August 2025 Monthly Report
- Nominis Intelligence Unit
- 6 days ago
- 9 min read
August 2025 was a turbulent but comparatively lighter month for crypto exploits. While major losses totalled ~$65 million, less than half of July’s ~$141 million, the industry still faced serious disruptions. However, this was overshadowed by widespread phishing campaigns targeting individual wallets, which alone accounted for an enormous $97 million in losses. High-profile incidents ranged from the $48 million breach at BTCTurk, to the suspicious disappearance of CrediX, underscoring the diverse and persistent threats facing the sector.
At the same time, investigative breakthroughs revealed historic thefts, insider fraud and the persistence of illicit markets, while new compliance and intelligence tools emerged to strengthen defences. This report highlights the major attacks, significant events and elusive findings from the Nominis Intelligence Team, offering a detailed look at the evolving threat landscape in August 2025.
Major Crypto Exploits August 2025
CrediX - 04/08/2025
Type: Access Control
At the beginning of the month, CrediX Finance, a DeFi lending protocol, was exploited for over $4 million worth in crypto. Attackers appeared to gain access to its multisig admin and bridge wallets, enabling them to mint unbacked collateral tokens and drain liquidity pools. The stolen funds were bridged from the Sonic blockchain to Ethereum via Tornado Cash-funded addresses. The protocol immediately paused its website and deposits to prevent further damage, and reportedly managed to successfully negotiate with the hacker to return the funds. The attacker allegedly agreed to return the full amount within 24 to 48 hours in exchange for a payment from the protocol’s treasury.
In a twist, CrediX then vanished by August 8th. Its website, X (formerly Twitter) account, and Telegram channel all went offline. This led to widespread suspicions of an exit scam, where the team may have taken off with the funds after appearing to ‘negotiate’ their return.
Impact: $4,500,000.00

NumaVault - 10/08/2025
Type: Protocol Logic
NumaVault, a smart contract-based DeFi protocol component (specifically a vault contract) was exploited on the Sonic blockchain when an attacker manipulated the vault and liquidated victim accounts. This then gave the attacker additional tokens they weren’t entitled to. They then swapped and moved funds across multiple pools, and eventually mixed the stolen funds, to confuse the trace of funds. Specifically, the attacker used Tornado Cash, a prominent mixer chosen by illicit actors to obscure fund flows.
Impact: $320,000.00
Odin.fun - 12/08/2025
Type: Liquidity manipulation
Odin.fun, a bitcoin-based memecoin launchpad and trading platform, suffered a significant hack when attackers exploited a vulnerability in its automated market maker (AMM) smart contract. By depositing worthless tokens like SATOSHI and ODINPEPE alongside BTC, they artificially inflated their value through overweighted deposits and self trading. This ultimately tricked the system into overvaluing the deposits made. This enabled them to withdraw the equivalent of $7 million in quick succession. After the founder confirmed the hack on his personal X account, the platform immediately froze operations and began investigations, warning the perpetrators that funds should be returned, and that some of the hackers had already been identified. Via X, the founder confirmed that after initial investigations it appeared that the malicious actors were ‘linked to groups in China.’
Impact: $7,000,000.00
Coinbase - 13/08/2025
Type: MEV composability Attack
In mid-August, Coinbase, a centralized cryptocurrency exchange experienced a drain of $300,000 form one of its corporate DEX wallets, after mistakenly approving all of its accrued tokens to the 0x Protocol swapper contract. This swapper, which is not intended to receive approvals and is known to allow arbitrary calls, was quickly exploited by MEV bots that drained the wallet of its funds. The issue stemmed from a misconfiguration in Coinbase’s wallet setup, but the company confirmed that no customer assets were affected. In response, CSO of Coinbase announced that they had revoked token allowances, migrated funds to a new corporate wallet, and thanked the community for assistance in flagging the vulnerability.
Impact: $300,000
BTCTurk - 14/08/2025
Type: Compromised Private Key
Also in mid-August, Turkish crypto exchange BtcTurk suffered an attack when it detected a large amount of assets moving from its hot wallets across multiple chains, including Ethereum, Avalanche and Arbitrum. The exchange stressed that most user assets remained safe in cold storage and confirmed that trading and Turkish Lira services were unaffected.
