July 2025 Crypto Attacks Monthly Report
- Nominis Intelligence Unit
- Aug 5
- 10 min read
Updated: Aug 7
July 2025 was marked by a series of high-profile security breaches across both centralized and decentralized crypto platforms. From sophisticated backend compromises to smart contract exploits and phishing attacks, the month exposed critical vulnerabilities in the digital asset ecosystem.
This crypto hacks report provides an overview of the major incidents, the methods used by attackers, and the financial impact of these events, offering insights into the evolving threat landscape and the urgent need for enhanced security and compliance measures.
July 2025 Major attacks
Future Protocol - 02/07/2025
Type: Business Logic Flaw
In early July, Future Protocol, a decentralized protocol on the BNB Chain, suffered an enormous exploit that took advantage of a fundamental design flaw in the FPC token’s tokenomics. The attacker used a flash loan to manipulate the FPC token’s price, then exploited the protocol’s automatic token burning mechanism which incorrectly reduced the liquidity pool’s token reserves. This broke the pricing calculations used by the automated market maker, allowing the attacker to extract far greater funds than should have been possible from a token swap. The incident demonstrates the risk of poorly designed tokenomics in DeFi protocols, and highlights the need for thorough security testing before deployment.
Impact: $4,600,000.00
RANT - 05/07/2025
Type: Business Logic Flaw
Also in early July, $RANT token, a DeFi token on the BNB Chain, experienced an exploit caused by a flaw in the _sellBurnLiquidityPairTokens() function. Instead of referencing the correct balance from the liquidity pool, the function mistakenly used amounts from user transfers. This allowed attackers to manipulate the token burn process and steal assets in the process.
Impact: $204,000.00
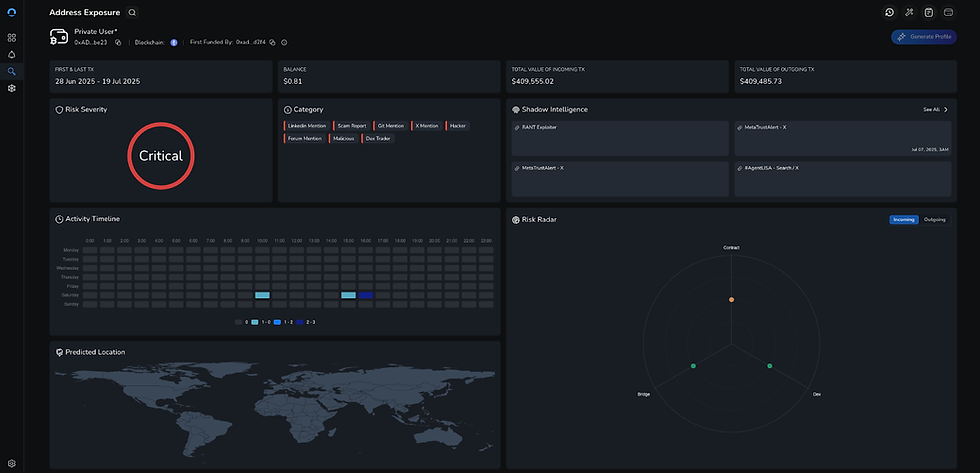
PeapodsFinance - 08/07/2025
Type: Vulnerable Price Dependency
Peapods Finance, a DeFi protocol that operates across multiple blockchains, experienced a hack when, according to Peapods’ X account, an attacker manipulated prices in a low volume, low liquidity Uniswap pools that were being used as TWAP (Time Weighted Average Price) oracles by some Pod markets.
The attacker exploited the fact that these oracle pools had deteriorated over time; they originally had over $1 million in liquidity when the Pods were created, but liquidity was later withdrawn, making the oracles vulnerable to price manipulation. By skewing prices in these weakened oracles, the attacker was able to borrow or liquidate positions at false values, draining funds. The exploit was possible due to Peapod’s reliance on user-selected oracles without proper safeguards or active monitoring of oracle quality.
