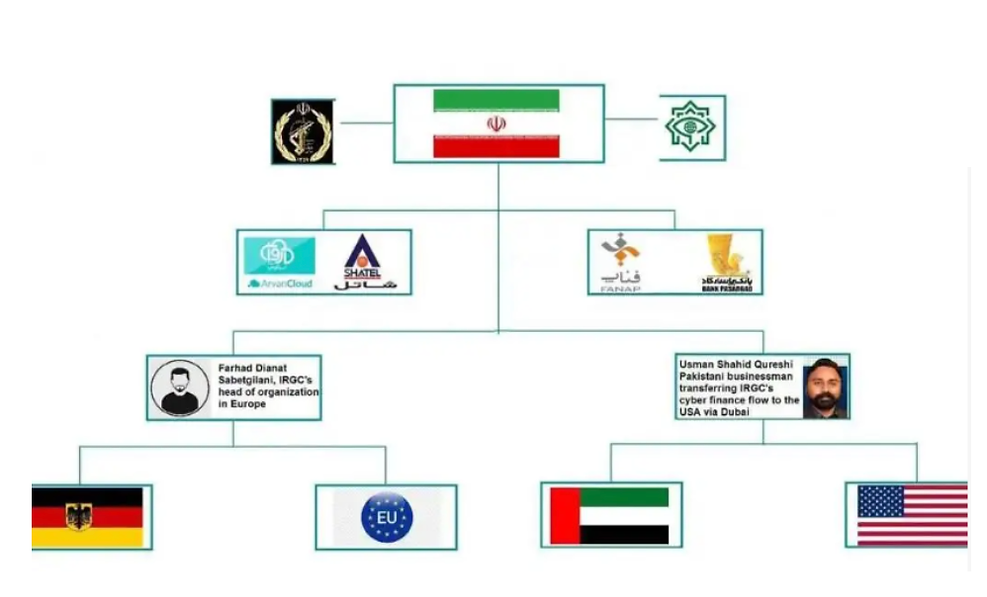
Iran’s use of crypto is deeper and more systemic. Under long-standing sanctions, the Iranian regime has embraced digital assets as a lifeline to fund internal operations, circumvent trade restrictions, and support regional proxies.
With state-backed Bitcoin mining, informal exchanges, and networks of Gulf-based sarafs (money brokers), Iran’s Revolutionary Guard Corps (IRGC) has facilitated covert payments to groups like Hezbollah and the Houthis. Recent intelligence points to extensive use of stablecoins, especially Tether (USDT), to transfer value discreetly across Asia and the Middle East.
These flows bypass traditional banking channels, and due to the pseudonymous nature of blockchain, leave investigators chasing complex trails that blend on-chain footprints with off-chain identities.
China: Strategic Enablement, Not Just Adoption
Although China bans crypto trading domestically, it plays a key global role as a strategic enabler for other hostile states. In 2024, the EU moved to sanction Chinese banks like China Construction Bank for facilitating sanctions-evading trade with Russia, including crypto-linked transactions. Chinese companies have also been tied to Bitcoin mining operations in Iran, bolstering Tehran’s ability to use crypto for sanctions evasion . Meanwhile, Chinese exporters have supplied dual-use tech to Iran’s military, aiding drone production and crypto-powered procurement. Crypto is also being used in Russia-China oil trades, often routed through stablecoins like USDT . While China avoids direct crypto sanctions violations, it remains a critical link in the infrastructure enabling hostile crypto flows.
The Tools to Fight Back: Multi-Layered Crypto Intelligence
Despite crypto’s inherent opacity, it remains traceable, if the right tools are in place. A new generation of blockchain forensics platforms are helping governments and investigators follow the money across borders and layers of obfuscation.
The Intelligence Stack

Platforms like Nominis provide law enforcement-grade tools for automated wallet monitoring, behavioral risk scoring, and real-time sanctions alerts, bringing visibility and structure to activity that would otherwise remain hidden in the blockchain’s shadows.
Conclusion: A Decentralized Arms Race
Cryptocurrency has enabled global inclusion and innovation, but it has also given hostile state actors a powerful tool to fund covert operations, bypass sanctions, and project power. The same decentralization that empowers citizens can also empower regimes operating outside international norms.
The answer is not to fear the blockchain, but to illuminate it. With robust crypto intelligence tools and coordinated enforcement, we can expose even the most covert uses of digital assets and ensure that the world’s next conflict isn’t financed in silence, one stablecoin at a time.
Hostile State Actors: FAQs
Q: Why don’t traditional banking controls stop these crypto-based operations?
Traditional financial controls rely on centralized institutions and SWIFT-based systems, which crypto bypasses entirely. Without direct ties to regulated banks, actors can move funds through decentralized platforms with minimal oversight, making it difficult for standard compliance systems to detect.
Q: What makes stablecoins particularly attractive for covert state operations?
Stablecoins like USDT and USDC offer the speed and anonymity of crypto with the price stability of fiat, making them ideal for discreet, high-volume transfers that won’t lose value mid-transaction. They're also widely accepted across exchanges and OTC desks, even in high-risk jurisdictions.
Q: Can crypto regulation alone stop hostile actors from exploiting blockchain networks?
No, regulation must be combined with blockchain intelligence, international cooperation, and off-chain investigative methods. Hostile actors often use a mix of crypto and traditional channels, requiring a holistic, multi-layered response that goes beyond regulation alone.
While we strive for accuracy in our content, we acknowledge that errors may occur. If you find any mistakes, please reach out to us at contact@nominis.io Your feedback is appreciated!






.png)