Impact: $48,000,000.00
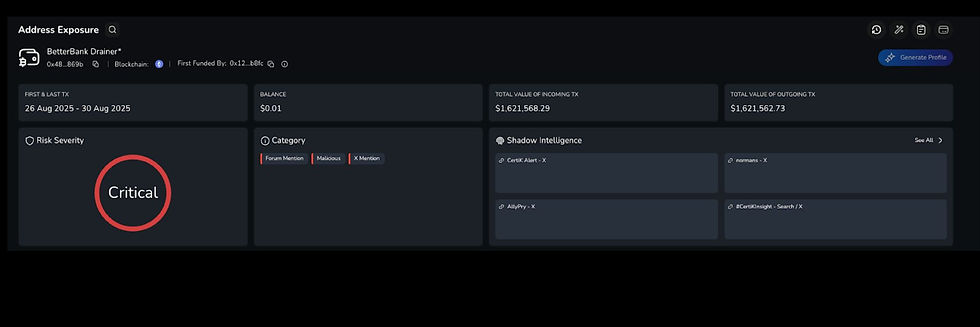
BetterBank - 26/08/2025
Type: Contract Vulnerability
BettterBank, a DeFi platform on PulseChain, was exploited via a flaw in its bonus-token contract that allowed an attacker to loop-mint unlimited Esteem and convert it into Favor tokens. The attacker drained pDai, PulseX and Pulise, and later swapped some for ETH. The protocol was paused within minutes, liquidity pools were drained to save assets, and BetterBank announced plans to relaunch with patched contracts, token airdrops, and debt recovery measures.
Impact: $5 million (~$2.7 million recovered)

Significant crypto events in August 2025
August 2025 was a turbulent month for the cryptocurrency sector, marked by unprecedented thefts, insider fraud and an extraordinary number of large scale phishing scams. Below are some of the most significant events that shaped the industry this month.
Largest ever Bitcoin theft revealed?
Chinese mining pool LuBian suffered a massive theft of 127,426 BTC in 2020. Equivalent to ~$3.5billion at the time, it is now worth ~$14.5 billion, and has gone undetected until now. This historic exploit was revealed five years later. The stolen funds had been steadily moved though exchanges and mixers, which ultimately were exposed. The breach has been attributed to weak private key generation, that may have allowed a brute-force attack, exposing security flaws in early mining infrastructure. This may potentially be the largest bitcoin theft ever recorded.
Lazarus Group revealed as Culprits
Mid August saw the report that the Lazarus Group was responsible for the theft of ~ $23 million in crypto assets from UK exchange Lykke. The breach was traced to a front-running exploit, a method where attackers insert trades ahead of legitimate ones, to profit unfairly. Nominis.io recently published an article observing Lazarus Groups’ behaviours, which is available to read here.
Insider Fraud
A former developer at Pump.fun, a Solana based meme coin launch platform, pleaded guilty to stealing $2 million in SOL after abusing privileged access. THis insider threat case underscores how even trusted team members can exploit their positions for personal gain, highlighting the importance of Know Your Employee (KYE) frameworks.
Social Engineering Attack
A high-net-worth Bitcoiner lost roughly $92 million in BTC after falling victim to a sophisticated social engineering scam. According to reliable blockchain investigator ZachXBT, the victim was tricked into authorizing fraudulent transfers, demonstrating that even the most security-aware holders can be compromised through targeted psychological manipulation.
Phishing Attacks
In August, an unusually high number of private crypto users fell victim to phishing attacks.
On August 6, a reputable crypto threat alerts group reported that the wallet at address 0x2d98….6695 was drained of 3.05 million USDT following a phishing attack. The victim was deceived into granting malicious approvals, leading to the immediate transfer of funds. As USDT is a stablecoin pegged 1:1 to the US dollar, the victim lost $3.05 million.
August 19th saw an unfortunately victim scammed approximately 783 BTC (worth about $91 million) after exchange and hardware wallet customer support were impersonated. According to reputable source ZachXBT, the ‘stolen funds began to peel off and deposits to Wasabi were made to the threat actor.’
Later in the month, on August 22, a user lost approximately $1 million in crypto and NFTs due to a phishing attack. The stolen assets included $ETH, $PORK, and $SPX. The victim signed phishing batch transactions that were disguised as Uniswap Swaps.
An additional user reportedly lost ~$1.54 million after falling victim to a phishing attack exploiting Ethereum’s EIP-7702 feature. The scam involved fraudulent batch transactions that included multiple token transfers and NFT approval operations. This event took place on 24th August.
The following day, a user lost 97 stETH valued at ~$465,802 after also falling for a victim scam. The user was apparently tricked into signing a malicious ‘permit’ signature, leading to the unauthorised transfer of their stETH holdings.
Many of these cases involved tricking users into authorizing transfers, suggesting a prevalence and increased uptake in spear phishing and phishing attacks. The total amount of assets lost to major private phishing attacks this month total a huge $97,095,802.