While more than one wallet was involved in the exploitation of Peapods, Etherscan, the blockchain explorer tool specifically for the Ethereum blockchain, failed to tag one of the exploiting wallets as dangerous. This is accurate at the time of writing.
Meanwhile, automated transaction monitoring platform Nominis Vue recognised this address as one of the hacking wallets, and can offer relevant information on the wallet’s popular weekday according to weekday and hour, and predicted location of the wallet.
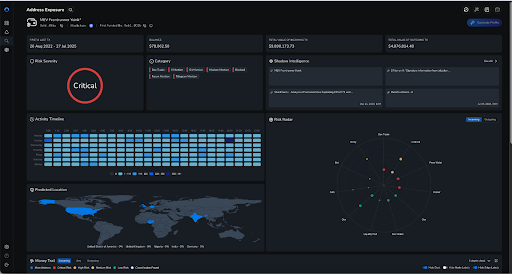
Impact: $230,000.00
Texture Finance- 09/07/2025
Type: Contract Vulnerability
Texture Finance, a Solana-based DeFi protocol, suffered a smart contract exploit in its USDC vault, when a missing ownership check allowed an attacker to provide their own token account, and as a result, had their account mistakenly filled with LP tokens, and redeemed these tokens for real liquidity. After discovering the hack, the protocol disabled withdrawals and auditors and engineering teams worked to patch the vulnerable contract.
Texture offered the hacker a 10% bounty, and in a rare ‘greyhat’ solution, the attacker returned 90% of the stolen USDC just before the deadline, claiming the bounty. In return, Texture agreed not to pursue legal steps.
Impact: $2.2 million (1.98 million returned)
GMX - 09/07/2025
Type: Reentrancy Attack
GMX v1, a decentralised exchange platform, suffered a major exploit resulting in huge loss when the attacker performed a reentrancy attack. The attacker, referred to by GMX in their post mortem as a ‘user’ took advantage of a re-entrancy vulnerability in the executeDecreaseOrder()function. By deploying a custom contract, they were able to repeatedly call this function before the protocol’s internal state was properly updated. This allowed them to artificially inflate key metrics such as the protocol’s global assets under management and the GLP token price, and ultimately withdraw more funds than they were entitled to.
GMX managed to recover most of the stolen funds after offering a $5 million ‘greyhat’ bounty, accepted by the attacker.
Impact: $42 million ($37 million recovered)
Kinto - 10/07/2025
Type: Contract Vulnerability
Kinto, an Ethereum Layer-2 network focused on compliant DeFi, suffered a major exploit involving its $K token deployed on Arbitrum. The attacker leveraged a critical ERC1967Proxy vulnerability that allowed them to insert a malicious proxy contract and mint unlimited $K tokens without detection, exploiting a bug in blockchain explorers that masked the attack. Kinto was unaware of the attack, and by the time the attacker began minting tokens and using them to drain liquidity from Morpho and Uniswap v4, it became too late to prevent the theft. The attacker stopped a sizable amount in ETH and USDC and crashed the $K’s token price. However, the core L2 network, bridge, and user wallets remained unaffected.
Impact: $1,550,000.00
Arcadia Finance - 15/07/2025
Type: Contract vulnerability
In mid-July, Arcadia Finance suffered a huge exploit after an attacker abused a vulnerability in its Asset Manager contracts, specifically the Rebalancer and Compounder modules. The attacker created Arcadia Accounts, exploited delegated permissions, and used Morpho flash loans to repay debts and trigger a malicious rebalance. By injecting custom call data and hijacking internal calls, the attacker accessed and drained funds from victim accounts while keeping them in a ‘healthy’ state to bypass failsafes. The exploit succeeded due to a design flaw that allowed the attacker to impersonate trust contracts. A previous trigger of the protocol’s circuit breaker had locked the system into an unpaused state due to Arcadia’s cooldown design, preventing decent defence when the actual exploit began. Arcadia confirmed in their post mortem that the lending and token contracts were not affected, and worked with white-hat partners and authorities to recover stolen funds.