Website compromise
Puffer Finance, a liquid staking protocol, saw its official website and social media channels compromised by attackers. Users were warned not to interact with Puffer applications or linked, as the hijacked platform could direct them to malicious contracts.While funds weren’t immediately reported as lost, the event highlighted the reputational and security risks of platform-level compromises.
Whale movement
On 24th August, a significant Bitcoin whale sold ~24,00 BTC, approximately valued at $2.7 billion, causing Bitcoin’s price to plummet by about $4,000, to about $110.5k. Despite this massive sell-off, the entity still holds 152,874 BTC worth about $17 billion. The sudden market movement led to widespread liquidations, but analysts remain optimistic, noting that Bitcoin could rally once momentum clears and the price reclaims the $113.5-114k range.
Nominis Intelligence Team: Exclusive findings
August 2025 saw the discovery and flagging of approximately $7 billion worth of illicit crypto assets, reinforcing our position at the forefront of blockchain investigations. The scale of funds Nominis monitors, as well as the breadth of sources we draw from, ensures the quality of our database remains the most comprehensive in the industry.
This month, Nominis uncovered significant developments across some of the most active illicit marketplaces in Asia. Our monitoring of Cambodian based Huione Guarantee, the largest elicit marketplace operating on Telegram, revealed ongoing adaptation by its merchants. Despite frequent bans and takedowns, alternative marketplaces such as Xinbi, and likely successors of Huione such as Tudou Guarantee, continue to surface, demonstrating the resilience of these networks. Nominis continuously tracks these iterations, identifying how banned groups quickly reorganise under new names to preserve their operations and user bases, overcoming bans.
In parallel, our Head of Intelligence identified a Chinese Telegram group offering an alarming range of illicit services. Among its listings were date rape drugs marketed explicitely for drug-facilitated sexual assault, pinhole cameras likely intended for covert surveillance, and access to a hotel surveillance group that live-streams from hidden cameras in hotel rooms. The group also offers nationwide escort services. All these services are payable in USDT, underscoring the role of stablecoins in enabling these illicit economies. These findings highlight the disturbing intersection of technology, privacy invasion, and human exploitation on encrypted messaging platforms. To read more about the case, the first article covering the discoveries is available here.

Nominis CEO Snir Levi recently announced the release of new proprietary technology designed to identify wallet addresses based on descriptive data. This capability was recently applied in re-examining the infamous ‘Welcome to Video’ case, a child exploitation dark web market dismantled in 2018. By aligning on-chain activity with legal records, Nominis has been able to uncover thousands of wallets linked to abusive content purchases, reaffirming the importance of blockchain investigations in exposing long-running criminal ecosystems.
Another major development this month was the launch of CryptoSanctions.net, a free and open database consolidating all wallet addresses that appear on global sanctioned lists. Until now, investigators and compliance officers were forced to consult fragmented sources across multiple jurisdictions. With CryptoSanctions.net, Nominis has created a single reference point where sanctioned wallets can be easily searched and monitored. This initiative reflects the growing need for unified compliance tools in the crypto space, ensuring both law enforcement and financial institutions can act quickly to block sanctioned entities from moving funds.
Together, these findings and initiatives underscore Nominis’ mission to combine cutting edge intelligence, open-source resources and blockchain forensics to detect, disrupt and prevent crypto-enabled crime. From illicit marketplaces to sanctioned wallets, Nominis is uniquely effective in detecting emerging threats and identifying high risk wallets before they spread, unchecked.
Conclusion
August 2025 demonstrated the shifting balance of threats facing the crypto industry. While protocol exchange exploits amounted to a comparatively lower $65 million, less than half of July’s losses, phishing campaigns surged, draining over $97 million from individual wallets. This inversion underscores a new critical trend: attackers are increasingly targeting end-users as much as the infrastructure itself.
At the same time. Revelations of historic thefts, insider fraud, and illicit marketplace resilience highlight the long shadow of crypto-enabled crime. Yet, the rollout of new compliance tools, intelligence platforms, and investigative breakthroughs shows that defenders are also advancing.
The month’s events make one point clear: the crypto ecosystem is maturing under constant pressure. Both organisations and individuals must adapt, strengthen defenses, and remain vigilant to prevent August’s lessons from repeating at greater scale in the months ahead.
All research content and accompanying reports are provided for informational purposes only and should not be relied upon as professional advice. Accessing these materials does not create any professional relationship or duty of care. Readers are encouraged to consult appropriately qualified professionals for guidance. We uphold the highest standards of accuracy in all the information we provide. For any questions or feedback, please contact us at contact@nominis.io.