Impact: $3,600,000.00
BigOne - 16/07/2025
Type: Supply Chain Attack
Also in mid-July, centralized exchange BigONE experienced a sophisticated supply chain attack that targeted its hot wallet infrastructure, resulting in an enormous heist of funds, including assets across BTC, ETH, USDT, SOL, DOGE, SHIB and others. Rather than compromising private keys directly, the attacker gained access to the platform’s backend production network, modified server-side business logic governing account operations and risk controls, and disabled withdrawal validations. This allowed unauthorized transfers without alerts, despite real-time system monitoring, spanning across different blockchains.
BigONE immediately suspended deposits, trading and all activity on the platform, and confirmed that private keys remained secure. The platform pledged to fully compensate all affected user balances, and resumed trading within a few hours alongside new additional security checks.
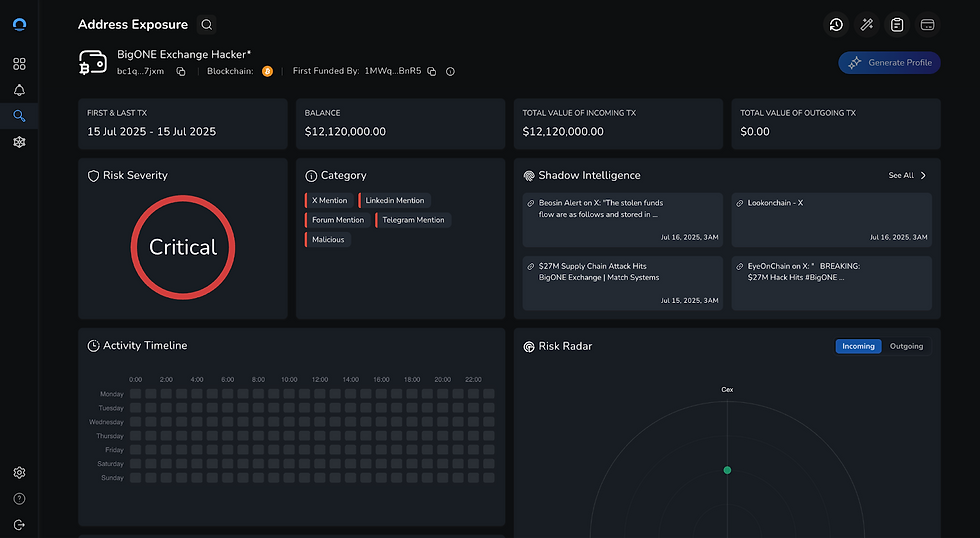
Impact: $27,000,000.00
CoinDCX - 19/07/2025
Type: Security Vulnerability
Mid July also saw the compromise of a liquidity providing operational account, at CoinDCX, draining it in minutes. The attacker exploited a permissions vulnerability within the internal systems, allowing unauthorized withdrawals. CoinDCX, a privately held Indian fintech and cryptocurrency company operates India’s leading crypto exchange platform, with over 10-15 million registered users. The compromise was recognised about half an hour after the breach, meaning it remained somewhat limited in scope and could not affect customer funds, according to their thread on X. Internal teams alongside external partners are working to trace and recover the stolen funds, and in the meantime, crypto withdrawals remain live, and customer funds remain in cold storage. Two days after the attack, CoinDCX announced a bounty program offering up to 25% of the recovered funds. According to some sources, this hack has been linked to the infamous Lazarus Group of North Korea, who regularly targets crypto exchanges.
Impact: $44,200,000.00
Trusta AI - 23/07/2025
Type: Liquidity pool exploit
Trusta Labs, a blockchain security and auditing firm, was involved in an external scam when an attacker created a fake version of their official $TA token. The attacker exploited a code flaw in a malicious, unverified smart contract (unassociated with TrustaLabs) which did not properly validate user input. This allowed the attacker to use WBNB tokens from any user who had authorised that malicious token. They then created a fake WBNB-$TA liquidity pool, and sold their own $TA tokens into that pool, draining WBNB from users without their permission. While Trusta’s own smart contracts and the $TA token remained secure and unaffected, the project team is encouraging all users to revoke permissions to the malicious contract immediately, and are offering a $200,000 buyback of $TA tokens to protect affected users.
Impact: $44,200,000.00
WOO X - 24/07/2025
Type: Phishing Attack
Towards the end of July, Woo X experienced unauthorized withdrawals totalling over $10 million from nine user accounts. The hacker appeared to target user-controlled accounts, rather than WOO X’s own wallets, and targeted assets on the BTC, ETH, ARB and BNB networks. According to WOO X’s X account, the exploit was the result of a phishing attack on a team member’s device, allowing the attacker access into the development environment. The exploiter was then able to coordinate withdrawals from the user accounts without interference from the security measures in place. The day after the attack, WOO X announced again via their X account that the ‘9 affected accounts had been credited from the company treasury’.
Impact: $14,000,000.00
SuperRare - 28/07/2025
Type: Contract Vulnerability
SuperRare, an NFT platform, was hacked by an attacker via a flawed smart contract on Ethereum. The exploit stemmed from a logical error in the updateMerkleRoot()function, which lacked proper authorisation checks, allowing anyone to update the contract state and drain its assets. The attacker’s wallet, funded via Tornado Cash about 6 months ago, executed the theft and does not appear to have moved or swapped the stolen tokens. Despite the large token quantity, the incident does not seem to have impacted NFT assets and only a single staking vault was affected.
Impact: $730,000.00
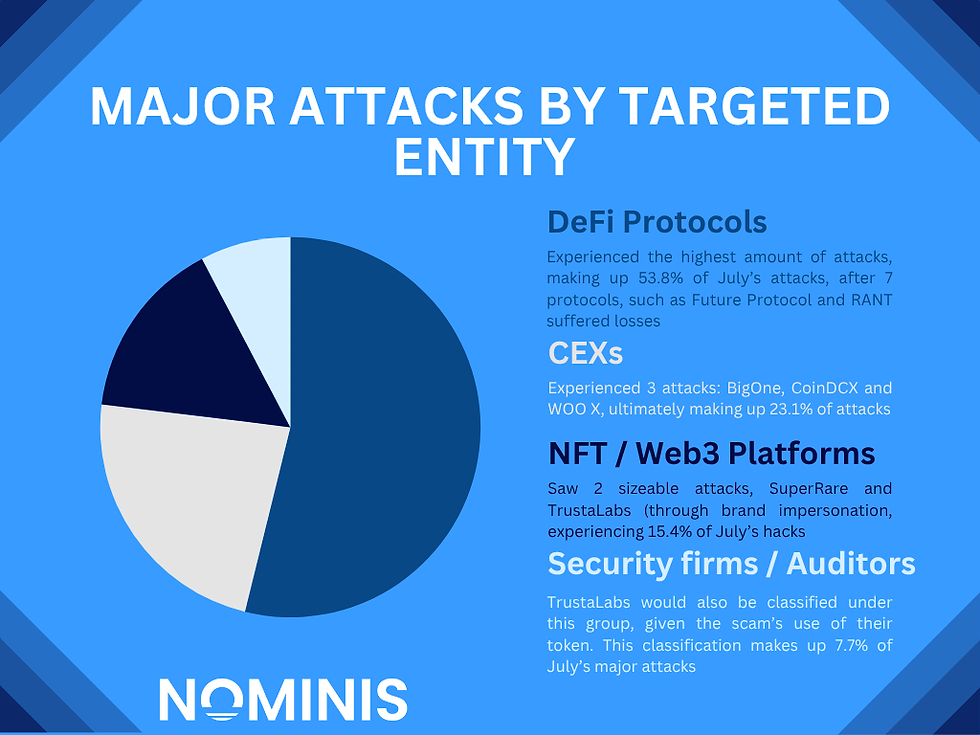
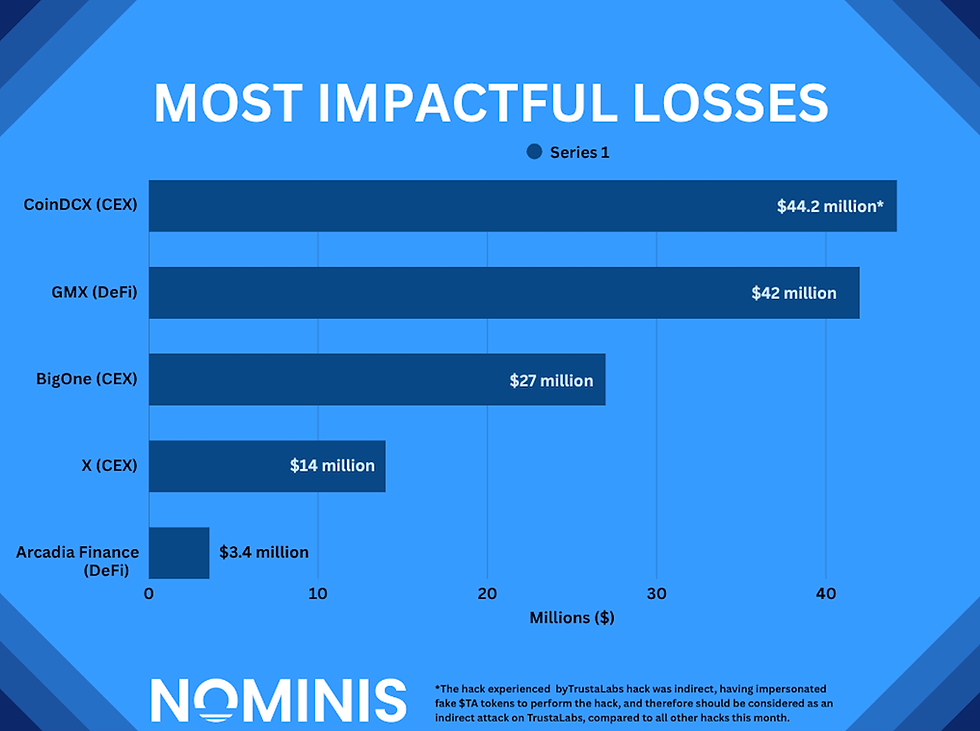
Significant events in July
This month saw a number of significant and newsworthy events, involving a variety of topics. These varied from the hacking of 6 Brazilian Banks via an inside job, to Satoshi-era dormant wallets suddenly reactivating, to high level law enforcement and regulatory actions from enforcers.
Security, Stability and Hacks:
In the realm of security, stability and hacks, July saw several interesting cases.
A hacker paid the equivalent of $2,770 US to an insider at C&M Software, gaining access to 6 Brazilian Banks’ reserve accounts and stealing approximately $140-148 million, with up to $40 million dollars laundered via crypto OTC channels.
Carbontec found a vulnerability in 1inch ‘s v4- v6 router’s rescueFunds function. This allowed unauthorized withdrawals of missent tokens, totally about $520,000 without detection.
Chris Larsen, co-founder of Ripple, moved about 50 million XRP - worth about $140-175 million to exchanges within several days, causing a ~14% price dip. Analysts warned he still holds ~ 2.8 billion XRP, raising concern over potential further sell-offs.
A sophisticated phishing operation impersonating Coinbase support was uncovered this month. Attackers used phone calls, fake Know Your Customer (KYC) requests, and spoofed email domains to bypass multi-factor authentication (MFA) and access user accounts. The scam used a fake KYC app and redirected users through deceptive customer service interactions, resulting in fund losses.
Whale Activity and On-Chain Movement:
Two significant events in July drew attention to whale wallets, both inactive since approximately 2011.
A satoshi-era wallet holding ~ 80,000 BTC, which approximately $8.6 billion, has been inactive since 2011 and was suddenly reactivated for what was presumably for a security upgrade, rather than a sale. Some speculate it was an address migration to Native SegWit, in an effort to future-proof their holdings, or upgrade their wallet software or infrastructure which could allow for easier key management or cold wallet integration, reducing risk.
A different, also long-time inactive wallet since about 2011 moved ~ $469.8 million in BTC, stirring speculation about profit-taking or strategic repositioning.
Regulatory Actions & Law Enforcement
On a positive note, regulatory bodies have made headlines this month with strategic efforts to ensure crypto crime is recognised and caught.
UK authorities, namely the FCA and the Metropolitan Police, seized 7 crypto ATMs across four London sites, and arrested two people suspected of running an unregistered crypto exchange linked to money laundering.
US enforcement agencies, specifically the DEA and FBI, seized over $10 million in cryptocurrency tied to the Sinaloa drug cartel during Miami raids, disrupting a key illicit money-laundering conduit.
Hungary has changed its Criminal Code to make private crypto trading on unlicensed exchanges illegal, imposing sentences of up to 5 years depending on the amount that is traded. Online bank Revolut suspended crypto services in Hungary immediately after the law took effect but later partially restored withdrawals. Deposits and new trading has been suspected until further regulatory clarity emerges. This change is among the most severe in Europe, diverging sharply from the EU’s MiCA standards which lean towards administrative fines rather than prison sentences.
The GENIUS Act, signed into law on July 18, 2025, establishes the first clear federal framework for fully dollar-backed stablecoins in the United States. Beyond regulating reserves and licensing, the Act has major implications for crypto compliance-especially KYT. With stablecoins now positioned as core financial infrastructure, issuers and platforms must implement real-time transaction monitoring, behavioral risk scoring, and robust AML safeguards.
Conclusion
July 2025 has been a particularly challenging month for the cryptocurrency ecosystem, with total losses from major attacks amounting to approximately $140.9 million. Centralized Exchanges (CEXs) continue to be the most prominent victims, accounting for the majority of funds stolen, and this concurs with broader industry findings suggesting that CEXs were consistently the most prominent victims in the first half of 2025. Their high liquidity, centralized infrastructure, and potential backend vulnerabilities or insider risks make them prime targets for attackers.
The exploitations methods observed this month ranged from internal permissions abuse and supply chain compromises to sophisticated phishing attacks targeting developer devices. Contract vulnerabilities and business logic flaws were the most frequent causes of successful exploits.
The first half of 2025 saw assets totalling approximately $2.17 billion, stolen to crypto hacks, with about 69% of these linked to CEXs. The largest included the unprecedented $1.49 billion Bybit hack.
Notably, the month also saw cases of ‘grey hat’ hacking, where attackers negotiated to return most of the stolen funds in exchange for keeping a bounty and avoiding prosecution. While these arrangements may mitigate losses, they raise concerns about the potential encouragement of future exploits by creating an implicit reward system for hackers.
Overall, July’s incidents underline the critical importance of continuous security vigilance , multi-layered defences, and proactive transaction monitoring within both centralised and decentralized crypto environments. As threat actors evolve their tactics, the industry must adopt robust compliance and investigative frameworks to protect assets, maintain user trust, and uphold the integrity of the blockchain ecosystem.
While we strive for accuracy in our content, we acknowledge that errors may occur. If you find any mistakes, please reach out to us at contact@nominis.io Your feedback is appreciated!


